Federal Circuit Limits Use of Applicant Admitted Prior Art in Inter Partes Reviews
As provided by statute at 35 U.S.C. § 311(b), a petitioner in an inter partes review (IPR) may challenge the claims of a patent “only on the basis of prior art consisting of patents or printed publications.” Does this provision permit IPR challenges based on Applicant Admitted Prior Art (AAPA) ― art identified in the patent as previously known ― in combination with a patent or printed publication? The Federal Circuit recently announced its decision in Qualcomm Inc. v. Apple Inc., clarifying that AAPA is not a “patent[] or printed publication[]” under the statute, and that combining AAPA with a patent or printed publication does not shield the use of AAPA from violating 35 U.S.C. § 311(b) in a petition for IPR.
Background
History of Appeals
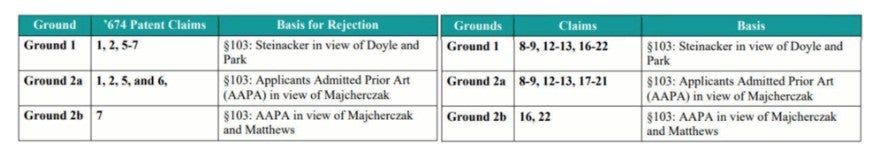
In January 2020, the Patent Trial and Appeal Board determined in a final written decision that the ’674 Patent claims were unpatentable under Ground 2. The Board rejected the arguments of the patent owner (Qualcomm) that Ground 2 was “not permitted.” The Board held that “AAPA is admitted to be prior art and is found in the ’674 patent” and was thus “prior art consisting of patents or printed publications,” and therefore qualified as prior art under § 311(b).
The patent owner appealed, arguing that AAPA could not be used as a “basis” for an IPR challenge, and that § 311(b) is limited to “prior art consisting of patents or printed publications.” While the appeal was pending, former USPTO Director Iancu published guidance in August 2020 noting that AAPA is not “prior art consisting of patents or printed publications” under § 311(b), but that AAPA, “if used in conjunction with” other patent documents “forming ‘the basis’” of an IPR proceeding under § 311, could support a finding of obviousness. Nonetheless, in February 2022, the Federal Circuit vacated the Board’s ruling against the patent owner, finding that AAPA does not qualify as prior art under § 311(b) and may not form the basis of an IPR proceeding, but could be used in an IPR “under particular circumstances,” and remanding back to the Board to consider whether the AAPA formed “the basis” of Ground 2.
In response, former USPTO Director Vidal issued superseding guidance in June 2022 that established an “in combination” rule: “Board panels should determine whether the petition relies on admissions in the specification in combination with reliance on at least one prior art patent or printed publication” and, if so, “those admissions do not form ‘the basis’ of the ground and must be considered by the Board in its patentability analysis.” Applying this superseding guidance, the Board again found in a second final written decision on remand that the challenged claims of the ’674 patent were unpatentable under Ground 2 because petitioner did not use AAPA to form the “basis” of Ground 2.
The patent owner once again appealed to the Federal Circuit. In its recent decision of April 23, 2025, the Federal Circuit found that the plain meaning of § 311(b) limits the basis of an IPR proceeding to only prior art patents or printed publications, and that AAPA cannot be used, alone or in combination with prior art patents or printed publications, as the basis for instituting an IPR. The Federal Circuit acknowledged that AAPA may be used to provide general background knowledge without violating § 311(b) and may be relied upon in combination with prior art patents or printed publications—just not as the basis.
Since the Board had already rejected petitioner’s Ground 1 argument for invalidity of the ’674 patent claims, and no other grounds remained, the Federal Circuit reversed, noting that the Board should have instead found that the challenged claims are not unpatentable.
Key Takeaways
While AAPA may be relied on in an IPR, it is critical for litigants to ensure that AAPA is not used to form the basis of the IPR. This clarification of § 311(b) by the Federal Circuit will ultimately require a higher threshold for challenging patents in IPRs. In order to avoid early dismissals, IPR petitions should be clear in how AAPA is being used, including identifying only printed patents and publications as the grounds for petitions.
USPTO Launches Task Force to Combat Patent Fraud and Protect the Patent System
The U.S. Patent and Trademark Office (USPTO) recently announced the creation of the Patent Fraud Detection and Mitigation Working Group. The working group is designed to identify and address threats to the patent system as well as to weed out improper activity in patent applications and reexamination proceedings. USPTO officials believe that these efforts will reduce pendency time for patent applications and preserve USPTO resources.
In particular, the working group is tasked with:
Addressing mistakes in fee certifications and assertions. To date, the USPTO has mailed more than 2,200 fee deficiency notices in patent applications in response to false micro entity certifications as well as 68 notices responding to false small entity certifications. Patent Applicants and practitioners are reminded that only entities that meet certain requirements can claim fee discounts as a small entity or micro entity, and an incorrect claim of small entity status or micro entity status can jeopardize the validity of a patent. Details regarding the requirements for establishing small entity status and micro entity status can be found here.
Identifying and reviewing potential misrepresentations to the USPTO, including for false signatures, and using the administrative sanctions process to address misrepresentations where appropriate. Since June 2023, the USPTO has terminated more than 3,300 applications due to false signatures. Patent Applicants and practitioners are reminded that, pursuant to 37 CFR 1.4, a signer’s signature on any paper submitted to the USPTO must be personally made or inserted by the signer and cannot be made by another at the signer’s direction. This applies to both handwritten signatures and S-signatures.
Preventing non-practitioners from engaging in the unauthorized practice of law. Except for pro se representation, a patent Applicant can only be represented in a patent matter before the USPTO by individuals specifically authorized to do so. 37 CFR 11.10(a). With some exceptions, this generally requires a registered patent practitioner who has, among other things, passed the patent registration examination. 37 CFR 11.7. Representing another before the USPTO regarding a patent matter is not limited to signing and filing papers in a patent application, but can also include drafting the patent application, drafting amendments and replies to communications from the USPTO, and giving advice to a client in contemplation of filing a patent application or an amendment or reply in a patent application. 37 CFR 11.5(b)(1). Patent Applicants are encouraged to obtain representation regarding patent matters only from authorized patent practitioners.
Monitoring and investigating otherwise suspicious filings.
Serving as the main point of contact within the USPTO for reporting potential threats to the patent system.
The USPTO has introduced a new webpage serving as a centralized hub to keep the public informed about emerging threats in patent applications and reexamination proceedings. Additionally, the USPTO will share data outlining its mitigation efforts.
Click here to visit the new USPTO Patent Fraud Detection and Mitigation website.
China’s Supreme People’s Court and Supreme People’s Procuratorate Issue Interpretation on Several Issues Concerning the Application of Law in Handling Criminal Cases of Intellectual Property Infringement
On April 24, 2025, China’s Supreme People’s Court (SPC) and Supreme People’s Procuratorate (SPP) jointly issued the Interpretation on Several Issues Concerning the Application of Law in Handling Criminal Cases of Intellectual Property Infringement (关于办理侵犯知识产权刑事案件适用法律若干问题的解释). The Interpretation clarifies trademark crimes, patent counterfeiting, copyright crimes, trade secret misappropriation, and common issues arising in IP crimes (e.g., heavier or reduced sentences). The Interpretation is effective as of April 26, 2025.
A translation follows. The original text is available here (Chinese only).
In order to punish crimes of infringement of intellectual property rights in accordance with the law and maintain the socialist market economic order, in accordance with the relevant provisions of the Criminal Law of the People’s Republic of China, the Criminal Procedure Law of the People’s Republic of China and other laws, and in combination with judicial practice, we hereby explain several issues concerning the application of law in handling criminal cases of infringement of intellectual property rights as follows:
Article 1: Where a person uses a trademark identical to a registered trademark on the same kind of goods or services without the permission of the registered trademark owner, any of the following circumstances shall be deemed to be “the same kind of goods or services” as provided for in Article 213 of the Criminal Law:
(1) The names of the goods actually produced and sold, or the names of the services actually provided by the actor are the same as the names of the goods or services approved for use by the right holder’s registered trademark;
(2) The commodity names are different, but the functions, uses, main raw materials, consumers, sales channels, etc. are the same or substantially the same, and the relevant public generally believes that they are the same kind of commodities;
(3) The service names are different, but the purpose, content, method, object, location, etc. of the services are the same or substantially the same, and the relevant public generally believes that they are the same type of services.
To determine “the same kind of goods or services”, a comparison should be made between the goods or services approved for use by the right holder’s registered trademark and the goods or services actually produced and sold, or the services actually provided, by the actor.
Article 2 A trademark that is identical to a counterfeited registered trademark, or that is substantially indistinguishable from a counterfeited registered trademark and sufficient to mislead the relevant public, shall be deemed a “trademark that is identical to its registered trademark” as provided for in Article 213 of the Criminal Law. A trademark that is substantially indistinguishable from a counterfeited registered trademark and sufficient to mislead the relevant public shall be deemed to be a trademark that is substantially indistinguishable from a counterfeited registered trademark and sufficient to mislead the relevant public if any of the following circumstances exists:
(1) Changing the font, uppercase and lowercase letters, or the horizontal and vertical arrangement of the characters of a registered trademark, which is basically indistinguishable from the registered trademark;
(2) Changing the spacing between words, letters, numbers, etc. of a registered trademark, which is basically indistinguishable from the registered trademark;
(3) Changing the color of a registered trademark does not affect the distinctive features of the registered trademark;
(4) merely adding to a registered trademark elements that lack distinctive features, such as the common name of the goods or model number, which do not affect the distinctive features of the registered trademark;
(5) There is basically no difference between the three-dimensional signs and the two-dimensional elements of the three-dimensional registered trademark;
(6) Other marks that are basically indistinguishable from the registered trademark and are sufficient to mislead the relevant public.
Article 3: Where a person uses a trademark identical to a registered trademark on the same kind of goods without the permission of the registered trademark owner, any of the following circumstances shall be deemed to be a “serious circumstance” as provided for in Article 213 of the Criminal Law:
(1) The amount of illegal income is RMB 30,000 or more, or the amount of illegal business is RMB 50,000 or more;
(2) counterfeiting two or more registered trademarks, with illegal gains exceeding RMB 20,000 or illegal business volume exceeding RMB 30,000;
(3) Having been subject to criminal or administrative punishment for committing an act specified in Articles 213 to 215 of the Criminal Law within two years, he commits the act again, and the amount of illegal gains is more than RMB 20,000 or the amount of illegal business is more than RMB 30,000;
(4) Other circumstances of a serious nature.
If a person uses a trademark identical to a registered trademark on the same kind of service without the permission of the registered trademark owner, any of the following circumstances shall be deemed to be a “serious circumstance” as provided for in Article 213 of the Criminal Law:
(1) The amount of illegal gains is RMB 50,000 or more;
(2) counterfeiting two or more registered trademarks, with the amount of illegal gains exceeding RMB 30,000;
(3) Having been subject to criminal or administrative punishment for committing an act specified in Articles 213 to 215 of the Criminal Law within two years, he commits the act again, and the amount of illegal gains is RMB 30,000 or more;
(4) Other circumstances of a serious nature.
Where a person counterfeits both a registered trademark for goods and a registered trademark for services, and the amount of illegal gains from the counterfeit registered trademark for goods is less than the standard prescribed in the first paragraph of this Article, but the total amount of illegal gains from the counterfeit registered trademark for services reaches the standard prescribed in the second paragraph of this Article, it shall be deemed as “serious circumstances” as prescribed in Article 213 of the Criminal Law.
If the amount of illegal gains or illegal business operations reaches ten times or more the standards specified in the first three paragraphs of this article, it shall be deemed as “particularly serious circumstances” as stipulated in Article 213 of the Criminal Law.
Article 4 Anyone who sells goods bearing counterfeit registered trademarks shall be deemed to have “knowingly” done so as provided for in Article 214 of the Criminal Law if any of the following circumstances exists, unless there is evidence proving that the person was truly unaware:
(1) Knowing that the registered trademark on the goods he sells has been altered, replaced or covered;
(2) Forging or altering a trademark registrant’s authorization document or knowing that the document has been forged or altered;
(3) A person who has been subject to criminal or administrative penalties for selling goods bearing counterfeit registered trademarks and then sells the same goods bearing counterfeit registered trademarks;
(4) purchasing or selling goods at prices significantly lower than the market price without justifiable reasons;
(5) after being discovered by administrative law enforcement agencies or judicial agencies to be selling goods bearing counterfeit registered trademarks, transferring or destroying infringing goods, accounting documents and other evidence, or providing false certification;
(6) Other circumstances that may be regarded as knowing that the goods are counterfeit registered trademarks.
