Combatting Scams in Australia, Singapore, China and Hong Kong
Key Points:
Singapore’s Shared Responsibility Framework
Comparing scams regulation in Australia, Singapore and the UK
China’s Anti-Telecom and Online Fraud Law
Hong Kong’s Anti-Scam Consumer Protection Charter and Suspicious Account Alert Regime
The increased reliance on digital communication and online banking has created greater potential for digitally-enabled scams. If not appropriately addressed, scam losses may undermine confidence in digital systems, resulting in costs and inefficiencies across industries. In response to increasingly sophisticated scam activities, countries around the world have sought to develop and implement regulatory interventions to mitigate growing financial losses from digital fraud. So far in our scam series, we have explored the regulatory responses in Australia and the UK. In this publication, we take a look at the regulatory environments in Singapore, China and Hong Kong, and consider how they might inform Australia’s industry-specific codes.
SINGAPORE
Shared Responsibility Framework
In December 2024, Singapore’s Shared Responsibility Framework (SRF) came into force. The SRF, which is overseen by the Monetary Authority of Singapore (MAS) and Infocomm Media Development Authority (IMDA), seeks to preserve confidence in digital payments and banking systems by strengthening accountability of the banking and telecommunications sectors while emphasising individuals’ responsibility for vigilance against scams.
Types of Scams Covered
Unlike reforms in the UK and Australia, the SRF explicitly excludes scams involving authorised payments by the victim to the scammer. Rather, the SRF seeks to address phishing scams with a digital nexus. To fall within the scope of the SRF, the transaction must satisfy the following elements:
The scam must be perpetrated through the impersonation of a legitimate business or government entity;
The scammer (or impersonator) must use a digital messaging platform to obtain the account user’s credentials;
The account user must enter their credentials on a fabricated digital platform; and
The fraudulently obtained credentials must be used to perform transactions that the account user did not authorise.
Duties of Financial Institutions
The SRF imposes a range of obligations on financial institutions (FIs) in order to minimise customers’ exposure to scam losses in the event their account information is compromised. These obligations are detailed in table 1 below.
Table 1
Obligation
Description
12-hour cooling off period
Where an activity is deemed “high-risk”, FIs must impose a 12-hour cooling off period upon activation of a digital security token. During this period, no high-risk activities can be performed.
An activity is deemed to be “high-risk” if it might enable a scammer to quickly transfer a large sum of money to a third party without triggering a customer alert. Examples include:
Addition of new payee to the customer’s account;
Increasing transaction limits;
Disabling transaction notification alerts; and
Changing contact information.
Notifications for activation of digital security tokens
FIs must provide real-time notifications when a digital security token is activated or a high-risk activity occurs. When paired with the cooling off period, this obligation increases the likelihood that unauthorised account access is brought to the attention of the customer before funds can be stolen.
Outgoing transaction alerts
FIs must provide real-time alerts when outgoing transactions are made.
24/7 reporting channels with self-service kill switch
FIs must have in place 24/7 reporting channels which allow for the prompt reporting of unauthorised account access or use. This capability must include a self-service kill-switch enabling customers to block further mobile or online access to their account, thereby preventing further unauthorised transactions.
Duties of Telecommunications Providers
In addition to the obligations imposed on FIs, the SRF creates three duties for telecommunications service providers (TSPs). These duties are set out in table 2 below.
Table 2
Obligation
Description
Connect only with authorised alphanumeric senders
In order to safeguard customers against scams, any organisation wishing to send short message service (SMS) messages using an alphanumeric sender ID (ASID) must be registered and licensed. TSPs must block the sending of SMS messages using ASIDs if the sending organisation is not appropriately registered and licensed.
Block any message sent using an unauthorised ASID
Where the ASID is not registered, the TSP must prevent the message from reaching the intended recipient by blocking the sender.
Implement anti-scam filters
TSPs must implement anti-scam filters which scan each SMS for malicious elements. Where a malicious link is detected, the system must block the SMS to prevent it from reaching the intended recipient.
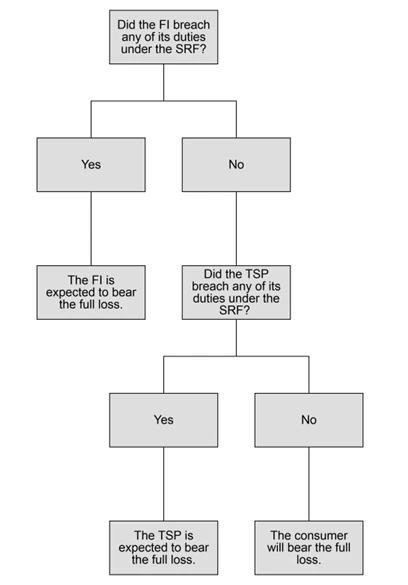
Responsibility Waterfall
Similar to the UK’s Reimbursement Rules explored in our second article, the SRF provides for the sharing of liability for scam losses. However, unlike the UK model, the SRF will only require an entity to reimburse the victim where there has been a breach of the SRF. The following flowchart outlines how the victim’s loss will be assigned.
HOW DOES THE SRF COMPARE TO THE MODELS IN AUSTRALIA AND THE UK?
Scam Coverage
The type of scams covered by Singapore’s SRF differ significantly to those covered by the Australian and UK models. In Australia and the UK, scams regulation targets situations in which customers have been deceived into authorising the transfer of money out of their account. In contrast, Singapore’s SRF expressly excludes any scam involving the authorised transfer of money. The SRF instead targets phishing scams where the perpetrator obtains personal details in order to gain unauthorised access to the victim’s funds.
