Weekly IRS Roundup December 23 – December 27, 2024
Check out our summary of significant Internal Revenue Service (IRS) guidance and relevant tax matters for the week of December 23, 2024 – December 27, 2024.
December 23, 2024: The IRS released Internal Revenue Bulletin 2024-52, which includes the following:
Treasury Decision 10015: These final regulations update the previous regulations under Section 48 of the Internal Revenue Code (Code), which provides for an investment tax credit for energy property (energy credit), and respond to changes made by the Inflation Reduction Act of 2022 (IRA).
The final regulations update the types of energy property eligible for the energy credit, including additional types of energy property added by the IRA; clarify the application of new credit transfer rules to recapture because of failure to satisfy the prevailing wage requirements, including notification requirements for eligible taxpayers; and include qualified interconnection costs in the basis of certain lower-output energy properties.
The final regulations also provide rules generally applicable to energy property, such as rules regarding functionally interdependent components, property that is an integral part of an energy property, application of the “80/20 rule” to retrofitted energy property, dual use property, ownership of components of an energy property, energy property that may be eligible for multiple federal income tax credits, and the election to treat qualified facilities eligible for the renewable electricity production credit under Code Section 45 as property eligible for the energy credit.
Notice 2024-82, which sets forth the 2024 Required Amendments List. The list applies to both individually designed plans under Code Section 401(a) and individually designed plans that satisfy the requirements of Code Section 403(b).
Notice 2024-86, which announces the extension of certain timeframes under the Employee Retirement Income Security Act of 1974 and the Code for group health plans; disability and other welfare plans; pension plans; and participants, beneficiaries, qualified beneficiaries, and claimants of these plans affected by Hurricane Helene, Tropical Storm Helene, or Hurricane Milton.
Revenue Procedure 2024-42, which updates the list of jurisdictions with which the United States has in effect a relevant information exchange agreement or an automatic exchange relationship under Treasury Regulation §§ 1.6049-4(b)(5) and 1.6049-8(a).
Announcement 2024-42, which provides a copy of the competent authority arrangement entered into by the competent authorities of the US and the Kingdom of Norway under paragraph 2 of Article 27 (Mutual Agreement Procedure) of the Convention between the US and Norway for the Avoidance of Double Taxation and the Prevention of Fiscal Evasion with respect to Taxes on Income and Property, signed on December 3, 1971.
The IRS issued a notice of proposed rulemaking, setting forth proposed regulations related to the definition of “qualified nonpersonal use vehicles.” Qualified nonpersonal use vehicles are excepted from the substantiation requirements that apply to certain listed property. The proposed regulations add unmarked vehicles used by firefighters or members of a rescue squad or ambulance crew as a new type of qualified nonpersonal use vehicle. The regulations affect governmental units that provide firefighter or rescue squad or ambulance crew member employees with unmarked qualified nonpersonal use vehicles and the employees who use those vehicles. Comments on the proposed regulations are due by March 3, 2025.
The IRS acquiesced to Green Rock LLC v. Internal Revenue Serv., 104 F.4th 220 (11th Cir. 2024). In that case, the US Court of Appeals for the Eleventh Circuit held that notices identifying certain conservation easement arrangements as reportable transactions are invalid under the Administrative Procedure Act because they failed to follow notice-and-comment rulemaking procedures.
December 23, 2024: The US Department of the Treasury and the IRS released final regulations regarding supervisory approval of penalties assessed pursuant to Code Section 6751(b). Section 6751(b) provides that no penalty “shall be assessed unless the initial determination of such assessment is personally approved (in writing) by the immediate supervisor of the individual making such determination….” The final regulations clarify the application of Section 6751(b) as to the timing of supervisory approval, the identities of the individual who first proposes the penalty and their supervisor, the requirement that the approval be “personally approved (in writing)” by the supervisor, and other aspects of the statute.
December 27, 2024: The IRS announced via Notice 2025-3 transitional relief with respect to the reporting of information and backup withholding on digital assets for digital asset brokers providing trading front-end services.
Transparency Is the Best Medicine: Device Parts Don’t Justify Orange Book Listing
The US Court of Appeals for the Federal Circuit affirmed a district court’s delisting of patents from the Orange Book because the patent claims did not “claim the drug that was approved” or the active ingredient of the drug that was approved. Teva Branded Pharmaceutical Products R&D, Inc., et al. v. Amneal Pharmaceuticals of New York, LLC, et al., Case No. 24-1936 (Fed. Cir. Dec. 20, 2024) (Prost, Taranto, Hughes, JJ.)
Teva owns the product that Amneal sought to delist, ProAir® HFA Inhalation Aerosol. The ProAir® HFA combines albuterol sulfate (the active ingredient) with a propellant and an inhaler device to administer the drug. Although the US Food and Drug Administration (FDA) approved Teva’s ProAir® HFA as a drug, the ProAir® HFA contains both drug and device components (the device components being the physical machinery of the inhaler). Teva lists nine nonexpired patents in the Orange Book for its ProAir® HFA.
Amneal filed an abbreviated new drug application (ANDA) seeking approval to market a generic version of the ProAir® HFA that uses the same active ingredient. Amneal asserted that it did not infringe Teva’s nine patents listed for the ProAir® HFA. Teva sued for infringement of six of those patents. Amneal filed counterclaims for antitrust and for a declaratory judgment of noninfringement and invalidity and sought an order requiring Teva to delist the five patents that it asserted against Amneal. Amneal moved for judgment on the pleadings on the ground that Teva improperly listed the asserted patents. The district court granted Amneal’s motion, concluding that Teva’s patents “do not claim the drug for which the applicant submitted the application.” The district court ordered Teva to delist its patents from the Orange Book. Teva appealed.
On appeal, Teva argued that a patent can be listed in the Orange Book if the claimed invention is found in any part of its new drug application (NDA) product. Teva argued that a patent “claims the drug” if the claim reads on the approved drug (i.e., if the NDA product infringes that claim). Teva also argued that according to the Federal Food, Drug, and Cosmetic Act’s broad definition of the word “drug,” any component of an article that can treat disease meets the statutory definition of a “drug.” With this interpretation, Teva’s patents “claim the drug” as the claim dose counter and canister components of the ProAir® HFA.
The Federal Circuit rejected Teva’s interpretation as overbroad because it would allow the “listing of far more patents than Congress has indicated.” The Court rejected Teva’s argument that a patent claiming any component of a drug is listable, explaining that Teva cannot list its patents just because they claim the dose counter and canister parts of the ProAir® HFA.
The Federal Circuit also rejected Teva’s argument that even if Teva’s statutory arguments were rejected, the Federal Circuit must remand the case to the district court to construe the claims. In doing so, the Court rejected Teva’s interpretation of the word “claims” in the listing and counterclaim/delisting provisions, explaining that the listing provision identifies “infringing” and “claiming” as two distinct requirements, and that to be listed, a patent must both claim the drug and be infringed by the NDA product.
The Federal Circuit explained that “infringing the claimed invention has several distinct features that differentiate it from claiming the invention.” In contrast to infringement, which is assessed by facts “out in the world,” claims require “examining the intrinsic meaning of the written patent document.” A product can infringe a patent “without meeting all of the claim elements” and often has additional features.
Teva further argued that a claim qualifies as claiming a drug “even if it only claims device parts.” The Federal Circuit rejected this contention, stating that “it is apparent that a product regulatable and approvable as a drug contains an active ingredient” and noting that “devices have a distinct approval pathway.” The presence of distinct drug and device pathways means that even if a product can simultaneously satisfy the linguistic elements of both, it can only be regulated as a drug or a device, and devices are “characterized more by their purely mechanical nature” (as was the case with Teva’s patents). The Court determined that the “active ingredient” ultimately classifies a drug or biological product, and not the “dosage form.”
Teva further argued that since the FDA designated ProAir® HFA as a combination product, the device components were statutorily a drug. In rejecting this contention, the Federal Circuit again noted the statutory focus on a drug’s active ingredient: an “approved drug” is “an active ingredient,” and to be listed it must meet several requirements, “including that it was identified in an NDA and that the FDA considered whether the active ingredient is safe and effective.” The Court concluded that “including a drug in a combination product does not transform each and every component of that combination product into a drug,” and that “a combination product does not become a drug just because it is regulated as a drug.”
Finally, Teva argued that its patents did claim an active ingredient since each patent has one claim that requires “an active drug.” The Federal Circuit explained that the FDA does not approve drugs based on “reference to some vague active ingredient in the abstract” and that the mere presence of those words was far too broad and would permit “any active ingredient in any form.”