Article 5 Where a person knowingly sells goods that are counterfeit registered trademarks and the amount of illegal proceeds is more than RMB 30,000, it shall be deemed as “a relatively large amount of illegal proceeds” as provided for in Article 214 of the Criminal Law. If any of the following circumstances exists, it shall be deemed as “other serious circumstances” as provided for in Article 214 of the Criminal Law:
(1) The sales amount is RMB 50,000 or more;
(2) Having been subject to criminal or administrative punishment for committing an act specified in Articles 213 to 215 of the Criminal Law within two years, he commits the act again, and the amount of illegal gains is more than RMB 20,000 or the amount of sales is more than RMB 30,000;
(3) The value of the goods bearing counterfeit registered trademarks that have not yet been sold reaches three times or more the sales amount standards prescribed in the first two paragraphs of this paragraph, or the sales amount of the goods that have been sold is less than the sales amount standards in the first two paragraphs of this paragraph, but the total value of the goods and the sales amount of the goods that have not yet been sold reaches three times or more the sales amount standards prescribed in the first two paragraphs of this paragraph.
If the amount of illegal proceeds, sales amount, value of goods, or the total of sales amount and value of goods reaches ten times or more of the standard specified in the preceding paragraph of this Article, it shall be deemed as “the amount of illegal proceeds is huge or there are other particularly serious circumstances” as stipulated in Article 214 of the Criminal Law.
Article 6 Forging or unauthorized manufacturing of another person’s registered trademark or selling forged or unauthorized registered trademark shall be deemed to be a “serious circumstance” as provided for in Article 215 of the Criminal Law if any of the following circumstances exists:
(1) The number of labels is more than 10,000, or the amount of illegal income is more than 20,000 yuan, or the amount of illegal business is more than 30,000 yuan;
(2) Forging, manufacturing without authorization, or selling forged or unauthorized manufacturing of two or more registered trademarks, the number of which is more than 5,000, or the amount of illegal gains is more than RMB 10,000, or the amount of illegal business is more than RMB 20,000;
(3) Having been subject to criminal or administrative punishment for committing an act specified in Articles 213 to 215 of the Criminal Law within two years, and committing the act again, the number of labels is more than 5,000, or the amount of illegal income is more than RMB 10,000, or the amount of illegal business is more than RMB 20,000;
(4) selling registered trademark signs illegally manufactured by others, where the number of signs that have not yet been sold reaches three times or more the standards specified in the first three items of this paragraph, or the number of signs that have been sold is less than the standards specified in the first three items of this paragraph, but the total number of signs that have not yet been sold reaches three times or more the standards specified in the first three items of this paragraph;
(5) Other serious circumstances.
If the number of labels, the amount of illegal income, and the amount of illegal business reach more than five times the standards specified in the preceding paragraph of this article, it shall be deemed as “particularly serious circumstances” as stipulated in Article 215 of the Criminal Law.
Article 7 The term “two or more registered trademarks” as used in this interpretation refers to two or more registered trademarks that identify different sources of goods or services. Although the registered trademarks are different, if they are used on the same goods or services and point to the same source of goods or services, they should not be considered as “two or more registered trademarks”.
The term “piece” of a registered trademark logo as used in this interpretation generally refers to a logo with a complete trademark image. If several logo images are printed on a tangible carrier and the logo image cannot be used independently without the tangible carrier, it shall be deemed as one logo.
Article 8 Whoever commits the crime of counterfeiting registered trademarks as provided for in Article 213 of the Criminal Law and also sells goods bearing the counterfeit registered trademarks, and where such a crime is constituted, he shall be convicted and punished for the crime of counterfeiting registered trademarks in accordance with the provisions of Article 213 of the Criminal Law.
If a person commits the crime of counterfeiting registered trademarks as stipulated in Article 213 of the Criminal Law and sells goods that he knows are counterfeit registered trademarks of others, and the crime is constituted, he shall be punished for multiple crimes.
Article 9 Any of the following circumstances shall be deemed as “counterfeiting another’s patent” as provided for in Article 216 of the Criminal Law:
(1) Forging or altering another person’s patent certificate, patent document or patent application document;
(2) Marking the patent number of another person on the products or product packaging manufactured or sold without permission;
(3) Using another’s patent number in a contract, product manual, advertisement or other promotional materials without permission, causing others to mistakenly believe that the invention, utility model or design is that of another.
Article 10 Anyone who counterfeits another person’s patent shall be deemed to be a “serious circumstance” as provided for in Article 216 of the Criminal Law if any of the following circumstances exists:
(1) The amount of illegal income is more than RMB 100,000 or the amount of illegal business operations is more than RMB 200,000;
(2) causing direct economic losses of more than RMB 300,000 to the patentee;
(3) counterfeiting two or more patents of others, with illegal gains exceeding RMB 50,000 or illegal business volume exceeding RMB 100,000;
(4) Having been subject to criminal or administrative penalties for counterfeiting another person’s patent within two years, he again commits the act, and the amount of illegal gains is more than RMB 50,000 or the amount of illegal business is more than RMB 100,000;
(5) Other serious circumstances.
Article 11: Any act of infringing upon copyright or rights related to copyright without obtaining authorization from the copyright owner, producer of audio or video recordings, or performer, or forging or altering authorization documents, or exceeding the scope of the authorization, shall be deemed as “without the permission of the copyright owner”, “without the permission of the producer of audio or video recordings”, or “without the permission of the performer” as stipulated in Article 217 of the Criminal Law.
A natural person, legal person or unincorporated organization that signs a work or audio or video product in a usual manner as provided for in Article 217 of the Criminal Law shall be presumed to be the copyright owner or audio or video producer, and shall have corresponding rights in the work or audio or video product, unless there is evidence to the contrary.
In cases where there are many types of works, audio and video products involved and the rights holders are scattered, if there is evidence that the works, audio and video products involved were illegally published, copied and distributed, or disseminated to the public through information networks, and the publishers, copy distributors, and information network disseminators cannot provide relevant evidence materials for obtaining permission from the copyright owner, audio and video producer, or performer, it can be determined as “without the permission of the copyright owner”, “without the permission of the audio and video producer”, or “without the permission of the performer” as stipulated in Article 217 of the Criminal Law. However, this does not apply if there is evidence that the rights holder has waived his rights, the copyright of the works involved or the relevant rights of the audio and video products and performers are not protected by China’s Copyright Law, or the protection period of the rights has expired.
Article 12 The act of reproducing and distributing, or reproducing for the purpose of distributing, a work or audio or video recording without the permission of the copyright owner or the owner of rights related to the copyright shall be deemed as “reproduction and distribution” as stipulated in Article 217 of the Criminal Law.
Without the permission of the copyright owner or the owner of rights related to the copyright, providing works, audio and video products, or performances to the public by wired or wireless means so that the public can obtain them at a time and place of their choice shall be deemed as “dissemination to the public through an information network” as stipulated in Article 217 of the Criminal Law.
Article 13 Where an act of infringing upon copyright or copyright-related rights as provided for in Article 217 of the Criminal Law is carried out, and the amount of illegal proceeds is RMB 30,000 or more, it shall be deemed as “a relatively large amount of illegal proceeds” as provided for in Article 217 of the Criminal Law; where any of the following circumstances exists, it shall be deemed as “other serious circumstances” as provided for in Article 217 of the Criminal Law:
(1) The amount of illegal business operations is more than RMB 50,000;
(2) Having been subject to criminal or administrative punishment for committing an act specified in Articles 217 and 218 of the Criminal Law within two years, he commits the act again, and the amount of illegal gains is more than RMB 20,000 or the amount of illegal business is more than RMB 30,000;
(3) copying and distributing another person’s work or audio or video recording, where the total number of copies is 500 or more;
(4) disseminating to the public through information networks other people’s works, audio and video recordings or performances, the total number of which is 500 or more, or the number of which is downloaded more than 10,000 times, or the number of which is clicked more than 100,000 times, or disseminating through a membership system with more than 1,000 registered members;
(5) The amount or quantity does not reach the standards specified in Items 1 to 4 of this paragraph, but reaches more than half of two or more of the standards.
If a person knowingly provides others with devices or components mainly used to circumvent or destroy technical measures, or provides technical services for others to circumvent or destroy technical measures, and the amount of illegal gains or illegal business reaches the standards prescribed in the preceding paragraph, he shall be held criminally liable for the crime of copyright infringement.
If the amount or quantity reaches more than ten times the corresponding standards stipulated in the first two paragraphs of this article, it shall be deemed as “the illegal proceeds are huge or there are other particularly serious circumstances” as stipulated in Article 217 of the Criminal Law.
Article 14: If a person knowingly sells infringing copies as provided for in Article 217 of the Criminal Law, and the amount of illegal proceeds is RMB 50,000 or more, he shall be deemed to have committed the “huge amount of illegal proceeds” as provided for in Article 218 of the Criminal Law. If any of the following circumstances exists, he shall be deemed to have committed the “other serious circumstances” as provided for in Article 218 of the Criminal Law:
(1) The sales amount is more than RMB 100,000;
(2) Having been subject to criminal or administrative punishment for committing an act specified in Article 217 or Article 218 of the Criminal Law within two years, he commits the act again, and the amount of illegal gains is more than RMB 30,000 or the amount of sales is more than RMB 50,000;
(3) selling another person’s work or audio or video recording, where the total number of copies is more than one thousand;
(4) The value of the infringing copies that have not yet been sold or the number of infringing copies that have not yet been sold is more than three times the standards set forth in the first three items of this paragraph; or the value or number of infringing copies that have been sold is less than the standards set forth in the first three items of this paragraph, but the total value or number of infringing copies that have not yet been sold is more than three times the standards set forth in the first three items of this paragraph.
Article 15 Whoever commits the crime of copyright infringement as provided for in Article 217 of the Criminal Law and also sells the infringing copies, and this constitutes a crime, shall be convicted and punished for the crime of copyright infringement in accordance with the provisions of Article 217 of the Criminal Law.
If a person commits the crime of copyright infringement as provided for in Article 217 of the Criminal Law and knowingly sells the infringing copies of others’ works, and this constitutes a crime, he shall be punished for multiple crimes.
Article 16: Obtaining commercial secrets by means of illegal copying or other means shall be deemed as “theft” as provided for in Article 219, paragraph 1, item 1 of the Criminal Law; obtaining commercial secrets by means of unauthorized or unauthorized use of computer information systems or other means shall be deemed as “electronic intrusion” as provided for in Article 219, paragraph 1, item 1 of the Criminal Law.
Article 17: Infringement of trade secrets under any of the following circumstances shall be deemed to be a “serious circumstance” as provided for in Article 219 of the Criminal Law:
(1) causing losses of more than RMB 300,000 to the owner of the rights of the trade secrets;
(2) The amount of illegal gains from infringement of trade secrets is more than RMB 300,000;
(3) Having been subject to criminal or administrative punishment for committing an act specified in Article 219 or Article 219-1 of the Criminal Law within two years, he commits the act again, causing losses or illegal gains of more than RMB 100,000;
(4) Other circumstances of a serious nature.
If the infringement of trade secrets directly leads to the bankruptcy or closure of the rights holder of the trade secrets due to major operational difficulties, or the amount is more than ten times the standard specified in the preceding paragraph of this article, it shall be deemed as “particularly serious circumstances” as stipulated in Article 219 of the Criminal Law.
Article 18 The “amount of loss” for infringement of trade secrets as provided for in this Interpretation shall be determined in the following manner:
(1) Where the business secrets of the right holder are obtained by improper means and have not yet been disclosed, used or allowed to be used by others, the amount of loss may be determined based on the reasonable licensing fee for the business secrets;
(2) If a person obtains the right holder’s trade secrets by unfair means and then discloses, uses or allows others to use the trade secrets, the amount of loss may be determined based on the loss of profits caused by the right holder’s infringement. However, if the amount of loss is lower than the reasonable license fee for the trade secrets, it shall be determined based on the reasonable license fee;
(3) If a person violates the obligation to keep confidentiality or the right holder’s request to keep business secrets confidential and discloses, uses or allows others to use the business secrets in his possession, the amount of loss may be determined based on the loss of profits caused by the right holder due to the infringement;
(4) Where a person knowingly obtains, discloses, uses or allows others to use a trade secret by improper means or in violation of the obligation to keep the trade secret or the right holder’s requirement to keep the trade secret, but still obtains, discloses, uses or allows others to use the trade secret, the amount of loss may be determined based on the loss of profits caused by the right holder due to the infringement;
(5) If a trade secret has become known to the public or has been lost due to an act of infringing a trade secret, the amount of loss may be determined based on the commercial value of the trade secret. The commercial value of a trade secret may be determined based on a combination of factors such as the research and development costs of the trade secret and the benefits of implementing the trade secret.