Entities Captured
Australia’s Scams Prevention Framework (SPF) covers the widest range of sectors, imposing obligations on entities operating within the banking and telecommunications sectors as well as any digital platform service providers which offer social media, paid search engine advertising or direct messaging services. The explanatory materials note an intention to extend the application of the SPF to new sectors as the scams environment continues to evolve.
In contrast, the UK’s Reimbursement Rules only apply to payment service providers using the faster payments system with the added requirement that the victim or perpetrator’s account be held in the UK. Any account provided by a credit union, municipal bank or national savings bank will be outside the scope of the Reimbursement Rules.
Falling in-between these two models is Singapore’s SRF which applies to FIs and TSPs.
Liability for Losses
Once again, the extent to which financial institutions are held liable for failing to protect customers against scam losses in Singapore lies somewhere between the Australian and UK approaches. Similar to Singapore’s responsibility waterfall, a financial institution in Australia will be held accountable only if the institution has breached its obligations under the SPF. However, unlike the requirement to reimburse victims for losses in Singapore, Australia’s financial institutions will be held accountable through the imposition of administrative penalties. In contrast, the UK’s Reimbursement Rules provide for automatic financial liability for 100% of the customer’s scam losses, up to the maximum reimbursable amount, to be divided equally where two financial institutions are involved.
CHINA
Anti-Telecom and Online Fraud Law of the People’s Republic of China
China’s law on countering Telecommunications Network Fraud (TNF) requires TSPs, Banking FIs and internet service providers (ISPs) to establish internal mechanisms to prevent and control fraud risks. Entities failing to comply with their legal obligations may be fined the equivalent of up to approximately AU$1.05 million. In serious cases, business licences or operational permits may be suspended until an entity can demonstrate it has taken corrective action to ensure future compliance.
Scope
China’s anti-scam regulation defines TNF as the use of telecommunication network technology to take public or private property by fraud through remote and contactless methods. Accordingly, it extends to instances in which funds are transferred without the owner’s authorisation. To fall within the scope of China’s law, the fraud must be carried out in mainland China or externally by a citizen of mainland China, or target individuals in mainland China.
Obligations of Banking FIs
Banking FIs are required to implement risk management measures to prevent accounts being used for TNF. Appropriate policies and procedures may include:
Conducting due diligence on all new clients;
Identifying all beneficial owners of funds:
Requiring frequent verification of identity for high-risk accounts:
Delaying payment clearance for abnormal or suspicious transactions: and
Limiting or suspending operation of flagged accounts.
The People’s Bank of China and the State Council body are responsible for the oversight and management of Banking FIs. The anti-scams law provides for the creation of inter-institutional mechanisms for the sharing of risk information. All Banking FIs are required to provide information on new account openings as well as any indicators of risk identified when conducting initial client due diligence.
Obligations of TSPs and ISPs
TSPs and ISPs are similarly required to implement internal policies and procedures for risk prevention and control in order to prevent TNF. This includes an obligation to implement a true identity registration system for all telephone/internet users. Where a subscriber identity module (SIM) card or internet protocol (IP) address has been linked to fraud, TSPs/ISPs must take action to verify the identity of the owner of the SIM/IP address.
HONG KONG
Hong Kong lacks legislation which specifically deals with scams. However, a range of non-legal strategies have been adopted by the Hong Kong Monetary Authority (HKMA) in order to address the increasing threat of digital fraud.
Anti-Scam Consumer Protection Charter
The Anti-Scam Consumer Protection Charter (Charter) was developed in collaboration with the Hong Kong Association of Banks. The Charter aims to guard customers against digital fraud such as credit card scams by committing to take protective actions. All 23 of Hong Kong’s card issuing banks are participating institutions.
Under the Charter, participating institutions agree to:
Refrain from sending electronic messages containing embedded hyperlinks. This allows customers to easily identify that any such message is a scam.
Raise public awareness of common digital fraud.
Provide customers with appropriate channels to allow them to make enquiries for the purpose of verifying the authenticity of communications and training frontline staff to provide such support.
More recently, the Anti-Scam Consumer Protection Charter 2.0 was created to extend the commitments to businesses operating in a wider range of industries including:
Retail banking;
Insurance (including insurance broking);
Trustees approved under the Mandatory Provident Fund Scheme; and
Corporations licensed under the Securities and Futures Ordinance.
Suspicious Account Alerts
In cooperation with Hong Kong’s Police Force and the Association of Banks, the HKMA rolled out suspicious account alerts. Under this mechanism, customers have access to Scameter which is a downloadable scam and pitfall search engine. After downloading the Scameter application to their device, customers will receive real-time alerts of the fraud risk of:
Bank accounts prior to making an electronic funds transfer;
Phone numbers based on incoming calls; and
Websites upon launch of the site by the customer.
In addition to receiving real-time alerts, users can also manually search accounts, numbers or websites in order to determine the associated fraud risk.
Scameter is similar to Australia’s Scamwatch, which provides educational resources to assist individuals in protecting themselves against scams. Users can access information about different types of scams and how to avoid falling victim to these. Scamwatch also issues alerts about known scams and provides a platform for users to report scams they have come across.
KEY TAKEAWAYS
Domestic responses to the threat of scams appear to differ significantly. Legal approaches explored so far in this series target financial and telecommunications sectors, seeking to influence entities in these industries to adopt proactive measures to prevent, detect and respond to scams. While the UK aims to achieve this by placing the financial burden of scam losses on banks, China and Australia adopt a different approach by imposing penalties on entities failing to comply with their legal obligations. Singapore has opted for a blended approach whereby entities which have failed to comply with the legal obligations under the SRF will be required to reimburse customers who have fallen victim to a scam. However, where the entities involved have met their legal duties, the customer will continue to bear the loss.