Practice Note: In the slip opinion, at pp 4-12, the Federal Circuit delivers extraordinarily detailed treatise on FDA practice, NDA process, the Hatch-Waxman Act (ANDA practice), Paragraph IV certification, the delisting statute (21 U.S.C. § 355(j)(5)(C)(ii)(I)) and the Orange Book Transparency Act of 2020 (21 U.S.C. § 355(b)(1)(A)(viii)).
FDA Proposes New Rule on Testing Talc-Containing Cosmetic Products
Key Takeaways
What Happened: The Food and Drug Administration proposed a rule to require manufacturers of talc-containing cosmetic products to test their products for asbestos using specific testing methods.
Who’s Impacted: Manufacturers of talc-containing cosmetic products.
What Should You Do: Consider submitting comments on this proposed rule by March 27, 2025.
Mandatory testing of talc-containing cosmetic products is coming. At the end of December, the Food and Drug Administration (FDA) proposed a cosmetics rule and test method for asbestos in talc that was required under Section 3505 of the Modernization of Cosmetics Regulation Act of 2022 (MoCRA). 89 Fed. Reg. 105492 (Dec. 27, 2024). MoCRA added substantial new cosmetics provisions to the Federal Food, Drug, and Cosmetic Act (FFDCA), including a requirement for the FDA to establish and require the use of standardized testing methods for detecting and identifying asbestos in talc-containing cosmetic products. For more details on MoCRA, see here.
Talc is mined as naturally occurring hydrous magnesium silicate and is used in many cosmetic products to absorb moisture, prevent caking, render makeup opaque, or improve product texture. However, the rock types that host talc deposits often also contain asbestos, which is a known carcinogen when inhaled. As noted in the Environmental Protection Agency’s latest risk evaluation for asbestos (November 2024), “If vermiculite or talc are mined from ore that also contains asbestos fibers, it is possible that the resulting vermiculite or talc minerals are contaminated with asbestos fibers.” (EPA’s risk evaluation did not consider asbestos in talc for use in cosmetics.) FDA has repeatedly monitored for asbestos in talc-containing cosmetic products, and though it found none in the products sampled in 2010 and 2023, the agency detected asbestos in 9 of 52 products it tested in 2019.
As laboratories lacked standardized testing methods that can be followed without modification to test for asbestos in talc-containing cosmetic products, MoCRA required that FDA develop such methods. This proposed rule aims to standardize testing in the industry so that the public can rely on talc-containing cosmetic products without concerns of asbestos contamination. This standardization would apply to all manufacturers of talc-containing cosmetic products, including cosmetic products that are subject to the requirements of Chapter V of the FFDCA, such as cosmetic products that are also drugs.
Proposed Testing Requirements
The proposed rule would require manufacturers to test a representative sample of each batch or lot of a talc-containing cosmetic product for asbestos using both Polarized Light Microscopy (PLM) (with dispersion staining) and Transmission Electron Microscopy (TEM)/Energy Dispersive Spectroscopy (EDS)/Selected Area Electron Diffraction (SAED). FDA proposes defining “representative sample” as “a sample that consists of a number of units drawn based on rational criteria, such as random sampling, and intended to ensure that the sample accurately portrays the material being sampled.” This definition is intended to provide flexibility and to align with the definition of “representative sample” in other FDA-covered product areas.
Under the proposed rule, a sample would be deemed to contain asbestos if asbestos is detected at or above the applicable detection limit using either method. FDA has specifically requested comment on this issue.
Additionally, the proposed rule would require manufacturers to either test each batch or lot of the talc cosmetic ingredient or rely on a certificate of analysis for each batch or lot from a qualified talc supplier. If a manufacturer chooses to rely on a talc certificate of analysis, the manufacturer must annually qualify the supplier by verifying the reported asbestos test results based on their own testing or that of a third-party laboratory to establish the certificate’s reliability.
Recordkeeping
The proposed rule would require manufacturers to keep certain records to demonstrate compliance. Manufacturers would need to keep records of testing for asbestos that show test data, including raw data, and to describe in detail how samples were tested. If a manufacturer relies on a certificate of analysis from its talc supplier, records must include any certificate of analysis received from the supplier for testing of the talc used to make the finished product, and documentation of how the manufacturer qualified the supplier by as described above.
The proposed rule would also require that these records be made available to the FDA within one business day of a request from the agency. The records would need to either be in English or have an English translation available and would need to be retained for three years after the date that the record was created. FDA is specifically soliciting comment on the timeframe for retention. The agency wants to ensure the timeframe is sufficient given the timing from testing to when the product containing the tested talc makes it to consumers and the average length of time consumers keep or use the product.
Enforcement
FDA proposes to enforce the new rule’s requirements under the FFDCA’s prohibition on the sale or distribution of adulterated cosmetics products, 21 U.S.C. § 331(a). As there is no established safe level below which asbestos could not cause adverse health effects, FDA will consider asbestos at any level in talc-containing cosmetic products to be injurious to users. Therefore, the proposed rule would codify in regulations that if asbestos is present in a talc-containing cosmetic product, or if a manufacturer fails to test its talc-containing cosmetic or its talc ingredient for asbestos or to maintain records or such testing, that cosmetic is adulterated under the FFDCA and illegal to sell or distribute.
FDA proposes that this rule become effective 30 days after the date of publication of the final rule in the Federal Register. For those interested in commenting on the proposed rule, parties must should submit comments to the docket by March 27, 2025.
As noted, MoCRA requires FDA to publish a final rule on testing talc-containing cosmetic products. With a new administration soon to take office, it is unclear whether the Trump FDA will proceed to final rulemaking once the comment period ends or take other action.
US Surgeon General Advises on Link Between Alcohol and Cancer, Recommends Cancer Warnings on Alcohol Labels
On January 3, the US Surgeon General issued an advisory on the association between alcohol and the risk of cancer.
The advisory outlines current scientific literature and concludes that alcohol consumption is the third leading preventable cause of cancer in the United States. Among other things, the advisory recommends updating the “Government Warning” statement on alcohol beverage labels to warn consumers about the cancer risk.
Potential Changes to Mandatory Government Warning
Since 1988, federal law has required a “Government Warning” statement on every alcoholic beverage sold in the United States. Under existing law, the Government Warning must state that (1) pregnant women should not drink alcohol because of the risk of birth defects and (2) that alcohol may impair one’s ability to drive a car, operate machinery, and could cause health problems. It is also subject to strict formatting and placement requirements.
If enacted, the Surgeon General’s recommendation would require alcohol beverage suppliers to update the Government Warning statement for the first time since the statement became mandatory nearly four decades ago. Nonetheless, only Congress has the power to update existing federal law to require alcohol labels to warn of the risk of cancer. Therefore, alcohol beverage companies should continue to closely monitor congressional action for potential changes to the mandatory governmental warning.
Globally, the advisory notes that there are currently 47 countries that require alcohol warning labels related to health and safety. Of those, South Korea currently requires a cancer-specific warning, and Ireland will require the following cancer warning starting in 2026: “There is a direct link between alcohol and fatal cancers.”
Conclusion
While it would take an act of Congress to change the current mandatory Government Warning statement on alcohol beverage labels, the Surgeon General’s advisory is likely to increase scrutiny on the potential links between alcohol consumption and cancer risk. Additionally, this advisory may signal new regulatory requirements for alcohol beverage suppliers in the future.
Listen to this article
What Private Equity Investors and Real Estate Investment Trusts Need to Know About the Newly Enacted Massachusetts Health Oversight Law
On December 30, 2024, the Massachusetts state legislature passed House Bill 4653 (the Act), which significantly enhances regulatory oversight in the Massachusetts health care market. As signed into law by Governor Maura Healy on January 8, the Act will have profound effects for private equity (PE) investors and real estate investment trusts (REITs) engaging with the Massachusetts health care market. Passage of the Act comes on the heels of prominent PE-backed hospital failures in Massachusetts.
The Act Expands Existing Law and Government Infrastructure to Address Issues in Health Care Quality and Affordability
The Act overhauls the functions of, and increases coordination among, certain state agencies, including the Health Policy Commission (HPC), Department of Public Health (DPH), and the Center for Health Information and Analysis (CHIA). In addition, the Act expands the investigatory and enforcement powers of the Massachusetts Attorney General (MA AG) as it relates to health care activities, with particular attention to private equity investors, REITs, and management services organizations (MSOs). The Act does the following:
Increases HPC Oversight for PE Investors, REITs, and MSOs
The HPC is a Massachusetts government agency charged with monitoring health care cost trends and reviewing certain “material changes” to health care providers (e.g., proposed changes in ownership, sponsorship, or operations by health care providers). The Act broadens the scope of the HPC cost trend hearings to encompass a review of pharmaceutical manufacturers, pharmacy benefit managers (PBMs), PE investors, REITs, and MSOs. Additionally, Registered Provider Organizations (RPO) now must disclose ownership information about PE investors, REITs, and MSOs to HPC.