The loss of profits caused by infringement of the rights holder specified in the second to fourth items of the preceding paragraph can be determined by multiplying the total number of product sales reductions caused by the infringement by the reasonable profit of each product of the rights holder; if the total number of product sales reductions cannot be determined, it can be determined by multiplying the sales volume of the infringing products by the reasonable profit of each product of the rights holder. If the trade secret is used for other business activities such as services, the amount of loss can be determined based on the reasonable profit reduced by the rights holder due to infringement.
The remedial expenses incurred by the right holder of the trade secret to mitigate the losses to business operations or business plans or to restore the security of computer information systems or other systems should be included in the losses caused to the right holder of the trade secret.
Article 19 The “amount of illegal gains” from infringement of trade secrets as provided for in this Interpretation refers to the value of property or other property benefits obtained by disclosing or allowing others to use trade secrets, or the profits obtained by using trade secrets. Such profits can be determined by multiplying the sales volume of the infringing products by the reasonable profit of each infringing product.
Article 20: If a foreign institution, organization or individual steals, spies on, buys or illegally provides commercial secrets and the circumstances specified in Article 17 of this Interpretation exist, it shall be deemed as “serious circumstances” as specified in Article 219 of the Criminal Law.
Article 21 In criminal proceedings, if a party, defender, litigation agent or non-party applies in writing for confidentiality measures to be taken with respect to evidence or materials concerning commercial secrets or other commercial information that needs to be kept confidential, necessary confidentiality measures shall be taken, such as organizing the litigation participants to sign a confidentiality commitment letter, based on the circumstances of the case.
Anyone who violates the requirements of the confidentiality measures in the preceding paragraph or the confidentiality obligations stipulated by laws and regulations shall bear corresponding responsibilities in accordance with the law. Anyone who discloses, uses or allows others to use commercial secrets accessed or obtained in criminal proceedings without authorization shall be held criminally liable in accordance with the law if a crime is constituted.
Article 22 Anyone who knowingly commits a crime of intellectual property infringement by another person and commits any of the following acts shall be treated as a co-offender, except where otherwise provided by law or judicial interpretation:
(1) Providing assistance in producing or manufacturing the main raw materials, auxiliary materials, semi-finished products, packaging materials, machinery and equipment, labels and logos, production technology, formulas, etc. for the production or manufacture of infringing products;
(2) Providing loans, funds, accounts, licenses, payment settlement and other services;
(3) Providing production or business premises or transportation, warehousing, storage, express delivery, mailing and other services;
(4) Providing technical support such as Internet access, server hosting, network storage, and communication transmission;
(5) Other circumstances of assisting crimes of infringement of intellectual property rights.
Article 23: Where any of the following circumstances exist in the commission of a crime of infringement of intellectual property rights, a heavier punishment shall generally be imposed as appropriate:
(1) Mainly engaged in infringement of intellectual property rights;
(2) counterfeiting registered trademarks of goods or services such as emergency and disaster relief supplies or epidemic prevention materials during major natural disasters, accidents, disasters, or public health incidents;
(3) Refusing to hand over illegal gains.
Article 24: Where a crime of infringement of intellectual property rights exists and any of the following circumstances exists, a lighter punishment may be given in accordance with law:
(1) Those who plead guilty and accept punishment;
(2) the right holder has obtained forgiveness;
(3) Obtaining the right holder’s business secrets by improper means but not disclosing, using or allowing others to use them.
If the circumstances of the crime are minor, prosecution may be waived or criminal punishment may be exempted in accordance with the law. If the circumstances are significantly minor and the harm is not serious, they shall not be treated as crimes.
Article 25: Those who commit crimes of infringement of intellectual property rights shall be sentenced to a fine in accordance with the law by taking into account the amount of illegal gains from the crime, the amount of illegal business, the amount of losses caused to the right holder, the number of infringing and counterfeit goods and the social harm, etc.
The amount of the fine is generally determined to be between one and ten times the amount of the illegal income. If the amount of the illegal income cannot be ascertained, the amount of the fine is generally determined to be between 50% and one time the amount of the illegal business. If both the amount of the illegal income and the amount of the illegal business cannot be ascertained, if a sentence of less than three years of fixed-term imprisonment, criminal detention or a fine is imposed, the amount of the fine is generally determined to be between RMB 30,000 and RMB 1 million; if a sentence of more than three years of fixed-term imprisonment is imposed, the amount of the fine is generally determined to be between RMB 150,000 and RMB 5 million.
Article 26 If an organization commits any of the acts specified in Articles 213 to 219 of the Criminal Law, the organization shall be sentenced to a fine, and the directly responsible supervisors and other directly responsible persons shall be punished in accordance with the conviction and sentencing standards prescribed in these Interpretations.
Article 27 Except in special circumstances, goods with counterfeit registered trademarks, illegally manufactured registered trademark signs, infringing copies, and materials and tools mainly used to manufacture goods with counterfeit registered trademarks, registered trademark signs or infringing copies shall be confiscated and destroyed in accordance with the law.
If the above-mentioned items need to be used as evidence in civil or administrative cases, they may be destroyed upon application by the right holder after the civil or administrative case is concluded or after the evidence is fixed by means of sampling, photographing, etc.
Article 28 The “amount of illegal business” referred to in this interpretation refers to the value of the infringing products manufactured, stored, transported, and sold by the perpetrator in the process of committing an act of infringement of intellectual property rights. The value of the infringing products that have been sold shall be calculated according to the actual sales price. The value of the infringing products that have not yet been sold shall be calculated according to the actual sales average price of the infringing products that have been ascertained. If the actual average sales price cannot be ascertained, it shall be calculated according to the marked price of the infringing products. If the actual sales price cannot be ascertained or the infringing products have no marked price, it shall be calculated according to the market median price of the infringed products.
The “value of goods” referred to in this interpretation shall be determined in accordance with the value of the unsold infringing intellectual property rights products stipulated in the preceding paragraph.
The “sales amount” referred to in this interpretation refers to all illegal income obtained by and owed to the person from the sale of infringing products during the process of committing acts of infringement of intellectual property rights.
The “amount of illegal income” referred to in this interpretation refers to the total illegal income obtained by and owed to the perpetrator after selling products that infringe intellectual property rights, minus the purchase price of raw materials and products sold; if services are provided, minus the purchase price of products used in the service. If a person makes a profit by charging service fees, membership fees or advertising fees, the fees collected shall be deemed as “illegal income”.
Article 29: Where intellectual property rights infringement is committed multiple times and has not been dealt with but should be prosecuted according to law, the amounts and quantities involved in conviction and sentencing shall be calculated cumulatively.
For products that have been completed but have not yet been affixed with counterfeit registered trademark logos or have not yet been fully affixed with counterfeit registered trademark logos, if there is evidence that the product will counterfeit another person’s registered trademark, its value will be included in the amount of illegal business operations.
Article 30 Where a people’s court accepts a criminal private prosecution case involving infringement of intellectual property rights in accordance with law, and where a party is unable to obtain evidence due to objective reasons but is able to provide relevant clues when filing a private prosecution and applies to the people’s court for the evidence, the people’s court shall obtain the evidence in accordance with law.
Article 31 This interpretation shall come into force on April 26, 2025.
USPTO Reshapes Discretionary Denials for Post-Grant Proceedings
The US Patent and Trademark Office (USPTO) recently issued two memoranda reshaping the Patent Trial and Appeal Board’s (PTAB) approach to discretionary denials for parallel proceedings.
First Memo: Guidance on USPTO’s Recission of Fintiv Memo
The first memo, issued on March 24 by PTAB Chief Administrative Patent Judge Scott Boalick, clarifies how discretionary denials should be handled following the USPTO’s recission of the Fintiv Memo. Going forward, the Board will once again apply the Fintiv factors to determine whether it should exercise its discretion to deny institution for any post-grant proceeding challenging a patent that has been asserted in a parallel proceeding, including in the US International Trade Commission (ITC). Those six factors include:
Whether the court granted a stay or evidence exists that one may be granted if a proceeding is instituted.
Proximity of the court’s trial date to the Board’s projected statutory deadline for a final written decision.
Investment in the parallel proceeding by the court and parties.
Overlap between issues raised in the petition and parallel proceeding.
Whether the petitioner and the defendant in the parallel proceeding are the same party.
Other circumstances that impact the Board’s exercise of discretion, including the merits.
The memo makes clear that no single Fintiv factor is dispositive; the Board must reach a decision by conducting a holistic Fintiv analysis that weighs all the relevant factors. That said, Sotera stipulations will remain highly relevant. The Board may also consider any record evidence concerning the proximity of the Board’s final written decision to the district court’s trial date or the ITC’s final determination target date.
Second Memo: Interim Process for PTAB Institution Decisions
The second memo, issued on March 26, put forward interim procedure for institution decisions will be bifurcated into (1) discretionary considerations and (2) non-discretionary considerations and merits. Under the new procedure, the USPTO director will now consult at least three PTAB judges to determine whether a discretionary denial of institution is appropriate. If denial is appropriate, the director will simply issue a decision stating such. If denial of institution is not appropriate, the proceeding will continue under a new three-member panel, according to the normal procedure.
The interim procedure puts forward a new briefing schedule as a matter of right in addition to the normal, existing briefing schedule. The brief seeking discretionary denial of institution from the patent owner must be filed within two months of the Notice of Filing of any post-grant petition and is limited to 14,000 words. The opposition brief must be a month later and is also limited to 14,000 words. If good cause is shown, a reply brief of 5,600 words can be filed.
The briefs can address all the relevant factors under PTAB precedent, including the above described Fintiv factors. The memo enumerates specific factors, including (1) whether the PTAB or another forum has already adjudicated the validity or patentability of the challenged patent claims, (2) whether there have been changes in the law or new judicial precedent issued since issuance of the claims that may affect patentability, (3) the strength of the unpatentability challenge, (4) the extent of the petition’s reliance on expert testimony, (5) settled expectations of the parties, such as the length of time the claims have been in force, (6) compelling economic, public health, or national security interests, and (7) any other considerations bearing on the director’s discretion. One other consideration will likely be the ability of the PTAB to meet its “workload needs.”
While the memoranda do not explicitly predict the results of the new interim procedure, a rise in discretionary denials can be expected. The combination of the bifurcation of discretionary denials and the consistency in which the ITC sets target dates ahead of the PTAB estimated final written decision increases the probability of denials. Additionally, because the briefing schedule does not replace the normal briefing schedule, there should be no expected increased efficiency for patent owners from the new bifurcation procedure. Factoring in the tight three-month briefing window, any petition for post-grant review would need to be filed within one to two months of any ITC proceeding to have a chance of avoiding discretionary denial of institution.
Listen to this article
Delete All IP Law? Really?
By now, everyone should know about the X post heard around the intellectual property world. On April 11, Jack Dorsey, co-founder of Twitter and Block, posted these four words : “delete all IP law.” A few hours later, Elon Musk chimed in with “I agree.” Over the next few days, the media was full of reactions from tech and legal luminaries. Some tech celebrities agreed. “Jack has a point,” posted Chris Messina, ironically on X rival Bluesky. Members of the IP legal community who were quoted in the media objected strongly, as one might expect.
When I asked several members of the IP legal community if they wanted to comment, the response I got from some was cool.
“These offhand tweets have received far more media attention than they deserve,” said Prof. Edward Lee of Santa Clara University School of Law, adding, “Let’s talk when Block and Tesla allow competitors to freely use their trademarks and trade secrets.”
The professor has a point. Perhaps X posts, shot from the hip, aren’t worth the paper they aren’t written on. But, as documented recently in the Washington Post, “[s]ome X posts appear to have influenced the White House.”. Tech Crunch’s Anthony Ha observed, “the line between a random conversation on Twitter/X and actual government policy is thinner than it used to be.”. And there is strong pressure from Silicon Valley to weaken copyright protection to allow unfettered training of the large language models that are the backbone of Artificial Intelligence (AI). As glib as Dorsey and Musk’s X posts might be, they need to be addressed seriously.
To begin with, my colleague Jim Ko explains in his article, “Delete All IP Law”? Why the Tech Titans Want to Pull Up the Ladder Behind Them,” that intellectual property rights were considered so important to the development of America that they were enshrined in the Constitution by the Founding Fathers. Article I, Section 8, Clause 8 gives Congress the power “[t]o promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries.”
Building on that, Robert Sterne of Washington, D.C.’s Sterne, Kessler, Goldstein & Fox, PLLC, states, “having represented literally hundreds of startups, emerging companies, and universities – the lifeblood of the USA innovation ecosystem – I can say with absolute certainty that a strong, robust, and predictable intellectual property regime is essential for their commercial success. Any weakening of the USA IP system would disadvantage the future of the nation as China and the European Union continue to evolve and strengthen their IP systems to generate jobs, wealth, and security.”