Look out for our next article in our scams series.
The authors would like to thank graduate Tamsyn Sharpe for her contribution to this legal insight.
Who is Stacking the Chips: U.S. Commerce Department Launches Section 232 Investigation into Semiconductor Imports
On April 16, 2025, the Department of Commerce announced that it initiated an investigation on April 1, 2025, under Section 232 of the Trade Expansion Act, into imports of semiconductors, semiconductor manufacturing equipment (SME), and related products to evaluate how those imports may impact national security.
The investigation extends beyond standalone semiconductor components, reaching into the broader electronics supply chain. It includes finished products embedding semiconductors, such as smartphones, laptops, tablets, and similar devices. Based on the application of the Section 232 tariff on steel and aluminum derivatives, if any downstream products becomes covered by this Section 232 investigation, it is likely that importers will need to pay a duty for those finished products based on the value of the incorporated semiconductors.
The scope of the investigation also covers various elements critical to the semiconductor industry, including semiconductor substrates, bare wafers, legacy chips, leading-edge chips, microelectronics, and SME components.
The Department of Commerce is seeking public comments on several national security-related issues surrounding semiconductor imports:
Demand and Production Capacity: Evaluating current and projected U.S. demand for semiconductors and SME by product type and node size, and assessing domestic production capacity to meet this demand.
Foreign Dependence: Examining U.S. reliance on foreign sources for semiconductors and SMEs, and the impact of foreign subsidies or export restrictions. This also considers the risks associated with concentrated imports from a small number of foreign facilities.
Domestic Expansion: Exploring the feasibility of expanding domestic production to reduce dependence on imports. This includes assessing strategies to enhance U.S. industry competitiveness and evaluating whether additional trade measures, such as tariffs or quotas, may be necessary to safeguard national security.
The comment period is open for 21 days from publication, closing on May 7th, 2025. Interested parties may submit their written comments, data, analyses, or other relevant information through the Federal rulemaking portal at www.regulations.gov under docket ID BIS-2025-0021.
CONSORTIUM OF PRIVACY REGULATORS: Eight States Announce Bipartisan Consumer Privacy Initiative
Eight state regulators have announced a bipartisan initiative to coordinate the implementation and enforcement of their privacy laws. The Consortium of Privacy Regulators includes the California Privacy Protection Agency (“CPPA”) and state Attorneys General from California, Colorado, Connecticut, Delaware, Indiana, New Jersey, and Oregon.
According to an announcement on the CPPA’s website, the Consortium’s goals include facilitating discussions on privacy law and protecting consumer privacy across jurisdictions. The CPPA notes that although each state has its own consumer privacy law, they share certain fundamental features such as rights to access, delete, and stop the sale of personal information, and similar obligations on businesses to protect consumer data.
“We’re proud to collaborate with states across the country to advance consistent, streamlined enforcement of privacy protections to address real-world privacy harms. The Consortium reflects this shared commitment—now and for the future.” – Michael Macko, CPPA’s head of enforcement
The CPPA has been one of the most active state agencies in the privacy arena. While this new initiative certainly signals more enforcement actions on the horizon, an inter-state coordinated effort may lead to some amount of uniformity and predictability amidst a patchwork regulatory framework.
You can read the CPPA’s announcement here: State Regulators Form Bipartisan Consortium to Collaborate on Privacy Issues
This Week in 340B: April 8 – 14, 2025
Find this week’s updates on 340B litigation to help you stay in the know on how 340B cases are developing across the country. Each week we comb through the dockets of more than 50 340B cases to provide you with a quick summary of relevant updates from the prior week in this industry-shaping body of litigation.
Issues at Stake: Rebate Model; Contract Pharmacy
In five cases against the Health Resources and Services Administration (HRSA) related to rebate models:
In one case, amici filed an amicus brief in support of the government.
In one case, a plaintiff filed a brief in opposition to defendants’ cross motion for summary judgment and reply in support of summary judgment.
In four cases, intervenor defendants filed a reply brief in support of their cross motion for summary judgment.
In a case challenging a Utah law that would restrict manufacturers’ ability to restrict contract pharmacy arrangements, the plaintiffs filed a motion for a preliminary injunction.
In two appealed cases challenging a Louisiana law governing contract pharmacy arrangements, the defendant and intervenor-defendant filed their briefs.
In a case by a drug manufacturer challenging an Arkansas state law governing contract pharmacy arrangements, the drug manufacturer filed a motion to strike a declaration.
Two drug manufacturer filed four separate complaints to challenge four state laws restricting contract pharmacy arrangements.
Reuben Bank and Deepika Raj also contributed to this article.
CMS Spring Provider Enrollment Updates
Centers for Medicare & Medicaid Services (CMS) released several pieces of Medicare provider enrollment guidance this spring, both emphasizing current policy and requirements as well as providing guidance and clarification relating to provider enrollment practices and forms. In particular, CMS reminded Medicare providers of the sanctions associated with failure to disclose their “managing employees” and updated its sub-regulatory guidance to clarify that Medicare providers’ legal business name as reported to CMS must very closely match what is listed on its IRS and NPI documentation.