The bill amends the HPC Material Change Notification (MCN) process and now stipulates that the following activities are material changes for providers and provider organizations, in addition to certain mergers, affiliations, and acquisitions:
Significant expansions in capacity.
Transactions involving a significant equity investor which result in a change of ownership or control.
Significant transfers of assets, including, but not limited to, real estate sale leaseback arrangements.
Conversion from a non-profit to a for-profit organization.
In addition to expanding the scope of the MCN process, the Act allows the HPC to make and refer to the MA AG a report on certain proposed material change transactions, which creates a rebuttable presumption that the provider or provider organization has engaged in unfair or deceptive trade practices. Upon receipt of such a report, the MA AG is permitted to seek legal redress, including injunctive relief, and the proposed material change cannot be completed while that legal action remains pending.
Expands CHIA Oversight of PE Investors, REITs, and MSOs
CHIA is an existing Massachusetts government agency that is generally charged with improving transparency and equity in the health care delivery system. Significant among CHIA’s responsibilities is the collection, evaluation, and reporting of financial information from certain health care organizations. The Act expands CHIA’s oversight in the following ways:
As with the HPC, expands RPO reporting requirements to include PE investors, REITs, MSOs, and certain other entities.
Increases financial penalties for failure to make timely reports to CHIA.
Expands hospital financial information reporting and monitoring requirements as to relationships with significant equity investors, REITs, and MSOs.
Requires CHIA to notify HPC and DPH of failures to comply with reporting requirement which, in turn, will be considered by HPC and DPH in their review and oversight activities.
Increases DPH Oversight and Authority to Include Hospitals with PE Investor or REIT Relationships
The Act expands DPH health facility licensure and Determination of Need (DON) oversight and authority in a variety of ways:
Charges DPH with establishing licensure and practice standards for office-based surgical centers and urgent care centers.
Directs that the Board of Registration in Medicine be under the oversight of DPH in certain ways.
Amends the DON review process for projects, which will be guided by considerations that include the state health plan, the state’s cost-containment goals, impacts on patients and the community, and comments and relevant data from CHIA, HPC, and other state agencies. DPH may impose reasonable conditions on the DON as necessary to achieve specified objectives, including measures to address health care disparities to better align with community needs. The DPH may also consider special circumstances related to workforce, research, capacity, and cost. These special needs and circumstances may pertain to a lack of supply for a region, population, or service line as identified in the state health plan or focused assessments.
Prohibits DPH from granting or renewing a license for an acute care hospital if its main campus is leased from a REIT. However, any acute care hospital leasing its main campus from a REIT as of April 1, 2024, is exempt from this prohibition.
Prohibits DPH from granting or renewing a hospital license unless all documents related to any lease, master lease, sublease, license, or any other agreement for the use, occupancy, or utilization of the premises are disclosed to DPH.
Prohibits DPH from granting or renewing any hospital license unless the applicant is in compliance with all CHIA reporting requirements.
Permits DPH to seek an HPC analysis on the impact of a proposed hospital closure or discontinuation of services.
Expanded MA AG Authority Over PE Investors, REITs, and MSOs
In addition to the MA AG authority noted above in seeking to enjoin transactions that create concern for the HPC, the Act expands the MA AG’s investigatory powers pertaining to false claims to encompass document production, answering interrogatories, and providing testimony under oath by provider organizations, significant equity investors, health care REITs, and MSOs. Similarly, and significantly, the MA AG’s authority to seek civil monetary penalties for health care false claims act violations is expanded to include those parties that have an ownership or investment interest in a violating party.
Key Takeaways
The Massachusetts legislature aims to improve the quality and affordability of health care in the Commonwealth by increasing transparency of private investment in the health care market. The Act overhauls and increases coordination among state agencies like the HPC, DPH, and CHIA, and expands the investigatory and enforcement powers of the MA AG. For-profit investors and REITs must be aware of the following provisions of the Act to avoid civil penalties and state-sanctioned injunctions, and in planning for transactions and investments in Massachusetts:
Increased HPC Oversight: The HPC’s annual cost trend includes reviews of pharmaceutical manufacturers, PBMs, PE investors, REITs, and MSOs. New MCNs (significant expansions, equity investor transactions, asset transfers, and organizational conversions) must be reported to HPC in a timely manner.
Increased CHIA Oversight: CHIA’s scope of oversight for RPOs includes PE firms, REITs, and MSOs. The Act increases financial penalties for providers’ noncompliance and enhances hospital financial reporting. CHIA must inform HPC and DPH of providers’ reporting failures, which will influence HPC and DPH oversight activities.
Increased DPH Authority: DPH’s oversight now includes development and implementation of licensure standards for surgical and urgent care centers. DPH may not issue or renew licenses for acute care hospitals leasing their main campus from an REIT, subject to the April 1 exemption, or to a party not in compliance with CHIA reporting requirements. DPH also has increased authority to require information regarding leasing and other operational contracts prior to issuing a hospital license.
Increased MA AG Authority: The MA AG’s powers are expanded to include investigatory and enforcement actions against false claims involving PE investors, REITs, and MSOs.
Listen to this article
What to Know About the HHS HIPAA Security Standards Proposal
At the close of 2024, the Office for Civil Rights (OCR) at the U.S. Department of Health and Human Services (HHS) issued a Notice of Proposed Rulemaking (the Proposed Rule) to amend the Security Rule regulations established for protecting electronic health information under the Health Insurance Portability and Accountability Act of 1996 (HIPAA). The updated regulations would increase cybersecurity protection requirements for electronic protected health information (ePHI) maintained by covered entities and their business associates to combat rising cyber threats in the health care industry.
The Proposed Rule seeks to strengthen the HIPAA Security Rule requirements in various ways, including:
Removing the “addressable” standard for security safeguard implementation specifications and making all implementation specifications “required.”
This, in turn, will require written documentation of all Security Rule policies and encryption of all ePHI, except in narrow circumstances.
Requiring the development or revision of technology asset inventories and network maps to illustrate the movement of ePHI throughout electronic information system(s) on an ongoing basis, to be addressed not less than annually and in response to updates to an entity’s environment or operations potentially affecting ePHI.
Setting forth specific requirements for conducting a risk analysis, including identifying all reasonably anticipated threats to the confidentiality, integrity, and availability of ePHI, identifying potential vulnerabilities, and assigning a risk level for each threat and vulnerability identified.
Requiring prompt notification (within 24 hours) to other healthcare providers or business associates with access to an entity’s systems of a change or termination of a workforce member’s access to ePHI; in other words, entities will now be obligated to immediately communicate changes if an employee’s or contractor’s access to patient data is altered or revoked to mitigate the risk of unauthorized access to ePHI.
Establishing written procedures on how the entity will restore the loss of relevant electronic information systems and data within 72 hours.
Testing and revising written security incident response plans.
Requiring encryption of ePHI at rest and in transit.
Requiring specific security safeguards on workstations with access to ePHI and/or storage of ePHI, including anti-malware software, removal of extraneous software from ePHI systems, and disabling network ports pursuant to the entity’s risk analysis.
Requiring the use of multi-factor authentication (with limited exceptions).
Requiring vulnerability scanning at least every six (6) months and penetration testing at least once every year.
Requiring network segmentation.
The Proposed Rule notably includes some requirements specific to business associates only. These include a proposed new requirement for business associates to notify covered entities (and subcontractors to notify business associates) within 24 hours of activating their contingency plans. Business associates would also be required to verify, at least once a year, to their covered entity customers that the business associate has deployed the required technical safeguards to protect ePHI. This must be conducted by a subject matter expert who provides a written analysis of the business associate’s relevant electronic information systems and a written certification that the analysis has been performed and is accurate.
The Proposed Rule even includes a specific requirement for group health plans, requiring such plans to include in their plan documents requirements for their group health plan sponsors to comply with the administrative, physical, and technical safeguards of the Security Rule, requiring any agent to whom they provide ePHI to implement the administrative, physical, and technical safeguards of the Security Rule; and notify their group health plans no more than 24 hours after activation of their contingency plans.
Ultimately, the Proposed Rule seeks to implement a comprehensive update of mandated security protections and protocols for covered entities and business associates, reflecting the significant changes in health care technology and cybersecurity in recent years. The Proposed Rule’s changes are also a tacit acknowledgment that current Security Rule standards have not kept up with threats or operational changes.
The government is soliciting comments on the Proposed Rule, and all public comments are due by March 7, 2025. Given the scope of the proposed changes and the heightened obligations for all individuals and entities subject to HIPAA, there will likely be many comments from various stakeholders. We will continue to follow the Proposed Rule and reactions thereto. The Proposed Rule is available here.