Scott Kelly, a partner at Banner Witcoff in Washington, zeroes in on patent law, which he says “isn’t perfect, but it solves a critical problem. Scientific progress does not benefit from innovators keeping their inventions secret when it is trivial to copy someone else’s ingenuity. Patents incentivize a proactive approach to problem solving, and disclosure of those solutions, rather than a world where the best strategy is to let others make the investment and figure it out for you.”
The economic consequences of deleting all IP law would be severe. Russell Beck of Beck Reed Riden, LLP, of Boston notes that “IP makes up 90% of the value of S&P 500 companies”, citing Ocean Tomo’s Intangible Asset Market Value Study. He says that “eliminating IP rights would erase that value, stifle innovation, strip the US of its global competitiveness, and cripple the US economy. ‘Deleting’ IP doesn’t level the playing field for AI – it removes the field entirely. It replaces commercial ethics and rights with corporate espionage and IP theft.”
Having recently returned from The Sedona Conference’s Global IP Litigation Conference in The Hague, I am particularly sensitive to the international ramifications of ill-considered attacks on intellectual property. We are already making it difficult for foreign students, artists, and researchers to work in the United States through visa restrictions and academic funding cuts. We would exacerbate the problem if inventors and creators – and the capital backing them – decided that to protect their rights, they need to relocate to a jurisdiction with stronger patent, copyright, and trade secret laws. Many commentators have noted that a weakening of trademark protections would cause a flood of knockoff products into the domestic market, eroding consumer confidence.
Observers are correct to note that intellectual property law isn’t perfect, but we can’t afford to throw it all out. There are tensions in patent law between high tech, pharma, and manufacturing sectors. Trade secrets are becoming more important to startups, but restrict labor mobility. As a retired librarian, I find modern digital copyright restrictions difficult to square with traditional concepts of access to knowledge, but I am also anxious about the future for the musicians and videographers in my family.
At The Sedona Conference, we stand both for the “rule of law” and strive to move the law forward “in a reasoned and just way” through dialogue and consensus. It’s not easy, and it requires a lot of listening to understand different viewpoints and find common ground. It requires more than a four-word post with potentially dire consequences.
Maximizing Recovery in Trade Secret Cases: A Guide to Damages and Remedies
The landscape of trade secret damages has evolved dramatically in recent years, with courts awarding unprecedented sums in cases of proven misappropriation.
Recent verdicts, including the $604.9 million award in Propel Fuels v. Phillips 66 (over confidential data, proprietary strategies, and business intelligence regarding low carbon fuels) and the $452 million verdict in Insulet Corp v. EOFlow (involving tubeless insulin pump technology), demonstrate the potential for substantial recovery. However, securing such awards requires a sophisticated understanding of available remedies and a carefully planned approach to proving damages.
Understanding Available Damages Under the DTSA
The federal Defend Trade Secrets Act (DTSA) provides several distinct paths to monetary recovery, each serving different purposes and requiring different types of proof.
At the foundation are actual damages, which compensate for direct losses caused by misappropriation. These often begin with lost profits from sales diverted to competitor,s but can encompass much more. Companies frequently incur substantial costs developing their trade secrets, implementing remedial measures after theft, investigating the scope of misappropriation, and rebuilding damaged customer relationships.
All of these expenses may be recoverable as actual damages when properly documented and linked to the defendant’s misconduct.
The challenge in proving actual damages lies in establishing causation. Courts require evidence that specific losses resulted from the misappropriation rather than from other market factors or business conditions. This often necessitates careful analysis of historical performance data, market conditions, and customer behavior patterns to isolate the impact of the misappropriation.
Unjust enrichment provides an additional (or alternative) path to recovery by focusing on the defendant’s gains rather than the plaintiff’s losses. A plaintiff may recover damages for any unjust enrichment caused by the misappropriation of the trade secret that is not addressed in computing damages for their actual loss.
This approach can be particularly valuable when the defendant’s use of the trade secret generated profits beyond what the plaintiff lost. For instance, a defendant might have reached new markets or customers that the plaintiff wouldn’t have served, making unjust enrichment damages potentially larger than lost profits alone.
The scope of unjust enrichment can be quite broad. Beyond direct profits from sales, courts recognize that defendants may benefit from reduced development costs, accelerated time to market, improved manufacturing efficiency, and enhanced customer relationships. These benefits can be quantified and recovered even when they haven’t yet translated into direct profits.
As an alternative to actual damages and unjust enrichment, courts may award a reasonable royalty. This approach attempts to determine what a willing licensee would have paid a willing licensor for the right to use the trade secret.
Courts examining a reasonable royalty award of damages typically consider numerous factors, including:
Comparable licensing arrangements in the industry;
The competitive relationship between the parties;
The value of the secret to both parties;
Development costs saved by the defendant;
The portion of profit attributable to the trade secret and
Expert analysis of market conditions and value.
Enhanced Recovery Options
Beyond compensatory damages, trade secret law provides for potential recovery of enhanced damages and attorney’s fees in cases of particularly egregious conduct. When misappropriation is willful and malicious, courts can award exemplary damages up to twice the amount of compensatory damages.
Evidence of deliberate theft, attempts to cover up misappropriation, violation of court orders, or continued use after receiving notice can support such awards.
Attorneys’ fees represent another important component of potential recovery.
These become available in cases involving willful and malicious misappropriation or bad faith litigation conduct. The availability of attorneys’ fee awards can significantly impact litigation strategy and settlement dynamics, particularly in cases where proving damages may be challenging but liability (misconduct) is clear.
Permanent Injunctive Relief and Alternative Remedies
While monetary damages often take center stage, injunctive relief remains a crucial remedy in trade secret cases.
Parties typically begin a trade secret case by seeking a temporary restraining order and then a preliminary injunction. These orders prohibit a defendant from using a trade secret while litigation is pending up through trial.
However, at the conclusion of a case, parties can also seek an injunction that will prohibit the disclosure of the trade secret permanently and/or the use of the trade secret. Courts typically will permanently enjoin a defendant from sharing a trade secret, but an injunction on use of the trade secret is normally less permanent. Courts structure “permanent” injunctions regarding the use of a trade secret around the concept of a “head start” period – the time it would have taken the defendant to independently develop the trade secret. This approach aims to eliminate any unfair advantage gained through misappropriation, while recognizing that trade secrets don’t confer perpetual monopolies.
In some situations, courts may order ongoing royalty payments instead of a permanent injunction. This usually occurs when completely barring use of the trade secret would be inequitable or against the public interest. For instance, if the defendant has incorporated the trade secret into products serving essential public needs, a court might prefer a royalty solution over an injunction.
Building a Strong Damages Case
Successfully proving damages requires careful preparation from the earliest stages of the case. Early case assessment should examine potential damages theories and identify necessary evidence before critical information is lost. This initial analysis helps guide discovery requests, identify necessary experts, and make strategic decisions about settlement parameters.
Selection of expert witnesses proves crucial in most trade secret cases. Beyond technical expertise, damages experts need strong communication skills and the ability to present complex financial analyses in understandable terms.
Damages experts should be involved early enough to help shape discovery and document preservation efforts.
Documentation becomes particularly important in trade secret cases because of the need to establish both the secret’s value and the impact of its misappropriation.
Companies should maintain detailed records of development costs, efforts, and associated expenses to maintain secrecy, value derived from the secret, affected customer relationships, market impact, and remedial measures taken. This documentation helps demonstrate both the existence of damage and its quantum.
Strategic Considerations for Maximum Recovery
Several strategic considerations can significantly impact ultimate recovery in trade secret cases.
First, maintaining multiple theories of recovery throughout trial provides maximum flexibility. Courts typically allow plaintiffs to elect their preferred theory of recovery (actual damages vs. unjust enrichment vs. reasonable royalty) after all evidence is presented, so preserving all viable theories until that point maximizes potential recovery.
The international reach of trade secret claims presents another strategic consideration. The DTSA can reach conduct outside the United States when any act in furtherance of misappropriation occurs domestically. This allows recovery of damages from foreign sales or use when there’s a U.S. nexus, potentially expanding the scope of recovery significantly.
Timing considerations permeate trade secret damages analysis. Key questions include when misappropriation began, when it should have been discovered, the appropriate “head start” period, and the commercial life of the secret. These temporal factors can significantly impact the calculation of both damages and the scope of injunctive relief.
Looking Forward
The complexity of trade secret damages demands careful attention from the outset of any potential case. Success requires understanding available theories of recovery, maintaining necessary documentation, and building strong expert support.
While recent high-value verdicts demonstrate the potential for substantial recovery, achieving such results requires methodical preparation and strategic presentation of damages evidence.
Our final article will explore preventive measures and best practices for protecting trade secrets before misappropriation occurs, completing our comprehensive examination of trade secret protection and enforcement.
Trade Secret Law Evolution Podcast, Episode 76: Two Circuit Cases on Trade Secret Identification, Proof of Misappropriation and Contractual Damages Waivers [Podcast]
In this episode, Jordan Grotzinger discusses a recent Fifth Circuit case that addressed trade secret identification and proof of misappropriation at trial, and an Eleventh Circuit case addressing whether and how trade secret misappropriation damages can be limited by contract.
Toward Digital-Ready Design Protection: The New EU Design Act
The European Union has undertaken a comprehensive modernization and harmonization of its design protection framework. The reform, commonly referred to as the “Design Act,” comprises two legislative measures: the Design Regulation (Regulation (EU) 2024/2822, which amends Regulation (EC) No 6/2002 and repeals Regulation (EC) No 2246/2002) and the Design Directive (Directive 2024/2823, which replaces Directive 98/71/EC).
The EU aims to align design protection with technological advancements, particularly in the realm of digital and animated designs. At the same time, the system is being simplified to better serve businesses and designers while strengthening enforcement mechanisms and promoting harmonization.
The Design Regulation deals with the EU Design (which is the new name for the former Community Design) and its registration, protection and enforcement, while the Design Directive sets mandatory requirements for the national designs that each Member State will need to implement into national legislation.
Key Changes at a Glance
The Design Act seeks to align EU design protection with the demands of the digital age while enhancing its accessibility and user-friendliness:
Digital and animated designs are explicitly protected in order to ensure comprehensive protection in the digital and virtual space.
For both the register for EU Designs and national Designs, protection of registered designs has been increased. A design that is registered in the EU register or a national register is deemed to be valid and is deemed to be owned by the registered owner.
Application procedures are streamlined within the EU.
Enforcement rights are strengthened.
Design owners gain new tools for legal certainty.
Specific market needs — such as component part availability— are addressed through the introduction of a repair clause, exempting repair parts from protection.
Replacement of the term “Community design” with “EU design.”
A circled D symbol (Ⓓ) can be used to indicate design protection on products.
Implementation Phases
The reforms the Design Act introduces will be implemented progressively across three phases.
Phase 1 (from May 1, 2025): Initial Practical Changes
Simplified and Unified Registration Process
The requirement for “unity of class” in multiple design applications is abolished, allowing multiple designs from different Locarno classes to be combined into a single application (capped at 50 designs per application), reducing administrative effort and costs.
(Art. 35 ff. Design Regulation/ Art. 27 Design Directive)
Updated Fee Structure
A single, unified application fee simplifies the cost structure. Renewal fees are increased but better reflect the commercial value of extended design protection. While the registration itself will not become more expensive, the renewal fees after the fifth year will increase. However, because the “unity of class” requirement is abolished, multiple applications will be more cost-efficient than before.
(Design Regulation, Annex I)
Amended Renewal Process
Registered designs must be renewed within the six-month period before expiration – this includes both the request and the fee payment.
(Art. 50d Design Regulation/ Article 32 Design Directive)
Enhanced Enforcement Powers
New rights may enable design owners to act against unauthorized 3D printing of their designs and counterfeit goods passing through the EU (transit goods), closing enforcement gaps and enhancing the overall enforcement framework.
(Art. 19 Design Regulation/ Art. 16 Design Directive)
Design Symbol Introduction
Design owners may now use the “Ⓓ” symbol to indicate protected designs, similar to trademarks (®) or copyrights (©) to deter potential infringers in the field of design law. Additional identifiers, such as registration numbers or links to the EU design register, may also be used.
(Art. 26a Design Regulation/ Art. 24 Design Directive)
Phase 2 (from July 1, 2026): Expanding the Scope of Protection
Expanded Definition of Designs
The definition of protectable designs now explicitly encompasses dynamic features such as motion, transitions, and animation – addressing the growing prominence of digital design.
(Art. 3 (1) Design Regulation; Art. 2 (3) Design Directive)
New Representation Requirements
The European Union Intellectual Property Office executive director will determine formats, numbering, and technical specifications for both static and animated design representations, ensuring clarity and consistency in registration.