In its Medicare Learning Network newsletter released on April 3, 2025, CMS reiterated Medicare enrollment requirements for providers and suppliers to report managing employees or face enrollment deactivation. CMS specified that managing employees are “general managers, business managers, administrators, directors, or other individuals who exercise operational or managerial control or directly or indirectly conduct day-to-day operations.” Roles that typically qualify as “managing employees,” per CMS, are Chief Executive Officer, Chief Operating Officer, Chief Financial Officer, Compliance Officer, Regional Manager, Clinical Manager, Operations Manager, Care Coordination Manager, Location Manager, Administration Manager, Compliance Director and Clinical Director. This guidance is a reminder to providers and suppliers to ensure the appropriate individuals are listed on its enrollment records as well as to continue to update enrollment records as individuals holding managerial positions change within an organization.
CMS also recently updated the Medicare Program Integrity Manual, Chapter 10, through Transmittal 13062. The updates became effective April 11, 2025.
Of note, CMS made several clarifications related to legal business name matches between provider enrollment systems (i.e., NPPES and PECOS) and a provider or supplier’s IRS CP-575. CMS’s general rule is that the legal business name must match between the IRS CP-575 as well as NPPES/PECOS. Deviations in legal business names across these sources can cause issues for providers and suppliers, particularly when punctuation, special characters or common words are involved. CMS addresses these situations by providing flexibility specifying cases where a Medicare Administrative Contractor (MAC) may accept certain mismatches.
CMS permits the MAC to accept a legal business name mismatch between the CP575 and NPPES/PECOS if there is no more than one punctuation/character discrepancy between the legal business name as listed on the CP575 and NPPES/PECOS and if the MAC believes based on the data and documentation furnished on and with the application that the legal business name listed on the CP575 and NPPES/PECOS belong to the same provider.
CMS also clarifies its stance in instances where certain common words may be present on the CP-575 but not in PECOS/NPPES or vice versa (for example, “the”, “a”, “to”, “of”, “and”, “in”, “for”, “as”, “you” and “at”). CMS permits the MAC to accept a legal business name mismatch between the CP575 and NPPES/PECOS if there is no more than one discrepancy between the two LBNs involving any of these 10 words, and if the MAC believes based on the data and documentation furnished on and with the application that the legal business name listed on the CP575 and NPPES/PECOS belong to the same provider.
A provider may have one discrepancy involving punctuation/special characters and one involving a common word, but no more than one of either. A discrepancy involving a common word only applies to the 10 words above, however, the discrepancy can be between one of the common words and a non-common word (for example, “of” and “with”).
Additional updates included in the transmittal mainly involve clarifying requirements involving provider enrollment forms and approval letter templates. A summary of those updates can be found below.
CMS has included instructions clarifying that the account holder’s street address on the CMS 588 EFT Form can be the provider or supplier’s practice location address, correspondence address, special payment address or chain home office address for those providers reporting a chain home office on the CMS 855A.
CMS also provides guidance indicating an already-enrolled supplier is not required to submit a new CMS-460 if they are enrolling in another state or MAC jurisdiction. A copy of the already-enrolled supplier’s CMS-460 must be provided to the new contractor.
CMS has included additional language in its Part A/B Certified Provider and Supplier Approval Letter Templates clarifying that if the provider/supplier has elected to use a CMS approved accreditation organization (AO), the AO will conduct the survey and recommend approval to the State Agency to finalize certification.
New Section 232 Trade Investigation on Imports of Processed Critical Minerals and Their Derivative Products Could Result in Trade Actions Later This Year
On April 15, 2025, President Trump signed an Executive Order directing the Secretary of Commerce to initiate a new investigation under Section 232 of the Trade Expansion Act of 1962 (Section 232) on imports of processed critical minerals and their derivative products. The investigation will evaluate the impact of imports of these materials on U.S. national security and resilience and address vulnerabilities in supply chains, the economic impact of foreign market distortions and potential trade remedies to ensure a secure and sustainable domestic supply of these essential materials. This is the third such investigation initiated this month and the fifth of President Trump’s second term.
Processed critical minerals and their derivative products are key building blocks of the U.S. defense industrial base and integral to sectors ranging from transportation and energy to telecommunications and advanced manufacturing. The new Section 232 investigation will encompass the following “critical minerals,” “rare earth elements,” “processed critical minerals” and “derivative products”:
“Critical minerals” are those included in the “Critical Minerals List” published by the United States Geological Survey (USGS) pursuant to section 7002(c) of the Energy Act of 2020 (30 U.S.C. 1606)1, as well as uranium.
“Rare earth elements” means the 17 elements identified as rare earth elements by the Department of Energy (DOE) in the April 2020 publication titled “Critical Materials Rare Earths Supply Chain” 2 and also includes any additional elements that either the USGS or DOE determines in any subsequent official report or publication should be considered rare earth elements.
“Processed critical minerals” refers to critical minerals that have undergone the activities that occur after critical mineral ore is extracted from a mine up through its conversion into a metal, metal powder or a master alloy. These activities specifically occur beginning from the point at which ores are converted into oxide concentrates; separated into oxides; and converted into metals, metal powders and master alloys.
“Derivative products” includes all goods that incorporate processed critical minerals as inputs. These goods include semi-finished goods (such as semiconductor wafers, anodes and cathodes) as well as final products (such as permanent magnets, motors, electric vehicles, batteries, smartphones, microprocessors, radar systems, wind turbines and their components and advanced optical devices).
Section 232 requires the Secretary of Commerce to complete an investigation and submit a report to the President within 270 days of initiating any investigation. The report will detail risks and provide recommendations to strengthen domestic production, reduce dependence on foreign suppliers and enhance economic and national security.
The President then has up to 90 days to decide whether to concur with the report and take action. Action may include import tariffs, quotas or other measures as needed to address the threat.
Although this timeline provides for action in approximately one year, there is nothing preventing the Administration from moving more quickly to finalize a report or take action.