HUD’s Proposed ORCA Program – A New Option for Earlier Mortgagee Reimbursement
On December 19, 2024, the Fair Housing Administration (FHA) and the U.S. Department of Housing and Urban Development (HUD) published a draft Mortgagee Letter proposing a new Optional Reimbursement Claim Alternative (ORCA) program. ORCA is intended to allow mortgagees to seek reimbursement for property tax and insurance payments the mortgagee advances on behalf of forward mortgage borrowers before the final claim payment.
Overview of ORCA
As outlined in the draft Mortgagee Letter, ORCA enables mortgagees to file early claims for reimbursement of advances made toward property taxes, hazard insurance, and flood insurance on defaulted forward mortgages. Currently, these costs are reimbursed only after the final resolution of a claim to HUD, meaning mortgagees are required to incur significant upfront costs for an uncertain period of time. The draft Mortgagee Letter recognizes that in the current higher interest rate environment these upfront costs are potentially exacerbating mortgagee liquidity issues.
If enacted, ORCA will allow mortgagees to make multiple claims during a single default episode. The term “single default episode” is not defined, but given FHA’s definition of “default,” a “single default episode” would likely encompass the period in which a borrower is at least 30 days delinquent under the mortgage until the borrower cures the delinquency. For a single default episode, mortgagees can claim up to 48 months of payments for eligible expenses, provided they meet the following eligibility requirements:
All property taxes and insurance obligations are paid before the due date;
The escrow funds intended for these expenses “were exhausted and were inadequate to meet these obligations;”
The delinquency/default code accurately reflects that the relevant mortgage has been in default for at least six months; and
The maximum allowable ORCA claims have not already been filed for a particular default.
In addition to the eligibility requirements above, mortgagees should be aware that initial ORCA claims can be submitted six months from the initial date of default, with subsequent claims allowed “no less than six months from the date the previous ORCA was filed.” Additionally, mortgagees will be required to maintain copies of all ORCA claims, as well as detailed servicing and transaction histories supporting the amounts claimed. Mortgagees should be sure to review the draft Mortgagee Letter to get a better understanding of the detailed proposed changes to the FHA Single Family Housing Policy Handbook related to the implementation of the ORCA program.
Takeaways
ORCA appears to offer mortgagees a positive new avenue for FHA claims that will likely ease liquidity pressures during the mortgage servicing process. By facilitating earlier reimbursement, HUD seems to recognize the need to mitigate the financial burdens mortgagees face and better position them to effectively service FHA mortgages. In light of the potential impact ORCA could have, we encourage mortgagees and other industry participants to review the draft Mortgagee Letter announcement and to provide feedback by the response deadline of March 3, 2025.
Listen to this post
5 Trends to Watch: 2025 U.S. Data Privacy & Cybersecurity
Even More States Join the Party — By the end of 2024, almost half of all U.S. states had enacted modern data privacy legislation. That trend will likely continue, particularly since a national data privacy statute may not be a top priority for the incoming administration.
It’s Time for State Enforcement — Several states have begun “staffing up” with the goal of bringing more data privacy enforcement in 2025, and some no longer have mandatory cure periods. Putting aside California, early indications are that Texas and Connecticut may take the lead among the states in enforcement activity.
It’s All About the Servers — Advertising technology’s transition from browser-side tracking technologies (cookies) to server-side tracking technologies (application programming interfaces or APIs) slowed in 2024. Nonetheless, the transition to server-side technologies continues; we may see it become the dominant medium for tracking in 2025 as organizations continue to work on aligning their digital advertising practices with applicable privacy laws.
Sensitive Data Is Everywhere — Regulators and plaintiffs continue to focus their attention on the collection, use, and sharing of sensitive data types. That trend is expected to continue in 2025 with continued focus on companies that use or share geolocation or health information.
Focus on Data Protection Impact Assessments (DPIAs) — The first states started requiring DPIAs two years ago, but regulators were reticent to demand that companies produce them. That has changed—state regulators have started requesting them and will continue requesting that companies produce DPIAs for data-processing activities that mandate them, like targeted advertising.
DOJ Finalizes Rule Implementing EO 14117, Establishing New National Security Cross-Border Data Regulatory Regime
On December 27, 2024, the U.S. Department of Justice (“DOJ”) issued a final rule (“Final Rule”) implementing Executive Order 14117 (Preventing Access to Americans’ Bulk Sensitive Personal Data and United States Government-Related Data by Countries of Concern) (“EO 14117”), which was published in the Federal Register on January 8, 2025. The Rule will go into effect on April 8, 2025, with the exception of certain due diligence, audit and reporting obligations that will become effective on October 5, 2025. The program is intended to address the threat of foreign powers and state-sponsored threat actors using Americans’ sensitive personal data for malicious purposes, including intelligence collection, cyber attacks, repression and intimidation, and economic espionage.
The substance of the Final Rule is largely similar to the Notice of Proposed Rulemaking, which we covered in our previous post. As discussed in that post, the Final Rule establishes a new regulatory regime that either prohibits or restricts “covered data transactions,” which are certain transactions―namely, data brokerage, employment agreements, investment agreements and vendor agreements―that could result in access to bulk U.S. sensitive personal data or government-related data (1) by a “country of concern” (i.e., China, Cuba, Iran, North Korea, Russia and Venezuela) or (2) a “covered person.” The term “covered persons” is defined broadly to include, for example, entities with 50% or more ownership by a country of concern, entities that are organized or chartered under the laws of, or have their principal place of business in, a country of concern, and a foreign person that is an employee or contractor of an entity described above or a primary resident of a country of concern.
The two general categories of data regulated by the Final Rule are defined as follows:
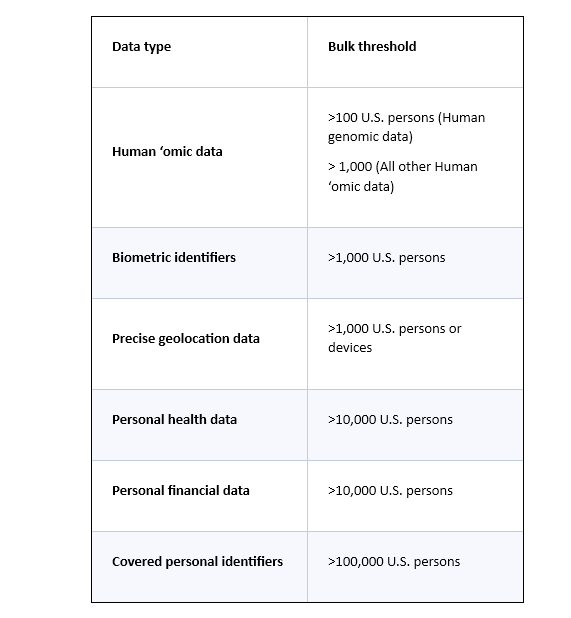
“U.S. sensitive personal data” means precise geolocation data, biometric identifiers, human ‘omic data, personal health data, personal financial data, certain “covered personal identifiers” (i.e., certain combinations of “listed identifiers,” such as government-issued identification numbers, device-based or hardware-based identifier, demographic or contact data, and advertising identifier), or any combination thereof.
The Rule applies only to certain “bulk” thresholds of U.S. sensitive personal data, and those thresholds differ depending on the type of U.S. sensitive personal data at issue. For example, for precise geolocation data, the Rule applies if a covered data transaction results in access to such information of over 1,000 U.S. persons or devices by a country of concern or covered person. In contrast, for personal financial data or personal health data, the threshold is higher (i.e., more than 10,000 U.S. persons). The table below provides the relevant “bulk” threshold for category of U.S. sensitive personal data.
“Government-related data” means any precise geolocation data, regardless of volume, for any location within any area enumerated on the “Government-Related Location Data List” or any sensitive personal data, regardless of volume, that a transacting party markets as linked or linkable to current or recent former U.S. government employees or contractors, or former U.S. government senior officials.
The Rule prohibits U.S. persons from engaging in certain types of covered data transactions, most importantly, covered data transactions involving (1) data brokerage or (2) bulk human ’omic data. All other covered data transactions are “restricted,” meaning that U.S. persons must comply with certain compliance requirements before engaging in such transactions, including cybersecurity requirements published on January 8, 2025, by the Cybersecurity and Infrastructure Security Agency, data compliance program requirements, annual audits and recordkeeping requirements.
As noted above, the DOJ largely declined to make significant revisions to the preliminary version of the Rule in response to input received during the recent notice and comment period. That said, the Final Rule does include certain clarifying changes and provide additional commentary. For example, the DOJ made adjustments to certain key definitions, clarified that the Final Rule applies prospectively to transactions engaged on or after the effective date, even if the underlying agreements existed prior to the rule, and added three types of human ‘omic data to the definition of U.S. sensitive personal data (the preliminary version of the Rule already covered genomic data).