(Art. 36 Design Regulation/ Art. 26 Design Directive)
Phase 3 (by Dec. 9, 2027): Market-Specific Adjustments
Introducing a Repair Clause
Component parts of complex products – where design is dictated by the appearance of the whole product and the component part used solely to restore that appearance (e.g., automotive body parts) – are excluded from design protection. However, an eight-year transitional period, ending on Dec. 9, 2032, preserves the existing protection for such parts during that time.
(Art. 20a Design Regulation/ Art. 19 Design Directive)
Conclusion
The EU’s Design Reform introduces a modernized legal framework that seeks to meet the evolving challenges of digitalization, enhance legal certainty, simplify administrative processes, and strengthen enforcement capabilities.
While EU trademark law has long been aligned across member states, design law had previously lagged behind in terms of consistency and uniformity. With the Design Act package, the EU is now taking further steps toward achieving a more coherent and fully harmonized design protection system.
Businesses and designers are encouraged to begin preparing for the phased changes now to enhance compliance and to leverage the new legal opportunities.
China’s State Administration for Market Regulation Releases RFC for Regulations on the Protection of Trade Secrets

On April 25, 2025, China’s State Administration for Market Regulation (SAMR) released the draft Regulations on the Protection of Trade Secrets for comment (商业秘密保护规定(征求意见稿)). Comments are due May 25, 2025. This draft updates the 1998 version with necessary revisions due to the march of technology. As explained by SAMR:
The revision and promulgation of the “Regulations on the Protection of Trade Secrets” is an urgent need to adapt to the new situation and new challenges of trade secret protection. With the development and changes of the domestic and international economic situation, the “Several Provisions on Prohibition of Infringement of Trade Secrets” revised in 1998 has lagged behind the needs of practice and needs to be revised and improved in line with the times. On the one hand, with the rapid development of the digital economy, digital information has become an important carrier of corporate trade secrets. The huge changes in trade secrets in the digital age have put forward higher technical requirements for corporate self-protection and administrative law enforcement, and there is an urgent need for detailed and clear rules and guidance. On the other hand, in recent years, the world’s major developed economies have issued some new institutional regulations on trade secret protection, and major multilateral economic and trade agreements have also put forward clear requirements for trade secret protection. Improving the system of trade secret protection is an inevitable requirement to connect with international high-standard economic and trade rules and better respond to the new trend of global market competition.
A translation follows. The original text and drafting notes are available here (Chinese only).
Chapter I General Provisions
Article 1 These Regulations are formulated in accordance with the Anti-Unfair Competition Law of the People’s Republic of China (hereinafter referred to as the “Anti-Unfair Competition Law”) and other relevant laws, administrative regulations, and relevant documents of the Party Central Committee and the State Council in order to strengthen the protection of trade secrets, stop acts of infringement of trade secrets, protect the legitimate rights and interests of trade secret rights holders and related entities, encourage research and development and innovation, maintain a fair and competitive market order, and serve the high-quality development of the economy and society.
Article 2 The acquisition, disclosure and use of trade secrets shall follow the principles of voluntariness, equality, fairness and good faith, and comply with laws, regulations and business ethics.
Article 3 The market supervision and management department is responsible for the organization, coordination, and guidance of the protection of trade secrets and the administrative law enforcement of trade secret infringements.
Chapter II Definition of Trade Secrets
Article 4 The term “trade secrets” as used in these Regulations refers to commercial information such as technical information, business information, etc. that is not known to the public, has commercial value, and for which the right holder has taken corresponding confidentiality measures.
Information related to technology, such as structures, raw materials, components, formulas, materials, samples, styles, designs, new plant variety propagation materials, processes, methods or their steps, algorithms, data, computer programs and related documents, may be deemed to constitute the technical information referred to in the first paragraph of this Article.
Creativity, management, sales, finance, plans, samples, bidding materials, customer information, data and other information related to business activities may be deemed to constitute the business information referred to in the first paragraph of this Article.
Article 5 The customer information referred to in these regulations includes the customer’s name, address, contact information, and transaction habits, intentions, content and other information.
If an operator claims that specific customer information is a trade secret simply because it maintains a long-term and stable trading relationship with the specific customer, such claim will not be recognized.
If a customer conducts market transactions with an employee’s company based on trust in the employee personally, and after the employee leaves the company, it can be proved that the customer voluntarily chose to trade with the employee or his new company, it should be deemed that the employee did not use improper means to obtain the customer information of the original company.
Article 6 The term “not known to the public” as used in these Regulations means that the information was not generally known or easily accessible to relevant personnel in the field to which it belongs when the suspected infringement occurred.
Under any of the following circumstances, the relevant information may be deemed to be known to the public:
(1) The information is common knowledge or industry practice in the relevant field;
(ii) The information only involves the product’s dimensions, structure, materials, simple combination of components, etc., which can be directly obtained by relevant personnel in the field by observing the marketed products;
(3) The information has been publicly disclosed in public publications or other media;
(4) The information has been made public through public reports, exhibitions, etc.;
(5) Relevant personnel in the relevant field can obtain the information from other public channels.
If new information is formed by organizing, improving and processing information known to the public and meets the provisions of the first paragraph of this Article, it shall be deemed that the new information is not known to the public.
Article 7 The term “commercial value” as used in these Regulations means that the information has actual or potential commercial value because it is not known to the public and can bring commercial benefits or competitive advantages to the right holder.
If any of the following circumstances is met, the information can be deemed to bring commercial benefits or competitive advantages to the right holder, unless there is contrary evidence to prove that the information has no commercial value:
(1) The information brings economic benefits to the right holder;
(2) The information has a significant impact on the production and operation of the right holder;
(3) The right holder has paid a corresponding price, research and development costs or operating costs or other material inputs to obtain the information, which has brought the right holder a competitive advantage;
(iv) Other circumstances that can prove that the information can bring commercial benefits or competitive advantages to the right holder.
If the interim results formed in production and operation activities meet the requirements of the first paragraph of this Article, such results may be deemed to have commercial value.
Article 8 The “appropriate confidentiality measures taken by the right holder” as used in these Regulations refers to reasonable confidentiality measures taken by the right holder before an infringement occurs to prevent information leakage that are commensurate with factors such as the commercial value of the trade secret and the difficulty of independent acquisition.
If any of the following circumstances exists and the leakage of confidential information can be prevented under normal circumstances, it can be deemed that the right holder has taken “corresponding confidentiality measures”:
(1) Signing a confidentiality agreement or stipulating confidentiality obligations in a contract;
(2) Imposing confidentiality requirements on employees, former employees, suppliers, customers, visitors, etc. who have access to or obtain trade secrets through charters, training, rules and regulations, written notifications, etc.;
(3) Restricting visitors to factories, workshops and other production and operation sites involving confidential information or implementing differentiated management;
(4) distinguishing and managing trade secrets and their carriers by marking, classifying, isolating, encrypting, sealing, limiting the scope of persons who can access or obtain them, etc.;
(5) Taking measures such as prohibiting or restricting the use, access, storage, or copying of computer equipment, electronic equipment, network equipment, storage equipment, software, etc. that can access or obtain trade secrets;
(6) requiring a resigned employee to register, return, remove or destroy the trade secrets and their carriers that he or she has accessed or obtained, and to continue to bear the obligation of confidentiality;
(7) Other reasonable confidentiality measures are taken.
Chapter III Construction of Trade Secret Protection System
Article 9 Operators shall implement the principal responsibility for protecting trade secrets, strengthen self-protection awareness and capacity building, and actively take effective measures to strengthen internal control and compliance management of trade secrets protection such as confidential information, confidential areas, confidential personnel, and confidential carriers based on their own industry characteristics, technical requirements, and competitive advantages, and consciously resist infringements.
Article 10 Market supervision and administration departments are responsible for the organization, coordination, supervision, administration and service guidance of trade secrets protection. Through publicity and training, building service sites, improving law enforcement capabilities, and cultivating third-party service agencies, they help operators establish and improve trade secrets protection systems and promote the overall improvement of trade secrets protection levels.
Article 11 The market supervision and management department shall, together with relevant departments, provide legal consultation, policy guidance, risk warning, rights protection support and other services to operators, strengthen foreign-related rights protection guidance and assistance, guide operators to carry out trade secret protection work, and safeguard their own legitimate rights and interests.
The market supervision and management departments will work with the judicial departments to establish a rapid and coordinated protection mechanism for commercial secrets that involves information exchange, resource sharing, case consultation, and law enforcement coordination, and strengthen the effective connection between administrative protection and judicial protection.
Article 12 Industry organizations shall strengthen industry self-discipline, guide and regulate the legal competition of operators, strengthen guidance on operators to establish and improve internal management systems for the protection of trade secrets, coordinate the handling of trade secret infringement disputes, and cooperate with and assist supervisory and inspection departments in investigating and handling acts of infringement of trade secrets.
Industry organizations are encouraged to formulate trade secret protection standards and compliance guidelines for their industries under the guidance of government departments.
Article 13 The people’s governments of all regions shall strengthen leadership over the protection of trade secrets, strengthen the overall coordination and work guarantees of related major matters, strengthen the construction of trade secret protection capabilities, and promote the establishment and improvement of a trade secret protection system that integrates self-protection, administrative protection, and judicial protection of trade secrets.
Article 14 Encourage, support and protect all organizations and individuals to conduct social supervision on violations of trade secrets. Market supervision and management departments shall keep confidential the organizations and individuals who report and assist in investigating and punishing violations of trade secrets.
No organization or individual may fabricate facts of infringement of trade secrets to frame others or engage in blackmail, or abuse the right to report to disrupt the normal working order of market supervision and management departments.
Chapter IV: Infringement of Trade Secrets
Article 15 Any business operator or other natural person, legal person or unincorporated organization that individually or jointly infringes upon trade secrets or instigates, induces or assists others in infringing upon trade secrets shall be deemed to have infringed upon trade secrets as defined in these Regulations.
Article 16: Business operators and other natural persons, legal persons and unincorporated organizations shall not obtain the business secrets of the right holder by theft, bribery, fraud, coercion, electronic intrusion or other improper means.
Any of the following circumstances shall be deemed as an act of obtaining the right holder’s business secrets by improper means as stated in the first paragraph of this Article:
(1) Accessing, possessing or copying, without authorization, documents, articles, materials, raw materials or electronic data under the control of the right holder that contain trade secrets or from which trade secrets can be derived, in order to obtain the trade secrets of the right holder;
(2) Inducing, coercing or deceiving the employees or others of the right holder to obtain trade secrets for them by means of offering money or other property benefits, personal threats or traps;
(3) Accessing the digital office system, server, mailbox, cloud disk, application account or other electronic information system of the right holder without authorization or exceeding the scope of authorization to obtain trade secrets or implanting computer viruses to obtain their trade secrets;
(4) downloading a trade secret to an email address or other electronic device controlled by an individual without the permission of the trade secret right holder, or causing the trade secret to be out of the control of the right holder by other means;
(5) Taking other actions that violate the law or generally accepted business ethics to obtain the trade secrets of the right holder.
Article 17: Business operators and other natural persons, legal persons and unincorporated organizations shall not disclose, use or allow others to use the business secrets of the right holder obtained by improper means.
“Disclosure” as used in this article means the act of making a trade secret known to others in any manner that may damage the competitive advantage or economic interests of the right holder.
“Use” as used in this article means the direct use of trade secrets in production and operation activities, the use of trade secrets after modification or improvement, or the adjustment, optimization and improvement of relevant production and operation activities based on trade secrets.
Article 18 Operators and other natural persons, legal persons and unincorporated organizations shall not violate confidentiality obligations stipulated by law, agreement or determined by effective judicial documents, or violate the requirements of the right holder to maintain confidentiality of commercial secrets, and disclose, use or allow others to use commercial secrets in their possession.
Any of the following circumstances shall be deemed as confidentiality obligations or requirements of the right holder to keep business secrets as referred to in this article:
(1) Agreements on maintaining business secrets concluded with the right holder in employment contracts, confidentiality agreements, cooperation agreements, etc.;
(2) unilateral confidentiality requirements made by the right holder to the counterparty who knows the trade secret, including but not limited to the counterparty who knows the trade secret through contractual relationship, and the counterparty who knows the trade secret through participation in research and development, production, inspection, etc.;
(3) In the absence of a confidentiality agreement, employment contract, cooperation agreement, etc., the rights holder’s other requirements for employees, former employees, partners, etc. to maintain business secrets through other rules and regulations or reasonable confidentiality measures;
(4) Knowing or should have known that the information he obtained was the right holder’s trade secret based on the principle of good faith, the nature of the contract, the purpose of the contract, the contract conclusion process, transaction practices, etc.;
(5) Other circumstances under which confidentiality obligations are imposed as provided for by laws and administrative regulations.