President Trump’s directive that Commerce investigate imports of critical minerals and their derivative products closely follows the initiation of Section 232 investigations on semiconductor and pharmaceutical imports earlier this month. Earlier this year, the President also issued executive orders directing Commerce to investigate imports of copper and lumber under this same provision, marking a continuation of the Trump Administration’s use of Section 232 as a preferred mechanism to bolster domestic production and reduce reliance on foreign suppliers. Prior actions on specific critical minerals and materials completed during President Trump’s first term resulted in either findings of no national security threat (vanadium) or trade actions other than tariffs, such as working groups and negotiations with allies to improve supply (uranium and titanium sponge).
[1] Aluminum, antimony, arsenic, barite, beryllium, bismuth, cerium, cesium, chromium, cobalt, dysprosium, erbium, europium, fluorspar, gadolinium, gallium, germanium, graphite, hafnium, holmium, indium, iridium, lanthanum, lithium, lutetium, magnesium, manganese, neodymium, nickel, niobium, palladium, platinum, praseodymium, rhodium, rubidium, ruthenium, samarium, scandium, tantalum, tellurium, terbium, thulium, tin, titanium, tungsten, vanadium, ytterbium, yttrium, zinc and zirconium.
[2] The lanthanide series (lanthanum, cerium, praseodymium, neodymium, promethium, samarium, europium, gadolinium, terbium, dysprosium, holmium, erbium, thulium, ytterbium and lutetium) as well as scandium and yttrium.
March 2025 Bounty Hunter Plaintiff Claims
California’s Proposition 65 (“Prop. 65”), the Safe Drinking Water and Toxic Enforcement Act of 1986, requires, among other things, sellers of products to provide a “clear and reasonable warning” if use of the product results in a knowing and intentional exposure to one of more than 900 different chemicals “known to the State of California” to cause cancer or reproductive toxicity, which are included on The Proposition 65 List. For additional background information, see the Special Focus article, California’s Proposition 65: A Regulatory Conundrum.
Because Prop. 65 permits enforcement of the law by private individuals (the so-called bounty hunter provision), this section of the statute has long been a source of significant claims and litigation in California. It has also gone a long way in helping to create a plaintiff’s bar that specializes in such lawsuits. This is because the statute allows recovery of attorney’s fees, in addition to the imposition of civil penalties as high as $2,500 per day per violation. Thus, the costs of litigation and settlement can be substantial.
In March of 2025, product manufacturers, distributors, and retailers were the targets of 283 new Notices of Violation (“Notices”), as well as 75 amended Notices, alleging a violation of Prop. 65 for failure to provide a warning for their products. This was based on the alleged presence of the following chemicals in these products. Noteworthy trends and categories from new Notices sent in March 2025 are excerpted and discussed below. A complete list of all new and amended Notices sent in March 2025 can be found on the California Attorney General’s website, located here: 60-Day Notice Search.
Food and Drug
Product Category
Notice(s)
Alleged Chemicals
Assorted Prepared Food and Snacks: Notices include sunflower seeds, granola, instant soup, chips, crackers, and energy bars
50Notices
Cadmium, Lead and Lead Compounds, Mercury and Mercury Compounds
Dietary Supplements: Notices include pea protein powder, protein shake blends, dietary fiber supplements, and cinnamon supplements
33Notices
Cadmium, Mercury and Mercury Compounds, Lead and Lead Compounds, Bisphenol A, Perfluorooctanoic Acid (PFOA), and Perfluorooctane Sulfonate (PFOS)
Fruits and Vegetables: Notices include pickled ginger, kale chips, and dried mango slices
12Notices
Lead and Lead Compounds
Seafood: Notices include shrimp, crab cakes, mussels, and anchovies
9Notices
Cadmium and Lead and Lead Compounds
Assorted Prepared Food and Snacks: Notices include coconut water, black beans, and plant-based chicken
5Notices
Bisphenol A (BPA)
Cannabinoid Products: Notices include gummies and coffee
5Notices
Delta-9-tetrahydrocannabinol
Seafood: Notices include anchovies, smoked clams, and sardines
5Notices
Perfluorononanoic acid (PFNA) and its salts, Perfluorooctanoic Acid (PFOA), and Perfluorooctane Sulfonate (PFOS)
Noodles, Pasta, and Grains: Notices include penne and gluten-free fusilli
4Notices
Lead and Cadmium
Spices and Sauces: Notices include mole, curry, and vegan Bolognese
4Notices
Lead and Lead Compound
Fruits and Vegetables: Notices include mushrooms and pineapple slices
2Notices
Bisphenol A (BPA)
Seafood: Notices include chunk light tuna
1Notice
Bisphenol A
Cosmetics and Personal Care
Product Category
Notice(s)
Alleged Chemicals
Personal Care Items: Notices include shower caps and body tape
6Notices
Perfluorooctanoic Acid (PFOA)
Personal Care Products: Notices include lotion, hair oil, and shave gel
6Notices
Diethanolamine
Personal Care Products: Notices include hair growth jelly
1Notice
Lead
Consumer Products
Product Category
Notice(s)
Alleged Chemicals
Glassware and Ceramics: Notices include serving dishes, mugs, bowls, and vases
34Notices
Lead
Plastic Pouches, Bags, and Accessories: Notices include clutches, toy baskets, travel cases, and cross-body bags
33Notices
Di(2-ethylhexyl)phthalate (DEHP), Diisononyl phthalate (DINP), and Di-n-butyl phthalate (DBP)
Clothing: Notices include jackets, hoodies, shoes, and shorts
15Notices
Di(2-ethylhexyl)phthalate (DEHP), Diisononyl phthalate (DINP), and Di-n-butyl phthalate (DBP)
Housewares: Notices include umbrellas, shower curtain liners, and washcloths
15Notices
Perfluorooctane Sulfonate (PFOS) and Perfluorooctanoic Acid (PFOA)
Housewares: Notices include tablecloths, corkscrews, and rope lights
11Notices
Di(2-ethylhexyl)phthalate (DEHP), Diisononyl phthalate (DINP) and Di-n-butyl phthalate (DBP)