The DOJ plans to release further guidance on the Final Rule, engage with industry and other stakeholders as the program goes into effect, and publish information related to voluntary self-disclosure, advisory opinions and approval processes for otherwise prohibited or restricted transactions. In the meantime, companies should assess their readiness for the rapidly approaching enforcement date in April.
Legislative Update: 119th Congress Outlook on AI Policy
House Looks To Rep. Obernolte to Take Lead on AI
Representative Jay Obernolte (R-Calif.) has emerged as a pivotal figure in shaping the United States’ legislative response to artificial intelligence (AI). With a rare combination of technical expertise and political acumen, Obernolte’s leadership is poised to influence how Congress navigates both the opportunities and risks associated with AI technologies.
AI Expertise and Early Influence
Obernolte’s extensive background in AI distinguishes him among his congressional peers. Holding a graduate degree in AI and decades of experience as a technology entrepreneur, he brings firsthand knowledge to the legislative arena.
As the chair of a bipartisan House AI task force, Obernolte spearheaded the creation of a comprehensive roadmap addressing AI’s societal, economic, and national security implications. The collaborative environment he fostered, eschewing traditional seniority-based hierarchies, encouraged open dialogue and thoughtful debate among members. Co-chair Rep. Ted Lieu (D-Calif.) and other task force participants praised Obernolte’s inclusive approach to consensus building.
Legislative Priorities and Policy Recommendations
Obernolte’s leadership produced a robust policy framework encompassing:
Expanding AI Resource Accessibility: Advocating for broader access to AI tools for academic researchers and entrepreneurs to prevent monopolization of research by private companies.
Combatting Deepfake Harms: Supporting legislative efforts to address non-consensual explicit deepfakes, a growing issue affecting young people nationwide. Notably, he backed H.R. 5077 and H.R. 7569, which are expected to resurface in the 119th Congress.
Balancing Regulation and Innovation: Striving to create a regulatory environment that protects the public while fostering AI innovation.
National Data Privacy Standards: Advocating for comprehensive data privacy legislation to safeguard consumer information.
Advancing Quantum Computing: Supporting initiatives to enhance quantum technology development.
Maintaining Bipartisanship
Obernolte emphasizes the importance of bipartisan collaboration, a principle he upholds through relationship-building initiatives, including informal gatherings with task force members. His bipartisan approach is vital in developing durable AI regulations that endure beyond shifting political majorities. Speaker Mike Johnson (R-La.) recognized Obernolte’s ability to bridge divides, entrusting him with the leadership role.
Obernolte acknowledges the difficulty of balancing immediate GOP priorities, such as confirming Cabinet appointments and advancing tax reform, with the urgent need for AI governance. His strategy involves convincing leadership that AI policy proposals are well-reasoned and broadly supported.
Senate Republicans 119th Roadmap on AI
As the 119th Congress convenes under Republican leadership, Senate Republicans are expected to approach artificial intelligence (AI) legislation with a focus on fostering innovation while exercising caution regarding regulatory measures. This perspective aligns with the broader GOP emphasis on minimal government intervention in technology sectors.
Legislative Landscape and Priorities
During the 118th Congress, the Senate Bipartisan AI Working Group, which included Republican Senators Mike Rounds (R-S.D.) and Todd Young (R-Ind.), released a policy roadmap titled “Driving U.S. Innovation in Artificial Intelligence.” This document outlined strategies to promote AI development, address national security concerns, and consider ethical implications.
In the 119th Congress, Senate Republicans are anticipated to prioritize:
Promoting Innovation: Advocating for policies that support AI research and development to maintain the United States’ competitive edge in technology.
National Security: Focusing on the implications of AI in defense and security, ensuring that advancements do not compromise national safety.
Economic Growth: Encouraging the integration of AI in various industries to stimulate economic development and job creation.
Regulatory Approach
Senate Republicans generally favor a cautious approach to AI regulation, aiming to avoid stifling innovation. There is a preference for industry self-regulation and the development of ethical guidelines without extensive government mandates. This stance reflects concerns that premature or overly restrictive regulations could hinder technological progress and economic benefits associated with AI.
Bipartisan Considerations
While Republicans hold the majority, bipartisan collaboration remains essential for passing comprehensive AI legislation. Areas such as national security and economic competitiveness may serve as common ground for bipartisan efforts. However, topics like AI’s role in misinformation and election integrity could present challenges due to differing party perspectives on regulation and free speech.
Conclusion
In both the House and Senate, Republicans are approaching AI legislation with a focus on fostering innovation, enhancing national security, and promoting economic growth. Their preference leans toward industry self-regulation and minimal government intervention to avoid stifling innovation. Areas like national security offer potential bipartisan common ground, though debates around misinformation and election integrity may highlight partisan divides.
With House and Senate Republicans already working on a likely massive reconciliation package focused on top Republican priorities including tax, border security, and energy, AI advocates will be hard pressed to ensure their legislative goals find space in the final text.
The BR Privacy & Security Download: January 2025
Must Read! The U.S. Department of Health and Human Services Office for Civil Rights recently proposed an amendment to the Health Insurance Portability and Accountability Act of 1996 (“HIPAA”) Security Rule to strengthen cyber security protections for electronic protected health information. Read the full alert to learn more about the first significant update to HIPAA’s Security Rule in over a decade. Read More > >
STATE & LOCAL LAWS & REGULATIONS
Five New State Comprehensive Privacy Laws Effective in January with Three More to Follow in 2025: With the start of the new year, five new state comprehensive privacy laws have become effective. The comprehensive privacy laws of Delaware, Iowa, Nebraska, and New Hampshire became effective on January 1, 2025, and New Jersey’s law will come into effect on January 15, 2025. Tennessee, Minnesota, and Maryland will follow suit and take effect on July 1, 2025, July 31, 2025, and October 1, 2025, respectively. Companies should review their privacy compliance programs to identify potential compliance gaps with differences in the increasing patchwork of state laws.
Colorado Issues Proposed Draft Amendments to CPA Rules: The Colorado Attorney General announced the adoption of amendments to the Colorado Privacy Act (“CPA”) rules. The rules will become effective on January 30, 2025. The rules provide enhanced protections for the processing of biometric data as well as the processing of the online activities of minors. Specifically, companies must develop and implement a written biometric data policy, implement appropriate security measures regarding biometric data, provide notice of the collection and processing of biometric data, obtain employee consent for the processing of biometric data, and provide a right of access to such data. In the context of minors, the amendment requires that entities obtain consent prior to using any system design feature designed to significantly increase the use of an online service of a known minor and to update the Data Protection Assessments to address processing that presents heightened risks to minors. Entities already subject to the CPA should carefully review whether they may have heightened obligations for the processing of employee biometric data, a category of data previously exempt from the scope of the CPA.
CPPA Announces Increased Fines and Penalties Under CCPA: The California Privacy Protection Agency (“CPPA”), the enforcement authority of the California Consumer Privacy Act (“CCPA”), has adjusted the fines and monetary thresholds of the CCPA. Under the CCPA, in January of every odd-numbered year, the CPPA must make this adjustment to account for changes in the Consumer Price Index. The CPPA has increased the monetary thresholds of the CCPA from $25,000,000 to $26,625,000. The CPPA also increased the range of monetary damages from between $100 to $750 per consumer per incident or actual damages (whichever is greater) to $107 to $799. The range of civil penalties and administrative fine amounts further increased from $2,500 for each violation of the CCPA or $7,500 for each intentional violation and violations involving the personal information of children under 16 to $2,663 and $7,988, respectively. The new amounts went into effect on January 1, 2025.
Connecticut State Senator Previews Proposed Legislation to Update State’s Comprehensive Privacy Law: Connecticut State Senator James Maroney (D) has announced that he is drafting a proposed update to the Connecticut Privacy Act that would expand its scope, provide enhanced data subject rights, include artificial intelligence (“AI”) provisions, and potentially eliminate certain exemptions currently available under the Act. Senator Maroney expects that the proposed bill could receive a hearing by late January or early February. Although Maroney has not published a draft, he indicated that the draft would likely (1) reduce the compliance threshold from the processing of the personal data of 100,000 consumers to 35,000 consumers; (2) include AI anti-discrimination measures, potentially in line with recent anti-discrimination requirements in California and Colorado; (3) expand the definition of sensitive data to include religious beliefs and ethnic origin, in line with other state laws; (4) expand the right to access personal data under the law to include a right to access a list of third parties to whom personal data was disclosed, mirroring similar rights in Delaware, Maryland, and Oregon; and (5) potentially eliminate or curtail categorical exemptions under the law, such as that for financial institutions subject to the Gramm-Leach-Bliley Act.