Article 19: Business operators and other natural persons, legal persons and unincorporated organizations shall not instigate, induce or assist others in violating confidentiality obligations or the rights holder’s requirements for maintaining confidentiality of business secrets, or obtaining, disclosing, using or allowing others to use the rights holder’s business secrets.
Any of the following circumstances shall be deemed as an infringement of trade secrets:
(1) intentionally using words, actions or other methods to persuade, advise or encourage others to violate confidentiality obligations or violate the rights holder’s requirements for maintaining business secrets;
(2) Inducing others to violate confidentiality obligations or violate the rights holder’s requirements for maintaining business secrets by means of promises of positions, material rewards, etc.;
(3) Providing convenience in various ways for others to violate confidentiality obligations or the rights holder’s requirements for maintaining confidentiality in order to obtain, disclose, use or allow others to use the rights holder’s trade secrets.
Article 20 If a third party knowingly or should have known that the employees, former employees or other entities or individuals of the trade secret right holder have committed any illegal act listed in Articles 16, 17, 18 or 19 of these Regulations, and still obtains, discloses, uses or allows others to use the trade secret, it shall be deemed as an infringement of the trade secret.
Article 21 The following acts shall not constitute infringement of trade secrets:
(1) Independent discovery or independent research and development;
(2) Obtaining relevant technical information of a product by disassembling, mapping, analyzing, etc. a product lawfully obtained from a public channel through technical means;
(3) Employees, former employees or partners of the trade secret right holder or holder disclose trade secrets to state organs and their staff for the purpose of exposing illegal or criminal acts, safeguarding national security and social public interests, etc.;
(4) Other circumstances that do not constitute infringement of trade secrets as provided for by laws and administrative regulations.
Chapter V Investigation and Punishment of Suspected Trade Secrets Infringement
Article 22: The market supervision and administration departments at or above the county level where the infringement of trade secrets occurs or where the rights holder is located shall be responsible for investigating and handling the infringement of trade secrets. If two or more market supervision and administration departments have jurisdiction and a dispute arises, they shall report to the common higher-level market supervision and administration department for designation of jurisdiction.
Article 23: The following entities may, as the trade secret rights holders, report infringements to the market supervision and administration department:
(1) the owner of the trade secret;
(2) the licensee of an exclusive license contract for the use of a trade secret;
(3) the licensee of a contract for exclusive use of a trade secret;
(4) an authorized person who has been authorized in writing by the owner of the trade secret.
Article 24 When a right holder believes that his or her trade secrets have been infringed and reports the infringement to the market supervision and management department, he or she shall provide preliminary evidence materials such as the commercial information he or she possesses meets the statutory requirements for trade secrets and the infringement of his or her trade secrets.
Materials required to determine that a trade secret meets the statutory requirements include:
(1) the process and time of formation of the trade secret;
(2) evidence materials on the specific content, carrier and form of expression of the trade secret that are not known to the public;
(3) the commercial value of the trade secret;
(4) the confidentiality measures taken to protect the trade secret;
(5) other evidential materials that the right holder believes he or she enjoys the rights.
If the right holder submits any of the following materials, it shall be deemed that it has provided preliminary evidence to reasonably indicate that its trade secrets have been infringed:
(1) There is evidence that the suspected infringer has channels or opportunities to obtain trade secrets, and the information used by the suspected infringer is substantially the same as the trade secret of the right holder;
(2) There is evidence that the suspected infringer has channels or opportunities to obtain trade secrets, and the confidentiality facilities have been destroyed by the suspected infringer by improper means;
(3) There is evidence that the trade secret has been actually obtained by the suspected infringer;
(4) There is evidence that the trade secret has been disclosed or used by the suspected infringer or is at risk of being disclosed or used;
(5) There is other evidence showing that the trade secret has been infringed by the suspected infringer.
Article 25 The right holder or the suspected infringer may entrust an appraisal institution to conduct appraisals on specialized matters such as whether the right holder’s information is known to the public and whether the information used by the suspected infringer is substantially the same as the right holder’s information.
The right holder or suspected infringer may entrust a person with specialized knowledge to provide opinions on specialized matters such as whether the right holder’s information is known to the public.
The right holder and the suspected infringer may explain to the market supervision and management department the appraisals or opinions they provide.
In the process of investigating and handling cases of commercial secret infringement, the market supervision and management department may suggest that the right holder conduct an appraisal on specialized matters such as whether the technical information involved is known to the public, whether the information used by the suspected infringer is substantially the same as the right holder’s information, etc.
Article 26 Where an infringement of a trade secret involves computer software, a judgment may be made as to whether the two are substantially identical based on whether the algorithm, software documentation, source code or target program of the trade secret is identical to the software involved in the alleged infringement, or whether the target program or source code of the computer software involved in the alleged infringement contains computer software-specific content for which the right holder claims the trade secret, or whether the software results (including software interface, operating parameters, database structure, etc.) are identical to the trade secret.
Article 27 Suspected infringers, interested parties, other relevant entities and individuals shall truthfully provide relevant evidence to the market supervision and management department.
If it can be proved that the information used by the suspected infringer is substantially the same as the business secret claimed by the right holder, and that the suspected infringer has the conditions to obtain the business secret, but the suspected infringer cannot or refuses to provide evidence that the information used was legally obtained or used, the market supervision and management department may determine that the suspected infringer has committed an infringement based on the relevant evidence.
Article 28 Upon application by the right holder and provision of preliminary evidence, the market supervision and administration department may seal and seize evidence that may be identified as trade secret infringement during the law enforcement investigation, including but not limited to correspondence emails, chat records, storage media, infringing items and equipment, internal documents and meeting minutes, etc. If the case is transferred to the judicial authority for handling, the relevant evidence should be transferred together.
The act of infringement of trade secrets involves computer technology. If electronic data related to the case is found but cannot be directly extracted on the spot, the relevant computer servers, mainframes, hard disks and other storage devices may be seized, and evidence may be promptly collected through copying, mirroring, video recording, screenshots, data recovery and other means.
Article 29 Where a right holder has filed a commercial secret infringement lawsuit with a people’s court before reporting a complaint to a market supervision and administration department, and the lawsuit has not yet been concluded, the market supervision and administration department may refuse to accept the case.
During the process of investigating and handling a trade secret infringement case, if the right holder simultaneously files a trade secret infringement lawsuit with the People’s Court, the market supervision and management department may suspend the investigation and handling of the case. After the reasons for suspension are eliminated, the case investigation and handling procedure shall be immediately resumed or terminated.
Article 30 If the infringer applies for a patent using the right holder’s trade secret, the market supervision and administration department may copy the administrative penalty results to the intellectual property management department for processing, and the right holder may file a lawsuit with the people’s court and request civil remedies such as compensation for damages.
Article 31 If the market supervision and administration department discovers, based on the evidence collected during investigation and the facts of the case ascertained, that a crime is suspected and that criminal liability needs to be pursued in accordance with the law, it shall promptly transfer the case to the public security organ.
Article 32 Where infringement of trade secrets is found, the market supervision and administration department may, at the request of the party concerned, mediate on the amount of compensation for infringement of trade secrets at the same time as imposing administrative penalties; if mediation fails, the party concerned may sue the people’s court in accordance with the law.
Article 33: State organs and their staff have an obligation to keep confidential commercial secrets that they become aware of in the course of performing their official duties and must not disclose, use or allow others to use the rights holder’s commercial secrets beyond the scope of their duties.
Market supervision and management departments shall not disclose content involving commercial secrets in administrative penalty information.
Chapter VI Legal Liability
Article 34 Any violation of these Regulations that infringes upon trade secrets shall be punished in accordance with the provisions of Article 21 of the Anti-Unfair Competition Law.
Article 35 Any of the following circumstances may be deemed to be a serious circumstance as referred to in Article 21 of the Anti-Unfair Competition Law:
(1) Causing the right holder to suffer property losses of RMB 300,000 or more or causing bankruptcy;
(2) electronic intrusion causes serious damage to the right holder’s office system network and computer data;
(3) Causing major losses to the state or society, or having adverse social impacts;
(4) the infringer refuses to execute the penalty decision and continues to infringe on trade secrets;
(5) Other acts of a serious nature.
Article 36 In accordance with Article 21 of the Anti-Unfair Competition Law, when an infringer is ordered to stop an illegal act, the time limit for ordering the infringer to stop the illegal act shall generally last until the trade secret has become known to the public.
If it is determined in accordance with the provisions of the preceding paragraph that the time for stopping infringement is obviously unreasonable, the market supervision and management department may, while protecting the competitive advantage of the right holder’s trade secret in accordance with the law, order the infringer to stop using the trade secret within a certain period of time or within a certain scope.
Orders to stop illegal conduct include:
(1) ordering the infringer to stop using the right holder’s trade secrets to carry out production and business activities;
(2) order the infringer to return the drawings, software and related materials containing trade secrets to the right holder;
(3) ordering the infringer to destroy the carrier containing the trade secret, unless the right holder agrees to other disposal methods such as purchase or sale;
(4) ordering the infringer to remove the right holder’s commercial secret information under its control;
(5) other orders to stop acts that infringe upon the rights holder’s trade secrets.
Article 37 The illegal gains referred to in Article 21 of the Anti-Unfair Competition Law may be determined in the following ways:
(1) If the infringer obtains the right holder’s trade secret by improper means and then uses it for production, the illegal income shall be calculated based on the total sales revenue of the illegally produced goods minus the purchase price of the raw materials used to produce the goods and the taxes and fees paid;
(2) If the infringer obtains the right holder’s trade secrets by improper means and then uses them to sell goods, the illegal gains shall be calculated based on the total sales revenue of the illegally sold goods, minus the purchase price of the goods sold and taxes paid;
(3) If the infringer obtains the right holder’s business secrets by improper means and then uses them to provide services, the illegal gains shall be calculated based on the total income from the illegal services provided, minus the purchase price of the goods used in the service and the taxes paid;
(4) The money or other property benefits obtained by disclosing or allowing others to use trade secrets shall be deemed as illegal gains.
Article 38: When investigating the losses caused to the right holder by acts of infringement of trade secrets, the market supervision and administration department shall determine the losses in accordance with the actual losses suffered by the right holder due to the infringement. If the actual losses are difficult to calculate, they shall be determined according to the profits obtained by the infringer due to the infringement.
The actual losses suffered due to infringement can be calculated according to the following method:
(1) the product of the right holder whose products have lost sales due to infringement multiplied by the right holder’s reasonable profit for each product;
(2) If the total amount of sales volume reduction caused by the infringement of the right holder is difficult to determine, the amount shall be calculated based on the product of the sales volume of the infringing products multiplied by the reasonable profit of each product of the right holder;
(3) If it is difficult to determine the total amount of sales reduction caused by the infringement and the reasonable profit of each product of the right holder, the product of the sales volume of the infringing products multiplied by the reasonable profit of each infringing product shall be used;
(4) the difference between the expected profit that the infringing product could obtain under normal circumstances and the reasonable profit of the product using the same information after the infringement.
The remedial expenses incurred by the right holder to mitigate losses to business operations or business plans or to restore the security of computer information systems or other systems should be included in the actual losses suffered by the right holder due to infringement.
If a business secret of the right holder is obtained by improper means and has not been disclosed, used or allowed to be used by others, the amount of loss shall be determined based on the reasonable licensing fee of the business secret.
If a trade secret has become known to the public or has been lost due to an infringement of trade secrets, the amount of loss shall be determined by the market value of the trade secret. The market value can be determined based on the research and development costs of the trade secret, the trade secret license fee, the income from the implementation of the trade secret, the evaluation of a third-party market research organization, and the market share encroachment caused by the party’s infringement of the trade secret.
Chapter VII Supplementary Provisions
Article 39: Commercial information as referred to in these Regulations that falls within the scope of state secrets shall be protected in accordance with the provisions of the Law of the People’s Republic of China on Guarding State Secrets.
Commercial secrets that violate laws and regulations and harm national interests and social public interests are not protected by these regulations.
Article 40 Where commercial secrets involve data processing activities, the provisions of data security laws and administrative regulations shall also be complied with.
Article 41 Any act of infringement of commercial secrets committed outside the territory of the People’s Republic of China that disrupts the domestic market competition order or damages the legitimate rights and interests of domestic operators shall be handled in accordance with these Provisions and relevant laws.
Article 42 These Regulations shall enter into force on the date of promulgation, and the former State Administration for Industry and Commerce’s “Several Provisions on Prohibiting Acts of Infringement of Trade Secrets” shall be repealed at the same time.