Tools: Notices include first aid kits, clamps, valves, safety vests, and natural gas conversion kits
11Notices
Di(2-ethylhexyl)phthalate (DEHP), Diisononyl phthalate (DINP), and Lead
Gloves
4Notices
Chromium (hexavalent compounds)
Housewares: Notices include lunch bags, generator covers, and athletic tape
4Notices
Perfluorooctanoic Acid (PFOA)
Moth Balls
4Notices
Naphthalene and p-Dichlorobenzene
Housewares: Notices include canes, brass bells, and air fresheners
3Notices
Lead
Jackets
3Notices
Perfluorooctanoic Acid (PFOA)
Sports Equipment: Notices include jump ropes and hockey sticks
2Notices
Di(2-ethylhexyl)phthalate (DEHP)
Furniture Wax
1Notice
Toluene
There are numerous defenses to Prop. 65 claims and proactive measures that industry can take prior to receiving a Prop. 65 Notice in the first place. Keller and Heckman attorneys have extensive experience in defense of Prop. 65 claims and in all aspects of Prop. 65 compliance and risk management. We provide tailored Prop. 65 services to a wide range of industries, including food and beverage, cosmetics and personal care, consumer products, chemical products, e-vapor and tobacco products, household products, plastics and rubber, and retail distribution.
Powering Africa’s Digital Future: The Challenge of Energy for Data Center Development
As the global economy increasingly digitizes, the infrastructure supporting this shift must evolve accordingly. In Africa, where the demand for digital services is surging — fueled by mobile penetration, fintech innovation, and a young, connected population — the case for expanding data center capacity is clear. However, the continent’s potential is hindered by underdeveloped energy infrastructure, presenting a significant bottleneck.
Why Data Centers Matter
Data centers form the backbone of digital transformation, underpinning cloud storage, AI applications, e-commerce platforms, and digital government services. According to the International Energy Agency (IEA), global electricity consumption by data centers is projected to exceed 800 TWh by 2026, up from 460 TWh in 2022. A significant portion of this demand comes from generative AI and machine learning applications, which consume up to 10 times more energy than traditional searches.
Africa, despite being one of the fastest-growing regions for digital adoption, accounts for less than 1% of the world’s data center capacity. The Africa Data Centres Association estimates that the continent requires at least 1,000 MW of new capacity across 700 facilities to meet demand. Yet, meeting this need will depend not only on digital infrastructure investments but also on solving a persistent and costly energy challenge.
The Energy Challenge: Costs, Capacity, and Volatility
Data center development will play a pivotal role in ensuring digital sovereignty and fostering a resilient, domestically-driven digital economy in Africa.
Sub-Saharan Africa exemplifies both the promise and the challenges of this transformation. While demand for digital services is accelerating, access to reliable energy remains a major obstacle. Many countries across the region grapple with limited energy access, high electricity costs, and outdated infrastructure characterized by frequent outages and heavy reliance on imported fuel sources.
This interplay of costs and reliability poses significant challenges for energy-intensive data centers. According to recent industry analysis, energy supply has emerged as the single most critical issue facing digital infrastructure investors. As demand for electricity rises—driven by AI, cloud computing, and the digitization of public services—grid expansion is struggling to keep pace. As a result, securing reliable, affordable power is now a top strategic priority for data center developers and investors alike.
Despite these challenges, several sub-Saharan countries—including Côte d’Ivoire, Gabon, and Senegal—are making significant progress. While legacy grid issues persist, these countries are actively investing in renewable energy projects that could create the enabling environment needed for sustainable data center growth.
Côte d’Ivoire: In June 2023, the country launched its largest solar power plant in Boundiali, delivering 37.5 MWp of capacity with an expansion target of 83 MWp by 2025. This project aligns with Côte d’Ivoire’s national goal to source 45% of its electricity from renewable energy by 2030.
Senegal: The Taiba N’Diaye Wind Farm, commissioned in 2021, is West Africa’s largest wind energy project, with a total capacity of 158 MW. It plays a central role in Senegal’s broader strategy to diversify its energy mix and reduce dependence on imported fossil fuels.
Gabon: Though less frequently spotlighted, Gabon is actively positioning itself as a renewable energy leader in Central Africa. In 2021, the government launched a hydropower development strategy to boost clean energy capacity. Notably, the Kinguélé Aval Hydroelectric Project, co-financed by the African Development Bank and IFC, will add 35 MW of capacity upon completion and help stabilize electricity supply in the Estuaire province, home to Libreville—the capital and potential hub for digital infrastructure. Gabon has also attracted investment in solar hybrid systems for rural electrification, aiming to reduce diesel reliance and support the decentralization of energy access. These initiatives create a more stable power framework suitable for future data center deployment.
Lessons from Leading Data Center Markets
Morocco is emerging as a pivotal player in North Africa’s data center market, driven by international energy investments and its strategic position connecting Europe, Africa, and the Middle East. Major global tech companies, including Oracle, Microsoft, Google, and Amazon Web Services (AWS), are drawn to Morocco’s rapidly expanding digital economy and its modern infrastructure. The country is fostering a favorable environment for data center growth through government-backed initiatives that enhance ICT infrastructure, making Morocco an attractive destination for both local and international data center operators.