CPPA Endorses Browser Opt-Out Law: The CPPA’s board voted to sponsor a legislative proposal that would make it easier for California residents to exercise their right to opt out of the sale of personal information and sharing of personal information for cross-context behavioral advertising purposes. Last year, Governor Newsome vetoed legislation with the same requirements. Just as last year’s vetoed legislation, the legislative proposal sponsored by the CPPA requires browser vendors to include a feature that allows users to exercise their opt-out right through opt-out preference signals. Under the CCPA, businesses are required to honor opt-out preference signals as valid opt-out requests. Opt-out preference signals allow a consumer to exercise their opt-out right with all businesses they interact with online without having to make individualized requests with each business. If the proposal is adopted, California would be the first state to require browser vendors to offer consumers the option to enable these signals. Six other states (Colorado, Connecticut, Delaware, Montana, Oregon, and Texas) require businesses to honor browser privacy signals as an opt-out request.
FEDERAL LAWS & REGULATIONS
HHS Proposes Updates to HIPAA Security Rule: The U.S. Department of Health and Human Services (“HHS”) Office for Civil Rights (“OCR”) issued a Notice of Proposed Rulemaking (“NPRM”) to amend the Health Insurance Portability and Accountability Act of 1996 (“HIPAA”) Security Rule to strengthen cybersecurity protections for electronic protected health information (“ePHI”). The NPRM proposes the first significant updates to HIPAA’s Security Rule in over a decade. The NPRM makes a number of updates to the administrative, physical, and technical safeguards specified by the Security Rule, removes the distinction between “required” and “addressable” implementation specifications, and makes all implementation specifications “required” with specific, limited exceptions.
Trump Selects Andrew Ferguson as New FTC Chair: President-elect Donald Trump has selected current Federal Trade Commission (“FTC”) Commissioner Andrew Ferguson to replace Lina Khan as the new FTC Chair. Ferguson is one of two Republicans of the five FTC Commissioners and has been a Commissioner since April of 2024. Prior to becoming an FTC Commissioner, Ferguson served as Virginia’s solicitor general. During his time as an FTC Commissioner, Ferguson dissented from several of Khan’s rulemaking efforts, including a ban on non-compete clauses in employment contracts. Separately, Trump also selected Mark Meador to be an FTC Commissioner. Once Meador is confirmed to give the FTC a Republican majority, a Republican-led FTC under Ferguson may deprioritize rulemaking and enforcement efforts relating to privacy and AI. In a leaked memo first reported by Punchbowl News, Ferguson wrote to Trump that, under his leadership, the FTC would “stop abusing FTC enforcement authorities as a substitute for comprehensive privacy legislation” and “end the FTC’s attempt to become an AI regulator.”
FERC Updates and Consolidates Cybersecurity Requirements for Gas Pipelines : The U.S. Federal Energy Regulatory Commission (“FERC”) has issued a final rule to update and consolidate cybersecurity requirements for interstate natural gas pipelines. Effective February 7, 2025, the rule adopts Version 4.0 of the Standards for Business Practices of Interstate Natural Gas Pipelines, as approved by the North American Energy Standards Board (“NAESB”). This update aims to enhance the efficiency, reliability, and cybersecurity of the natural gas industry. The new standards consolidate existing cybersecurity protocols into a single manual, streamlining processes and strengthening protections against cyber threats. This consolidation is expected to make it easier and faster to revise cybersecurity standards in response to evolving threats. The rule also aligns with broader U.S. government efforts to prioritize cybersecurity across critical infrastructure sectors. Compliance filings are required by February 3, 2025, and the standards must be fully adhered to by August 1, 2025.
House Taskforce on AI Delivers Report to Address AI Advancements: The House Bipartisan Task Force on Artificial Intelligence (the “Task Force”) submitted its comprehensive report to Speaker Mike Johnson and Democratic Leader Hakeem Jeffries. The Task Force was created to ensure America’s continued global leadership in AI innovation with appropriate safeguards. The report advocates for a sectoral regulatory structure and an incremental approach to AI policy, ensuring that humans remain central to decision-making processes. The report provides a blueprint for future Congressional action to address advancements in AI and articulates guiding principles for AI adoption, innovation, and governance in the United States. Key areas covered in the report include government use of AI, federal preemption of state AI law, data privacy, national security, research and development, civil rights and liberties, education and workforce development, intellectual property, and content authenticity. The report aims to serve as a roadmap for Congressional action, addressing the potential of AI while mitigating its risks.
CFPB Proposes Rule to Restrict Sale of Sensitive Data: The Consumer Financial Protection Bureau (“CFPB”) proposed a rule that would require data brokers to comply with the Fair Credit Reporting Act (“FCRA”) when selling income and certain other consumer financial data. CFPB Director Rohit Chopra stated the new proposed rule seeks to limit “widespread evasion” of the FCRA by data brokers when selling sensitive personal and financial information of consumers. Under the proposed rule, data brokers could sell financial data only for permissible purposes under the FCRA, including checking on loan applications and fraud prevention. The proposed rule would also limit the sale of personally identifying information known as credit header data, which can include basic demographic details, including names, ages, addresses, and phone contacts.
FTC Issues Technology Blog on Mitigating Security Risks through Data Management, Software Development and Product Design: The Federal Trade Commission (“FTC”) published a blog post identifying measures that companies can take to limit the risks of data breaches. These measures relate to security in data management, security in software development, and security in product design for humans. The FTC emphasizes comprehensive governance measures for data management, including (1) enforcing mandated data retention schedules; (2) mandating data deletion in accordance with these schedules; (3) controlling third-party data sharing; and (4) encrypting sensitive data both in transit and at rest. In the context of security in software development, the FTC identified (1) building products using memory-safe programming languages; (2) rigorous testing, including penetration and vulnerability testing; and (3) securing external product access to prevent unauthorized remote intrusions as key security measures. Finally, in the context of security in product design for humans, the FTC identified (1) enforcing least privilege access controls; (2) requiring phishing-resistant multifactor authentication; and (3) designing products and services without the use of dark patterns to reduce the over-collection of data. The blog post contains specific links to recent FTC enforcement actions specifically addressing each of these issues, providing users with insight into how the FTC has addressed these issues in the past. Companies reviewing their security and privacy governance programs should ensure that they consider these key issues.
U.S. LITIGATION
Texas District Court Prevents HHS from Enforcing Reproductive Health Privacy Rule Against Doctor: The U.S. District Court for the Northern District of Texas ruled that a Texas doctor is likely to prevail on her claim that HHS exceeded its statutory authority when it adopted an amendment to the Health Insurance Portability and Accountability Act (“HIPAA”) Privacy Rule that protects reproductive health care information and enjoined HHS from enforcing the rule against her. The 2024 amendment to the HIPAA Privacy Rule prohibits covered entities from disclosing information that could lead to an investigation or criminal, civil, or administrative liability for seeking, obtaining, providing, or facilitating reproductive health care. The Court stated that the rule likely unlawfully interfered with the plaintiff’s state-law duty to report suspected child abuse in violation of Congress’s delegation to the agency to enact rules interpreting HIPAA without limiting any law providing for such reporting. The plaintiff argued that, under Texas law, she is obligated to report instances of child abuse within 48 hours, and that relevant requests from Texas regulatory authorities demand the full, unredacted patient chart, which for female patients includes information about menstrual periods, number of pregnancies, and other reproductive health information, among other reproductive health information.
Attorneys General Oppose Clearview AI Biometric Data Privacy Settlement: A proposed settlement in the Clearview AI Illinois Biometric Information Privacy Act (“BIPA”) litigation is facing opposition from 22 states and the District of Columbia. The Attorneys General of each state argue that the settlement, which received preliminary approval in June 2024, lacks meaningful injunctive relief and offers an unusual financial stake in Clearview AI to plaintiffs. The settlement would grant the class of consumers a 23 percent stake in Clearview AI, potentially worth $52 million, based on a September 2023 valuation. Alternatively, the class could opt for 17 percent of the company’s revenue through September 2027. The AGs contend the settlement doesn’t adequately address consumer privacy concerns and the proposed 39 percent attorney fee award is excessive. Clearview AI has filed a motion to dismiss the states’ opposition, arguing it was submitted after the deadline for objections. A judge will consider granting final approval for the settlement at a hearing scheduled on January 30, 2025.