China’s Supreme People’s Court Releases Summary of the Annual Report on the Application of Law in Intellectual Property Cases (2024) Listing 43 Case-Derived IP Laws
On April 21, 2025, China’s Supreme People’s Court released the Summary of the Annual Report on the Application of Law in Intellectual Property Cases (2024) (全国法院知识产权案件法律适用问题年度报告(2024)摘要) listing 43 laws derived from 2024 IP litigation cases. While China is not a common law country, China’s SPC regularly releases guiding or typical cases as well as these summaries to promote uniformity to help ensure similar cases are treated consistently across different courts.
A translation follows. The original text is available here (Chinese only).
I. Patent Case Trial
1. The characterization of patent evaluation reports in patent infringement disputes
【Case Number】
(2024)最高法民再244号
[Judgment Summary]
In patent infringement disputes, patent evaluation reports can be used as one of the evidences in the trial of the case, but the validity of the patent involved should still be judged based on the patent authorization text and the effective decision of the administrative department [China’s National IP Administration]. In the case where the patent owner files an infringement lawsuit based on a valid patent, it cannot be determined that the patent owner does not have the basis to exercise the right to sue, and then the lawsuit can be dismissed simply because the patent evaluation report makes a negative conclusion that the patent involved does not meet the statutory authorization conditions.
2. Coordination of patent infringement determinations in related cases
【Case Number】
(2023)最高法知民终740号
[Judgment Summary]
For the same alleged infringing products, the same patent rights, and the same grounds for non-infringement defense, the determination of related cases should be consistent to prevent conflicts in judgment. Even if the alleged infringer does not appeal after the first-instance judgment, the second-instance court can also change the judgment and determine that the relevant defense of the alleged infringer is also established based on the determination of the establishment of the same grounds for defense in another effective judgment.
3. Judgment with performance conditions and interest on debt during the period of delayed performance
【Case Number】
(2024)最高法知民终370号
[Judgment Summary]
1. If the patent invalidation procedure is suspended due to property preservation measures being taken against the patent involved, and the National Intellectual Property Administration fails to make a decision on the invalidation request before the judgment of the patent infringement lawsuit, the people’s court may make corresponding arrangements for the performance of the obligations determined by the judgment according to the specific circumstances of the case, including adding necessary conditions to the performance of the judgment items such as cessation of infringement and compensation for losses. For example, the patent claim based on which the patent right holder filed the lawsuit can be made into a precondition for the performance of the judgment item after the National Intellectual Property Administration makes a decision to maintain the validity of the patent claim, and make arrangements for the debt interest during the period, so as to reasonably balance the interests of all parties.
2. For a judgment with attached performance conditions, the debt interest for the period of delayed performance may be ordered at the same time, that is, after the performance conditions of the judgment are met, interest shall be calculated based on the loan market quotation rate for the same period announced by the National Interbank Funding Center from the date of delivery of the effective judgment to the date when the performance conditions are met; if the obligation to pay money is still not performed after the performance conditions determined by the judgment are met, the debt interest for the period of delayed performance shall be doubled.
4. Handling of patent infringement judgments that have been executed after the examination decision declaring patent rights invalid
【Case Number】
(2024)最高法知民再1号
[Judgment Summary]
1. The enforcement actions after the decision to declare a patent right invalid does not fall under the circumstances stipulated in the second paragraph of Article 47 of the Patent Law that the invalidation decision does not have retroactive effect on the effective patent infringement judgment. The relevant enforcement funds should generally be ordered by the enforcement court in the execution reversal procedure to order the applicant for enforcement to return the acquired property and interest to the person subject to enforcement. The people’s court may also order the return in the retrial judgment depending on the circumstances.
2. For patent infringement judgments involving multiple alleged infringers, if the different execution times of the compensation obligations of different alleged infringers result in different application results of Article 47, paragraph 2 of the Patent Law, which violates the principle of fairness, the People’s Court may apply the provisions of Article 47, paragraph 3 of the Patent Law to deal with it.
5. Treatment of a Class I declaration made by a generic drug applicant before patent information registration
【Case Number】
(2023)最高法知民终1593号
[Judgment Summary]
If the drug marketing authorization holder correctly registers the patent information within the prescribed period, but the generic drug applicant has made a Class I statement before the registration, the drug marketing authorization holder should have the opportunity to require the generic drug applicant to promptly apply to change its statement type within a reasonable period. If the generic drug applicant applies to change its Class I statement to a Class IV statement, or refuses to apply for change within a reasonable period, or applies to change to other erroneous statements, the People’s Court shall accept and conduct substantive review of the drug patent linkage lawsuit filed by the patent right holder.
6. Handling of changes in drug technical solutions in drug patent linkage disputes
【Case Number】
(2023)京73民初855号
[Judgment Summary]
In cases of disputes over drug patent linkage, the people’s court shall use the technical solution of the drug review and approval department to determine whether the drug falls within the scope of patent protection. The applicant for drug marketing authorization shall promptly and truthfully explain to the people’s court any changes in the technical solution that affect the judgment of whether it falls within the scope of patent protection, otherwise it shall bear adverse consequences in accordance with the law.
7. Identification of the Inventor of a Utility Patent
【Case Number】
(2022)苏05民初925号
[Judgment Summary]
The invention patent for use is an invention based on the discovery of new uses of known compounds. Its core is not the known compounds themselves, but the discovery and application of new uses of known compounds. If the proposal of the invention concept of “new uses of old drugs” plays a key role in research and development activities, the person who proposes the invention concept, makes substantial contributions to the formation or substantial improvement of specific technical solutions, and makes substantial contributions to phased research and development can be listed as the inventor.
8. Identification of usage environment characteristics and infringement judgment
【Case Number】
(2022)沪73知民初223号
[Judgment Summary]
The identification of the characteristics of the usage environment can be based on the invention title, invention theme, and the claims of the involved patent, combined with the content of the specification for comprehensive judgment. When considering whether the accused technical solution has the relevant usage environment features of the patent claims involved, it is not required that the accused infringing product necessarily has components related to the usage environment features, as long as the accused infringing product can be applicable to the usage environment defined by the usage environment features.
9. Inventions and creations related to sacrificial offerings that violate social ethics and harm public interests should not be granted patent rights
【Case Number】
2023)最高法知行终2号
[Judgment Summary]
1. The patent system is intended to protect inventions and creations that can promote scientific and technological progress and economic and social development. So-called “inventions and creations” that have no substantial benefits for scientific and technological progress and economic and social development should not be protected by patents. The understanding and application of specific provisions, including the first paragraph of Article 5 of the Patent Law, should be based on the legislative purpose stipulated in Article 1 of the Patent Law.
2. In judicial practice, the core socialist values should be used as a guide to advocate and promote social morality that meets the requirements of the times and is recognized by the people. Even if a certain sacrificial product does not belong to feudal superstitious funeral products, it may still fall under the circumstances of violating social morality or harming the public interest as stipulated in Article 5, Paragraph 1 of the Patent Law.
10. Acceptance of deletion amendments to claims during oral proceedings of patent invalidation examination
【Case Number】
(2022)最高法知行终870号
[Judgment Summary]
During the oral hearing of patent invalidation examination, if the National Intellectual Property Administration considers that some of the modified claims are unacceptable, the patentee shall be allowed to delete the unacceptable claims in the current claims text and use the remaining acceptable claims as the basis for examination. Regardless of whether the deletion is proposed orally or in writing by the patentee in court, the National Intellectual Property Administration shall generally accept it; if the replacement page is not submitted in court, the National Intellectual Property Administration may require it to be submitted within a certain period of time; if the replacement page is not submitted within the specified period of time, it can be regarded as the patentee has not modified the claims in accordance with the law, and corresponding treatment shall be made accordingly.
11. Whether the scope of the design for which protection is sought is clearly shown
【Case Number】
(2024)最高法知行终672号
[Judgment Summary]
If, based on the general consumer’s knowledge level and cognitive ability, taking into account the patent views, usage status diagrams and general common sense, there are still multiple possible designs for the design shown in the design patent drawings, then it can be determined that the design patent document fails to clearly show the design of the product for which patent protection is sought.
II. Trial of Trademark Cases
12. Factors to be considered in determining infringement of geographical indication certification trademark rights
【Case Number】
(2024)最高法民再21号
[Judgment Summary]
The following factors need to be considered in determining whether the alleged infringing behavior constitutes an infringement of the geographical indication certification trademark right: first, whether the alleged infringing goods meet the conditions for using the geographical indication trademark, that is, the goods come from a specific place of origin; second, whether the alleged infringing goods have the specific qualities of geographical indication products; and third, whether the alleged infringing behavior is likely to cause confusion and misunderstanding among the relevant public about the source and specific quality of the goods.
13. Determination of the Prior Use Defense of a Trademark
【Case Number】
(2024)最高法民再218号
[Judgment Summary]
The application of the defense of prior use of trademarks requires a balance between the interests of the prior user of the trademark and the exclusive right holder of the registered trademark. If a trademark identical or similar to another person’s registered trademark is used in good faith on the same or similar goods and has a certain influence, the prior user has the right to continue using it within the original scope; if the prior use is earlier than the trademark application date but later than the use time of the trademark registrant, and there is evidence to prove that the prior user knew or should have known, etc., the prior use defense is not established.
14. Determination of legitimate use of scenic spot names
【Case Number】
(2024)最高法民再123号
[Judgment Summary]
If the logo is only used to refer to the name of a scenic spot, or to illustrate and describe the relevant content and characteristics of the scenic spot, and it does not exceed the necessary limits, and the relevant public pays general attention and combines it with daily life experience, and will not be confused about the source of the goods or services, it is a legitimate and reasonable use of the logo and does not constitute trademark infringement.
15. When there is evidence that the infringement has made profits, the amount of damages should be determined based on the profits made.
【Case Number】
(2023)最高法民再178号
[Judgment Summary]
Article 63 of the Trademark Law stipulates the order of application of the calculation method of damages. When determining the amount of damages, the People’s Court should give priority to the actual losses of the right holder, the infringement profits of the infringer and the reasonable license fees as the calculation method. Only when the actual losses, infringement profits and license fees are difficult to determine, the statutory compensation shall be applied.
16. Whether retail services and “selling for others” services constitute similar judgments
【Case Number】
(2022)苏民终356号
[Judgment Summary]
The retail services provided by commodity sellers to end consumers are highly similar to the services of “selling for others” in Class 35 in terms of purpose, content, method and object. In the process of providing retail services, if the unauthorized use of a mark identical to the “selling for others” trademark in Class 35 is likely to cause confusion and misidentification of the relevant public about the source of the services, it shall be deemed to constitute trademark infringement.
17. Calculation of contribution rate and application of punitive damages in pharmaceutical trademark infringement cases
【Case Number】
(2021)苏05民初437号
[Judgment Summary]
1. In cases of pharmaceutical trademark infringement, the contribution rate of the mark in question to the profits of the allegedly infringing drug should be reasonably determined by comprehensively considering the macro development trend of the pharmaceutical field, the micro perspective of consumers in purchasing drugs, the different barriers to entry into a specific pharmaceutical industry, the technical distinction between original research drugs and generic drugs, and the reputation of the pharmaceutical company itself.
2. The alleged infringer, as a shareholder of the right holder and an operator in the same industry, applied for registration of a logo similar to the right holder’s trademark for use on the same goods after the termination of the shareholding relationship, and did not stop the alleged infringement after the administrative judgment had determined that the trademark should be declared invalid. The drugs involved have potential side effects and are easily confused , and the infringement may endanger human health. This is a case of “malicious infringement of trademark exclusive rights with serious circumstances” as stipulated in the Trademark Law, and punitive damages can be applied in accordance with the law.
18. Determination of Distinctiveness of Trademark Registration Based on Product Design
【Case Number】
(2024)最高法行申5449号
[Judgment Summary]
If the applicant of a disputed trademark applied in the form of a product trade dress does not provide sufficient evidence to prove that, through its actual use, the relevant public has been able to use the disputed trademark as a mark for identifying the source of goods rather than merely as a product design, then the disputed trademark does not have distinctive features.
19. Determination of whether trademark registration infringes upon the prior domain name rights of others
【Case Number】
(2024)最高法行再244号
[Judgment Summary]
To determine that the registration of the disputed trademark infringes on the prior domain name rights of others, the following conditions must be met at the same time: the domain name was registered first and has a certain degree of popularity, the goods or services provided by the domain name operator are the same or similar to the goods or services approved for use by the disputed trademark, and the disputed trademark is the same or similar to the domain name, which is likely to cause confusion and misunderstanding among the relevant public. The publicity and use evidence of the goods or services provided by the domain name operator can be used as the factual basis for determining whether it has a certain degree of popularity.