The country’s stability and investments in renewable energy further position it as a sustainable choice for data center operations. With projects like those from Africa Data Centres, Gulf Data Hub, and N-ONE Datacenters, Morocco’s growing data center ecosystem is poised to meet the increasing demand for cloud computing and data storage across North Africa and beyond. By 2028, Morocco is expected to be a key hub for digital services, offering world-class data center facilities.
Looking to other pioneers in the continent, countries like Kenya and South Africa offer valuable lessons. Kenya, rich in geothermal resources, has attracted significant investments such as a $1 billion geothermal-powered data center from Microsoft and G42. This clean, non-intermittent energy solution provides a reliable power source for data centers. Similarly, South Africa is leading solar integration, with projects like the 12 MW solar farm being developed by Africa Data Centres and Distributed Power Africa, designed to power critical centers like Johannesburg and Cape Town. Such initiatives showcase the potential for public-private partnerships to address challenges of grid unreliability and position Africa as a growing leader in sustainable data center infrastructure.
These examples underscore the importance of strategic planning, infrastructure investment, and the integration of renewable energy sources in building resilient, sustainable data centers.
Policy and Legal Implications
From a legal perspective, developing a data center project requires meticulous contractual structuring. Long-term Power Purchase Agreements (PPAs) and Behind-the-Meter (BtM) agreements introduce project-specific risks — notably, the risk that delays in one part of the project (either the power plant or the data center) could lead to disruptions. Legal advisors must anticipate and address potential regulatory challenges, grid permitting complexities, and the need for future-proofing clauses to safeguard the project’s viability.
A comprehensive review of existing legislation, identification of key obstacles, and potential time-consuming issues (such as securing land) are crucial steps in ensuring the project’s success. Moreover, structuring energy supply projects to support data center operations is fundamental for ensuring the project’s bankability.
Conclusion: A Call to Action
Africa stands at a crossroads: with the right investments in both digital and energy infrastructure, the continent could leapfrog into a new era of economic autonomy and technological resilience. However, if energy bottlenecks are not addressed head-on, Africa risks falling behind just as the world accelerates into a data-driven future.
The roadmap is clear: invest in renewables, embrace innovative models like BtM PPAs, partner across sectors, and establish clear regulatory frameworks. Energy is no longer a background concern for digital infrastructure investors — it is the cornerstone. Data center growth and power sector development must now proceed hand-in-hand.
For Africa, this is not just a technical challenge — it is a strategic imperative.
SCOTUS Ruling: Freezing $65 Million in Teacher Grants Amid DEI Controversy
On April 4, 2025, the United States Supreme Court granted an emergency application to vacate the First Circuit Court of Appeals’ March 10 temporary restraining order (TRO) in the case of Department of Education v. California. The TRO had previously required the federal government to reinstate approximately $65 million in grants earmarked for recruiting and training teachers, which were previously terminated due to certain diversity, equity and inclusion (DEI) training and initiatives included in the grants. The Supreme Court’s decision allows the Department of Education to withhold and halt funding for these grants, prompting significant implications for organizations that rely on these grants. While the opinion is limited only to several grants for teacher recruitment and training, it opens the door for government agencies to immediately freeze or terminate grant funding and gives grant recipients little or no recourse to access potentially critical funding until lengthy and expensive litigation is complete.
The Court’s 5-4 majority opinion stated that the government would be unable to claw back funds without immediate intervention and funds may be withheld until litigation is completed. The Court’s opinion effectively stays the TRO and allows the Department of Education to proceed with its plan to terminate grants under the Teacher Quality Partnership (TQP) and Supporting Effective Educator Development (SEED) programs while the matter is litigated.
Although temporary restraining orders are typically not appealable, the Court majority believed that appellate review was justified because the TRO more closely resembled a preliminary injunction, which is appealable. The Court also noted that the government was likely to succeed in showing that the District Court did not have the authority to order payments of money under the Administrative Procedure Act, which does not typically cover monetary claims. Additionally, the Court majority believed that the state respondents would not suffer irreparable harm while the TRO was stayed because they had the financial means to continue the programs and could recover any wrongly withheld funds through appropriate legal channels. In dissent, several justices criticized the majority decision because the Department of Education’s grant funding terminations contradicted clear congressional goals in disbursing grant funding to educational institutions and other objectives.
With this opinion, organizations will need to carefully weigh whether to pursue injunctive relief based on the scope and size of the grant versus the time, cost and likelihood of success associated with litigation. For smaller grants and/or smaller organizations, this opinion may limit the ability or desire to challenge an adverse agency action related to a grant.
This opinion also raises important questions about whether a court has the authority to require grant payments in an injunction. It opens the floodgates for other cases to be brought by the new administration, including previous attempts to cut Federal assistance funding and foreign aid. As tensions between federal courts and the executive branch over funding decisions rise, time will tell what role the judicial branch will have in shaping or impacting this Administration’s policies.
Executive Order Proposes Big Changes to Federal Procurement
The 2,000 page Federal Acquisition Regulation (the “FAR”) has guided and dictated federal procurement for more than forty years. Periodically, the FAR has been updated to make procurement more efficient and simpler. The Trump administration is now undertaking its own effort with the rollout of an executive order entitled “Restoring Common Sense to Federal Procurement.” It goes without saying that significant changes to the FAR will impact how federal contractors and their subcontractors do business with the federal government.
While changes to the FAR could take some time (though the Executive Order lays out an aggressive timeline, as discussed further below), some changes may come sooner through class deviations. Class deviations can be issued at any time without public comments and may have immediate effect.
What is Staying in the FAR?