Federal Court Upholds New Jersey’s Daniel’s Law, Dismissing Free Speech Challenges: A federal judge affirmed the constitutionality of New Jersey’s Daniel’s Law, dismissing First Amendment objections raised by data brokers. Enacted following the murder of Daniel Anderl, son of U.S. District Judge Esther Salas, the law permits covered individuals—including active, retired, and former judges, prosecutors, law enforcement officers, and their families—to request the removal of personal details, such as home addresses and unpublished phone numbers, from online platforms. Data brokerage firms that find themselves on the receiving end of such requests are mandated by the statute to comply within ten (10) business days, with penalties for non-compliance including actual damages or a $1,000 fine for each violation, as well as potential punitive damages for instances of willful disregard. Notably, in 2023, Daniel’s Law was amended to allow claim assignments to third parties, resulting in over 140 lawsuits filed by a single consumer data protection company: Atlas Data Privacy Corporation. Atlas Data, a New Jersey firm specializing in data deletion, has emerged as a significant force in this litigation, utilizing Daniel’s Law to challenge data brokers on behalf of around 19,000 individuals. The court, in upholding Daniel’s Law, emphasized its critical role in safeguarding public officials while concurrently ensuring public oversight remains strong. Although data brokers contended that the law infringed on free speech and unfairly targeted their operations, the court dismissed these claims as lacking merit, instead placing significant emphasis on the statute’s relatively focused scope and substantial state interest at play. Although unquestionably a significant victory for advocates of privacy rights, the judge permitted an immediate appeal by the data brokers.
GoodRx Settles Class Action Suit Over Alleged Data Sharing Violations: GoodRx has agreed to a $25 million settlement in a class-action lawsuit alleging the company violated privacy laws by sharing users’ sensitive health data with advertisers like Meta Platforms, Google, and Criteo Corp. The settlement, if approved, would resolve a lawsuit filed in February 2023. The lawsuit followed an FTC action alleging that GoodRx shared information about users’ prescriptions and health conditions with advertising companies. GoodRx settled the FTC matter for $1.5 million. The proposed class in the class-action lawsuit is estimated to be in the tens of millions and would give each class member an average recovery ranging from $3.31 to $11.03. The settlement also allows the plaintiffs to use information from GoodRx to pursue their claims against the other defendants, including Meta, Google, and Criteo.
23andMe Data Breach Suit Settlement Approved: A federal judge approved a settlement to resolve claims that alleged 23andMe Inc. failed to secure the sensitive personal data causing a data breach in 2023. According to 23andMe, a threat actor was able to access roughly 14,000 user accounts through credential stuffing, which further enabled access to the personal information that approximately 6.9 million users made available through 23andMe’s DNA Relative and Family Tree profile features. Under the terms of the $30 million settlement, class members will receive cash compensation and three years of data monitoring services, including genetic services.
U.S. ENFORCEMENT
FTC Takes Action Against Company for Deceptive Claims Regarding Facial Recognition Software: The Federal Trade Commission (“FTC”) announced that it has entered into a settlement with IntelliVision Technologies Corp. (“IntelliVision”), which provides facial recognition software used in home security systems and smart home touch panels. The FTC alleged that IntelliVision’s claims that it had one of the highest accuracy rates on the market, that its software was free of gender or racial bias, and was trained on millions of faces was false or misleading. The FTC further alleged that IntelliVision did not have adequate evidence to support its claim that its anti-spoofing technology ensures the system cannot be tricked by a photo or video image. The proposed order against IntelliVision specifically prohibits IntelliVision from misrepresenting the effectiveness, accuracy, or lack of bias of its facial recognition technology and its technology to detect spoofing, and the comparative performance of the technology with respect to individuals of different genders, ethnicities, and skin tones.
FTC Settles Enforcement Actions with Data Brokers for Selling Sensitive Location Data: The FTC announced settlements with data brokers Gravy Analytics Inc. (“Gravy Analytics”) and Mobilewalla, Inc. (“Mobilewalla”) related to the tracking and sale of sensitive location data of consumers. According to the FTC, Gravy Analytics violated the FTC Act by unfairly selling sensitive consumer location data, by collecting and using consumers’ location data without obtaining verifiable user consent for commercial and government uses, and by selling data regarding sensitive characteristics such as health or medical decisions, political activities, and religious views derived from location data. Under the proposed settlement, Gravy Analytics will be prohibited from selling, disclosing, or using sensitive location data in any product or service, delete all historic location data and data products using such data, and must establish a sensitive data location compliance program. Separately, the FTC settled allegations against Mobilewalla stemming from allegations that Mobilewalla collected location data from real-time bidding exchanges and third-party aggregators, including data related to health clinic visits and visits to places of worship, without the knowledge of consumers, and subsequently sold such data. According to the FTC, when Mobilewalla bid to place an ad for its clients on a real-time advertising bidding exchange, it unfairly collected and retained the information in the bid request, even when it didn’t have a winning bid. Under the proposed settlement, Mobilewalla will be prohibited from selling sensitive location data and from collecting consumer data from online advertising auctions for purposes other than participating in those auctions.
Texas Attorney General Issues New Warnings Under State’s Comprehensive Privacy Law: The Texas Attorney General issued warnings to satellite radio broadcaster Sirius XM and three mobile app providers that they appear to be sharing sensitive data of consumers, including location data, without proper notification or obtaining consent. The letter warnings did not come with a press release or other public statement and were reported by Recorded Future News, who obtained the notices through a public records request. The letter to Sirius XM stated that the Attorney General’s office found a number of violations of the Texas Data Privacy and Security Act by the Sirius XM privacy notice, including failing to provide reasonably clear notice of the categories of sensitive data being processed and processing sensitive data without appropriate consent. Similar letters were sent to mobile app providers stating that the providers failed to obtain consumer consent for data sharing or including information on how consumers could exercise their rights under Texas law.
Texas Attorney General Launches Investigations Into 15 Companies for Children’s Privacy Practices: The Texas Attorney General’s office announced it had launched investigations into Character.AI and 14 other companies including Reddit, Instagram, and Discord. The Attorney General’s press release stated that the investigations related to the companies’ privacy and safety practices for minors pursuant to the Securing Children Online through Parental Empowerment (“SCOPE”) Act and the Texas Data Privacy and Security Act (“TDPSA”). Details of the Attorney General’s allegations were not provided in the announcement. The TDPSA requires companies to provide notice and obtain consent to collect and use minors’ personal data. The SCOPE Act prohibits digital service providers from sharing, disclosing, or selling a minor’s personal identifying information without permission from the child’s parent or legal guardian and provides parents with tools to manage privacy settings on their child’s account.
HHS Imposes Penalty Against Medical Provider for Impermissible Access to PHI and Security Rule Violations: The U.S. Department of Health and Human Services Office of Civil Rights (“OCR”) announced that it imposed a $1.19 million civil penalty against Gulf Coast Pain Consultants, LLC d/b/a Clearway Pain Solutions Institute (“GCPC”) for violations of the HIPAA Security Rule arising from a data breach. GCPC’s former contractor had impermissibly accessed GCPC’s electronic medical record system to retrieve protected health information (“PHI”) for use in potential fraudulent Medicare claims. OCR’s investigation determined that the impermissible access occurred on three occasions, affecting approximately 34,310 individuals. The compromised PHI included patient names, addresses, phone numbers, email addresses, dates of birth, Social Security numbers, chart numbers, insurance information, and primary care information. OCR’s investigations revealed multiple potential violations of the HIPAA Security Rule, including failures to conduct a compliant risk analysis and implement procedures to regularly review records of activity in information systems and terminate former workforce members’ access to electronic PHI.
HHS Settles with Health Care Clearinghouse for HIPAA Security Rule Violations: OCR announced a settlement with Inmediata Health Group, LLC (“Inmediata”), a healthcare clearinghouse, for potential violations of the HIPAA Security Rule, following OCR’s receipt of a 2018 complaint that PHI was accessible to search engines like Google, on the Internet. OCR’s investigation determined that from May 2016 through January 2019, the PHI of 1,565,338 individuals was made publicly available online. The PHI disclosed included patient names, dates of birth, home addresses, Social Security numbers, claims information, diagnosis/conditions, and other treatment information. OCR’s investigation also identified multiple potential HIPAA Security Rule violations including failures to conduct a compliant risk analysis and to monitor and review Inmediata’s health information systems’ activity. Under the settlement, Inmediata paid OCR $250,000. OCR determined that a corrective action plan was not necessary in this resolution as Inmediata had previously agreed to a settlement with 33 states that included corrective actions that addressed OCR’s findings.
New York State Healthcare Provider Settles with Attorney General Regarding Allegations of Cybersecurity Failures: HealthAlliance, a division of Westchester Medical Center Health Network (“WMCHealth”), has agreed to pay a $1.4 million fine, with $850,000 suspended, due to a 2023 data breach affecting over 240,000 patients and employees in New York State. The breach at issue, which occurred between September and October 2023, was reportedly caused by a security flaw in Citrix NetScaler—a tool used by many organizations to optimize web application performance and availability by reducing server load—that went unpatched. Although HealthAlliance was made aware of the vulnerability, they were unsuccessful in patching it due to technical difficulties, ultimately resulting in the exposure of 196 gigabytes of data, including particularly sensitive information like Social Security numbers and medication records. As part of its agreement with New York State, HealthAlliance must enhance its cybersecurity practices by implementing a comprehensive information security program, developing a data inventory, and enforcing a patch management policy to address critical vulnerabilities within 72 hours. For more details, view the press release from the New York Attorney General’s office.