The Executive Order provides that the only provisions that should be in the FAR are those required by statute or “or essential to sound procurement.” What falls in the latter category remains to be seen, but will probably be shaped by existing Administration priorities that have been signaled through already-released executive orders impacting procurement.
Recent previous efforts, such as the Section 809 Panel established by the 2016 National Defense Authorization Act (NDAA), proposed comprehensive changes to the FAR, many of which were not adopted because they required Acts of Congress. It remains to be seen how much of this effort will impact Congressionally-required FAR clauses (though the Executive Order seems to explicitly carve those out from consideration for removal).
Congressionally mandated FAR clauses include efforts to protect the supply chain (such as FAR 52.204-25 “Prohibition on Contracting for Certain Telecommunications and Video Surveillance Services or Equipment” implementing Section 889 of the 2019 NDAA) and domestic preferences (such as FAR 52.225-1 “Buy American-Supplies” implementing the Buy American Act). The origins of other familiar clauses are murkier – such as the ability of the Government to terminate for convenience (see 52.249-2), but will probably fall under a clause that is “essential to sound procurement.”
What is Next?
The Executive Order requires that “Federal Acquisition Regulatory Council (FAR Council), the heads of agencies, and appropriate senior acquisition and procurement officials from agencies” amend the FAR within 180 days to include only provisions that are required by statute “or that are otherwise necessary to support simplicity and usability, strengthen the efficacy of the procurement system, or protect economic or national security interests.” This will be a massive effort with far-reaching consequences.
Agency supplemental regulations will also be getting a closer look. As government contractors know well, the FAR overlays the entire regulatory system, but individual agencies are able to issue their own regulatory supplements so long as they do not contradict the FAR. See FAR 1.304(B)(2). Designated agency leads will work the FAR effort to identify and streamline agency-specific regulations. This includes, for example, the Defense Federal Acquisition Regulation Supplement, which is almost as lengthy as the FAR in its own right.
The Executive Order also contains a subset provision aimed at any regulatory clauses not required by statute. That provision suggests amending the FAR to subset those regulations unless specifically renewed by the FAR Council (or the individual regulations themselves). If this comes to fruition, contractors and their supply chains will have to pay close attention to a regulatory environment that will be more dynamic with significant changes coming more frequently as provisions are considered for renewal.
The Executive Order may have far-reaching impacts on companies, including retailers, supporting the nearly $1 trillion government marketplace. We will continue to monitor developments and provide updates when appropriate.
Illinois Amends ‘One Day Rest In Seven Act’ to Prohibit Employer Retaliation
Takeaways
The state’s “One Day Rest In Seven Act” now includes anti-retaliation provisions and an enforcement mechanism.
Employers should review their policies and practices and ensure they are compliant with the new law.
Related link
Illinois General Assembly – Full Text of Public Act 103-1082
Article
Recent amendments to the Illinois One Day Rest In Seven Act (ODRISA) prohibit employers from retaliating against employees and create an enforcement mechanism. The amendments went into effect March 21, 2025.
ODRISA requires employers to provide employees with at least 24 hours of rest in every “consecutive seven-day period.” It also requires meal periods of at least 20 minutes every 7.5 hours worked (and an additional 20-minute meal period for employees who work shifts of 12 hours or longer). Employers must also provide employees with reasonable restroom breaks.
Under the recent amendments, retaliation is prohibited against employees who have:
Exercised their rights under ODRISA;
Made ODRISA complaints to their employer or the Illinois Department of Labor (IDOL);
Instituted or are about to institute a proceeding under ODRISA; or
Testified or are about to testify in any investigation or proceeding under the Act.
820 ILCS 140/5.5.
An employee who believes their employer has violated ODRISA’s anti-retaliation provisions may file a claim with the IDOL and recover “all legal and equitable relief as may be appropriate.” 820 ILCS 140/7(b)(4).
The amendments also create an enforcement mechanism. The IDOL (represented by the Illinois attorney general) could assess penalties and fees and, ultimately, seek to enforce such penalties and fees by bringing a civil action “in any circuit court or in any administrative adjudicative proceeding under [the] Act.” 820 ILCS 140/7(d).
Employers should review their policies and practices and ensure they are compliant with the new ODRISA provisions.
USPTO Announces Changes to Patent Issue Timelines and Design Application Examinations
This week, the U.S. Patent and Trademark Office (USPTO) made two announcements of interest to patent holders and practitioners as part of modernization and efficiency efforts:
Suspension of Expedited Design Application Examinations—On April 14, 2025, the USPTO announced that it has suspended expedited examination of design applications starting April 17, 2025. This decision follows a 560 percent surge in requests for expedited examination in recent years, driven largely by fraudulent applications. The suspension aligns with the USPTO’s ongoing efforts to address issues such as erroneous micro entity certifications and to strengthen protections against threats to the intellectual property system.
Any request for expedited examination of a design application, including renewed requests, submitted on or after the effective date will not be approved. However, the USPTO will refund the associated fee for any request filed on or after this date.
Expedited Patent Issue Dates—Starting May 13, 2025, the USPTO will accelerate the timeline for patent Issue Dates. As part of the USPTO’s modernization efforts, the time between receiving an Issue Notification and the Issue Date will be reduced to roughly two weeks, down from the three-week average seen in recent years.
With this shortened timeframe, Applicants are reminded to file continuing applications before payment of issue fees to ensure copendency, per the Manual of Patent Examining Procedure (MPEP) 211.01(b), subsection I. For those applicants that do not participate in the e-Office Action program, patent issuance may occur before receipt of the Issue Notification.
Patent holders should be aware of these two changes for planning and scheduling purposes.