HHS Settles with Children’s Hospital for HIPAA Privacy and Security Violations: OCR announced a $548,265 civil monetary penalty against Children’s Hospital Colorado (“CHC”) for violations of the HIPAA Privacy and Security Rules arising from data breaches in 2017 and 2020. The 2017 data breach involved a phishing attack that compromised an email account containing 3,370 individuals’ PHI and the 2020 data breach compromised three email accounts containing 10,840 individuals’ PHI. OCR’s investigation determined that the 2017 data breach occurred because multi-factor authentication was disabled on the affected email account. The 2020 data breach occurred, in part, when workforce members gave permission to unknown third parties to access their email accounts. OCR found violations of the HIPAA Privacy Rule for failure to train workforce members on the HIPAA Privacy Rule, and the HIPAA Security Rule requirement to conduct a compliant risk analysis to determine the potential risks and vulnerabilities to ePHI in its systems.
INTERNATIONAL LAWS & REGULATIONS
Italy Imposes Landmark GDPR Fine on AI Provider for Data Violations: In the first reported EU penalty under the GDPR relating to generative AI, Italy’s data protection authority, the Garante, fined OpenAI 15 million euros for breaching the European Union’s General Data Protection Regulation (“GDPR”). The penalty was linked to three specific incidents involving OpenAI: (1) unauthorized use of personal data for ChatGPT training without user consent, (2) inadequate age verification risking exposure of minors to inappropriate content, and (3) failure to report a March 2023 data breach that exposed users’ contact and payment information. The investigation into OpenAI, which began after the Garante was made aware of the March 2023 breach, initially resulted in Italy temporarily blocking access to ChatGPT but eventually reinstated it after OpenAI made concrete improvements to its age verification and privacy policies. Alongside the monetary penalty, OpenAI is additionally mandated to conduct a six-month public awareness campaign in Italy to educate the Italian public on data collection and individual user rights under GDPR. OpenAI has said that it plans to appeal the Garante’s decision, arguing that the fine exceeds its revenue in Italy.
Australian Parliament Approves Privacy Act Reforms and Bans Social Media Use by Minors: The Australian Parliament passed a number of privacy bills in December. The bills include reforms to the Australian Privacy Act, a law requiring age verification by social media platforms, and a law banning social media use by minors under the age of 16. Privacy Act reforms include new enforcement powers for the Office of the Australian Information Commissioner that clarify when “serious” breaches of the Privacy Act occur and allow the OAIC to bring civil penalty proceedings for lesser breaches. Other reforms include requiring entities that use personal data for automated decision-making to include in their privacy notices information about what data is used for automated decision-making and what types of decisions are made using automated decision-making technology.
EDPB Releases Opinion on Personal Data Use in AI Models: In response to a formal request from Ireland’s Data Protection Commission asking for clarity about how the EU General Data Protection Regulation (“GDPR”) applies to the training of large language models with personal data, the European Data Protection Board (“EDPB”) released its opinion regarding the lawful use of personal data for the development and deployment of artificial intelligence models (the “Opinion”). The Irish Data Protection Commission specifically requested EDPB to opine on: (1) when and how an AI model can be considered anonymous, (2) how legitimate interests can be used as the legal basis in the development and deployment phases of an AI model, and (3) the consequences of unlawful processing in the development phase of an AI model on its subsequent operation. With respect to anonymity, the EDPB stated this should be analyzed on a case-by-case basis taking into account the likelihood of obtaining personal data of individuals whose data was used to build the model and the likelihood of extracting personal data from queries. The Opinion describes certain methods that controllers can use to demonstrate anonymity. With respect to the use of legitimate interest as a legal basis for processing, the EDPB restated a three-part test to assess legitimate interest from its earlier guidance. Finally, the EDPB reviewed several scenarios in which personal data may be unlawfully processed to develop an AI model.
Second Draft of General-Purpose AI Code of Practice Published: The European Commission announced that independent experts published the Second Draft of the General Purpose AI Code of Practice. The AI Code of Practice is designed to be a guiding document for providers of general-purpose AI models, allowing them to demonstrate compliance with the AI Act. Under the EU AI Act, providers are persons or entities that develop an AI system and place that system on the market. This second draft is based on the responses and comments received on the first draft and is designed to provide a “future-proof” code. The first part of the Code details transparency and copyright obligations for all providers of general-purpose AI models. The second part of the Code applies to providers of advanced general-purpose AI models that could pose systemic risks. This section outlines measures for systemic risk assessment and mitigation, including model evaluations, incident reporting, and cybersecurity obligations. The Second Draft will be open for comments until January 15, 2025.
NOYB Approved to Bring Collective Redress Claims: The Austrian-based non-profit organization None of Your Business (“NOYB”) has been approved as a Qualified Entity in Austria and Ireland, enabling it to pursue collective redress actions across the European Union (“EU”). Famous for challenging the EU-US data transfer framework through its Schrems I and II actions, NOYB intends to use the EU’s collective action redress system to challenge what it describes as unlawful processing without consent, use of deceptive dark patterns, data sales, international data transfers, and use of “absurd” language in privacy policies. Unlike US class actions, these EU actions are strictly non-profit. However, they do provide for both injunctive and monetary redress measures. NOYB intends to bring its first actions in 2025. Click here to learn more and read NOYB’s announcement.
EDPB Issues Guidelines on Third Country Authority Data Requests: The EDPB published draft guidelines on Article 48 of the GDPR relating to the transfer or disclosure of personal data to a governmental authority in a third country (the “Guidelines”). The Guidelines state that, as a general rule, requests from governmental authorities are recognizable and enforceable under applicable international agreements. The Guidelines further state that any such transfer must also comply with Article 6 with respect to legal basis for processing and Article 46 regarding legal mechanism for international data transfer. The Guidelines will be available for public consultation until January 27, 2025.
Irish DPC Fines Meta €251 Million for Violations of the GDPR: The Irish Data Protection Commission (DPC) fined Meta €251 million following a 2018 data breach that affected 29 million Facebook accounts globally, including 3 million in the European Union. The breach exposed personal data such as names, contact information, locations, birthdates, religious and political beliefs, and children’s data. The DPC found that Meta Ireland violated General Data Protection Regulation (GDPR) Articles 33(3) and 33(5) by failing to provide complete information in their breach notification and to properly document the breach. Furthermore, Meta Ireland infringed GDPR Articles 25(1) and 25(2) by neglecting to incorporate data protection principles into the design of their processing systems and by processing more data than necessary by default.
Additional Authors: Daniel R. Saeedi, Rachel L. Schaller, Gabrielle N. Ganze, Ana Tagvoryan, P. Gavin Eastgate, Timothy W. Dickens, Jason C. Hirsch, Tianmei Ann Huang, Adam J. Landy, Amanda M. Noonan, and Karen H. Shin
NYSERDA Issues Request for Information in Preparation for Sixth OREC Solicitation with Transmission Issues in the Forefront
As New York’s fifth Offshore Wind Renewable Energy Certificate (OREC) solicitation enters its final stages, the New York State Energy Research and Development Authority (“NYSERDA”) issued a Request for Information (“RFI”) on December 18, 2024, to solicit feedback concerning its next solicitation, which has been dubbed “NY6”.
While NYSERDA has requested feedback on a number of general concepts, including the structure, timeline and eligibility criteria for NY6, the RFI is notable for its focus on the relationship between generation and transmission. In particular, NYSERDA is seeking feedback on how to encourage applicants to optimize the coordination between offshore wind generation projects and ongoing or new transmission projects. The RFI builds on the New York State Public Service Commission’s (the “Commission”) Order Addressing Public Policy Requirements for Transmission Planning Purposes, issued June 22, 2023, (the “PPTN Order”).
In previous solicitations, NYSERDA sought radial offshore wind projects inclusive of generation, export infrastructure, and interconnection with the onshore grid. NY6 may mark an evolution in New York’s approach to offshore wind project infrastructure in which NYSERDA looks to separate transmission aspects of projects from generation aspects. Subject to Commission approval, in NY6, NYSERDA may elect to solicit “Generation-Only” proposals that would prioritize utilization of the transmission projects being developed and undertaken pursuant to the PPTN Order.
Respondents have until January 29, 2025 at 3 pm Eastern Standard Time to submit comments to the RFI. All comments should be emailed to [email protected], with the subject line “NY6 RFI Comments”.
Stay tuned for more on the Offshore Wind space, including additional insights into developments under the incoming Trump administration.