20. Application of Article 44 of the Trademark Law: “Obtaining registration by other unfair means”
【Case Number】
(2024)最高法行再88号
[Judgment Summary]
When judging whether a disputed trademark falls under the circumstance of “obtaining registration by other improper means” as provided for in Article 44, Paragraph 1 of the Trademark Law, it is not appropriate to determine that a trademark applicant has “obtained registration by other improper means” simply because the number of trademark applications has reached a certain scale. For applicants who can prove that they have a genuine intention to use the disputed trademark or have actually put the trademark into commercial use, and that the application for the disputed trademark is reasonable or legitimate, it is generally not appropriate to determine that the disputed trademark falls under the circumstance referred to in this article.
21. Determination of the approved goods for use in the case of cancellation of trademark due to non-use for three consecutive years
【Case Number】
(2024)最高法行再51号
[Judgment Summary]
If the goods actually used for the disputed trademark do not belong to the standardized product names in the “Classification of Similar Goods and Services”, but they are essentially the same goods as the goods approved for use by the trademark, or the goods actually used belong to a subspecies of the approved goods, it can be determined that it constitutes the use of the approved goods. If the “Classification of Similar Goods and Services” changes after the disputed trademark is registered, it will not affect the above determination.
22. Determination of whether the behavior of the game live broadcast platform constitutes “marketing for others” service
【Case Number】
(2024)京行终6099号
[Judgment Summary]
The game live streaming platform takes advantage of its own traffic and user resources to promote and advertise the partner games through game live streaming, providing game downloads and forums, organizing promotional activities, etc., thereby increasing the download and in-game purchase volume of the partner games, and thereby obtaining a share of the game revenue. This behavior can be deemed to be providing planning and publicity for the sale of goods or services for others, constituting Category 35 of the “Classification Table of Similar Goods and Services” “sales promotion for others” service.
III. Trial of Copyright Cases
23. Works of applied art can be protected by copyright law as works of fine art
【Case Number】
(2023)最高法民再40号
[Judgment Summary]
For shapes or designs that may be both practical and artistic, parties may choose to protect them under copyright law or design patents, with different protection focuses. When claiming copyright protection, according to the existing system arrangement of China’s copyright law, it is necessary to judge whether the claimed work meets the formal requirements of works of art and whether it has the substantive requirements of originality. There is no need to establish a separate type of work other than works of art, nor is there a need to make separate requirements for originality.
24. Exhaustion of the right to distribute computer software
【Case Number】
(2022)最高法知民终1460号
[Judgment Summary]
1. If computer software must be used in conjunction with specific hardware, the right holder’s sale of hardware and computer software in conjunction with each other can be regarded as the distribution of software in the form of delivering tangible carriers, and the principle of exhaustion of distribution rights can be applied as appropriate. After paying a reasonable price, the buyer obtains the ownership of the original or copy of the corresponding software and has the right to use it himself or transfer it to others for use. The right holder’s restrictions on the scope of use, resale, etc. of the aforementioned software are not necessarily binding on the buyer with no contractual relationship with him and the third party who legally transfers the original or copy of the software from the buyer. However, the buyer or third party shall not copy the software without authorization, except for the purpose of achieving legal use, nor shall they use the copy of the software after transferring the original or copy of the software.
2. The owner of a legal copy of software is prohibited from providing the modified software to any third party without permission, which mainly refers to the situation where the modified software cannot be used as the main subject of the transaction without the permission of the software copyright owner. If the main subject of the transaction is hardware, and the software is only used in conjunction with the hardware, and the ownership of the modified software is transferred together with the transaction of the matching hardware, it is generally not necessary to obtain the permission of the software copyright owner.
25. Determination of Substantial Similarity between Works of Art
【Case Number】
(2019)京73民初1376号
[Judgment Summary]
When judging whether a work of art is substantially similar, the visual image characteristics of the work of art should usually be considered from the perspective of an ordinary observer, and the artistic expression embodied in the work of art should be identified and comprehensively judged in terms of constituent elements, forms of expression, and overall visual effects. If there are only slight differences between the two as a whole, so that ordinary observers tend to ignore these differences unless they deliberately look for differences, then the two can be deemed to be substantially similar. In the case where there are a large number of both the rightholder’s paintings and the infringing paintings being compared, all the paintings involved can be considered as a whole, and at the same time, a comprehensive judgment can be made based on factors such as the author’s creative experience, creative methods, and creative style to determine whether infringement has occurred.
26. Determination of whether a screenwriter has the right to be credited if he quits writing a film or TV script midway
【Case Number】
(2020)京0108民初39696号
[Judgment Summary]
Whether a screenwriter who quits writing a screenplay for a film or TV work midway can enjoy the screenwriter’s right of authorship for the film or TV work should be judged comprehensively based on the provisions of the screenwriter contract signed by the screenwriter, whether the film or TV work uses the original content of the screenwriter’s script, and whether the proportion of use has made a substantial contribution to the film or TV work. If the screenwriter contract does not clearly stipulate the exercise of the screenwriter’s right of authorship after termination, if the proportion of the original content of the screenwriter’s script created by the screenwriter in the film or TV work reaches the level of substantial contribution to the film or TV work, the screenwriter should be deemed to enjoy the screenwriter’s right of authorship.
27. Determination of copyright infringement by the content provider of the in-vehicle system
【Case Number】
(2023)京0491民初11731号
[Judgment Summary]
The video platform operator shall bear the liability for infringement of the information network dissemination right for the provision of infringing videos on its vehicle-mounted application network server. The operator of the vehicle-mounted system software participated in the launch, display and promotion of the video platform vehicle-mounted application and provided package services. It is a participant and beneficiary of the provision of the works involved in the case and shall bear joint and several liability with the video platform in accordance with the law.
28. Implementing algorithmic unified aggregation behavior to increase the duty of care of network service providers
【Case Number】
(2022)沪0115民初29412号
[Judgment Summary]
In determining whether a video sharing platform constitutes copyright infringement or aiding and abetting infringement, it is important to distinguish between the neutrality of the technology itself and the non-neutrality of the technology application. The platform organizes a large number of infringing short videos into a certain topic and category based on the copyrighted works, and then presents them to all users in a unified manner, which contains the subjective intention of the platform. The implementation of this algorithmic unified aggregation behavior will increase the duty of care of network service providers, and thus affects the determination of whether it constitutes knowledge.
29. Determination of infringement liability of generative artificial intelligence service providers
【Case Number】
一审:(2024)浙0192民初1587号
二审:(2024)浙01民终10332号
[Judgment Summary]
1. When a service provider provides generative artificial intelligence technology services, whether it constitutes contributory infringement should take into account factors such as the service provider’s profit model, the popularity and influence of the copyrighted work, the obviousness of the infringement, the level of development of artificial intelligence technology, the feasibility and cost of alternative designs to avoid damage, the necessary measures that can be taken and their effects, and the impact of the assumption of infringement liability on the industry. The fault identification standard should be dynamically adjusted to control the service provider’s duty of care to a reasonable level that is commensurate with its information management capabilities.
2. Generative AI services are only subject to anti-unfair competition law when they violate the principles of good faith and recognized business ethics, disrupt the market competition order, and damage the legitimate rights and interests of other operators or consumers.
30. Determination of Direct Infringement and Necessary Measures Taken by Cloud Storage Service Providers
【Case Number】
(2022)粤民再59号
[Judgment Summary]
1. The “same file merge storage” technology adopted by cloud storage service providers does not change the source of the work. To determine whether the cloud storage service provider has replaced third-party providers in providing downloaded works to users, it is necessary to investigate whether there is any real transmission of work content data between the cloud disk and third-party network nodes during the download process. The content data of the work is completely transmitted from third-party network nodes to the cloud , which is a downloading tool and does not constitute a direct infringement of the network dissemination right of the work information.2. For the behavior of users sharing infringing works, cloud storage service providers should take necessary measures to prevent the continuation of the infringing behavior, prevent other behaviors similar to the infringing behavior, and prevent the occurrence of behaviors similar to the infringing behavior. For unpopular works with minor infringement, disconnecting the infringing link and blocking the “sharing” function of the file pointed to by the infringing link can basically achieve the aforementioned prevention and control effects.
IV. Competition Case Trials
31. Identification of corporate names with certain influence
【Case Number】
(2023)最高法民终418号
[Judgment Summary]
To determine whether it constitutes a “trade name with a certain influence” as stipulated in Article 6, Paragraph 2 of the Anti-Unfair Competition Law, the starting time of the use of the alleged infringing trade name should be used as the benchmark, and the degree of awareness of the relevant public in China, the time, region, amount and target of product sales, the duration, degree and geographical scope of publicity, the protection of the logo, etc. should be considered. If the accused infringer is aware of the prior use of the trade name by others, it can be deemed that the market reputation of the prior trade name has reached the accused infringer.
32. Overall judgment of infringement of technical secrets and specific assumption of civil liability for stopping infringement
【Case Number】
(2023)最高法知民终1590号
[Judgment Summary]
1. For the alleged infringement of technical secrets caused by organized, planned, and large-scale poaching of personnel and technical resources of other enterprises, the people’s court shall make an overall analysis and comprehensive judgment during the trial. If the alleged infringer produces products related to the technical secrets involved in a time that is obviously shorter than the reasonable time required for independent research and development, and the alleged infringer has channels or opportunities to obtain the technical secrets involved, at this time, due to the great possibility of infringement, the burden of proof of the infringement of technical secrets by the technical secret right holder should be further reduced, and it should be directly presumed that the alleged infringer has committed acts of infringing the right holder’s technical secrets. If the alleged infringer denies that he has committed acts of infringing technical secrets, he shall provide evidence to refute it.
2. In order to effectively stop and deter infringement and enhance the enforceability of judgments, the People’s Court may, when determining the specific manner of assuming civil liability for ceasing infringement, determine the specific manner, content and scope of ceasing infringement based on the specific claims of the right holder for the liability to ceasing infringement, or, if necessary, directly determine the specific manner, content and scope of ceasing infringement ex officio; it shall, on the basis of fully considering the nature of the protected rights and interests and the severity of the infringement, especially the actual harmful status of the infringement and the possibility of continued infringement in the future, focus on considering factors such as the necessity, rationality and enforceability of taking relevant specific measures to protect such rights and interests.
3. According to the specific circumstances of the case, specific measures to stop infringement of technical secrets may include: stop using the technical secrets involved to manufacture related products by oneself or entrust others to manufacture related products, stop selling related products manufactured using the technical secrets involved; without the consent of the real right holder, the infringer shall not implement, authorize others to implement, transfer, pledge or otherwise dispose of the relevant patents applied for using the illegally obtained technical secrets involved, including malicious abandonment of patent rights; destroy the relevant carriers containing the technical secrets involved held or controlled by the infringer and relevant units and personnel under the supervision of the People’s Court or witnessed by the right holder, or hand them over to the technical secret right holder; announce and/or in the form of an internal notice, notify the company’s shareholders, senior management, relevant employees, affiliated companies and upstream and downstream manufacturers who may have learned the technical secrets involved in the case, etc. to actively cooperate in fulfilling the requirements of the People’s Court’s judgment to stop infringement, and provide clear guidance on the internal intellectual property compliance operation of the company; notify the relevant requirements to stop infringement one by one to the relevant employees who resigned from the technical secret right holder to work for the infringer and its affiliated companies, all other personnel of the infringer and its affiliated companies who are responsible for or involved in related research and development work (including relevant senior management), and upstream and downstream manufacturers who may have learned the technical secrets involved, and sign a letter of commitment with them to keep the commercial secrets involved and not to infringe.
4. In order to ensure that the judgment is executed in a timely and comprehensive manner, the people’s court may, based on the specific circumstances of the case, comprehensively consider the nature and circumstances of the infringement, the possible damages and negative impacts caused by the violation of non-monetary payment obligations such as cessation of infringement, as well as factors such as enhancing the deterrent effect of the judgment, and clarify the calculation standards for the delayed performance of non-monetary payment obligations involved in the judgment. The relevant payment standards may be calculated on a daily or monthly basis or as a one-time fixed amount depending on the circumstances.
33. Determination of Trade Secret Infringement and Infringement Liability
【Case Number】
(2022)最高法知民终1592号
[Judgment Summary]
1. If the alleged infringer has illegally obtained and used trade secrets based on his prior acts of infringing trade secrets, and the evidence submitted by the right holder can preliminarily prove that the alleged infringer has committed acts again, and the alleged infringer cannot submit sufficient evidence to refute it, the right holder’s claim that the alleged infringer continues to commit acts of infringing trade secrets can be deemed valid.
2. If an employee sets up a company and participates in acts that infringe on trade secrets by means of hidden shareholding by a third party such as his/her spouse while serving in the original company, the employee and the company shall constitute joint infringement and shall bear joint liability.
3. If computer software and specific data have a unique corresponding relationship and the two cannot be used separately, and the existing evidence is sufficient to determine that the alleged infringer has used the specific data, then it can be determined that he has also used the computer software at the same time.
4. If there is no evidence to prove that the right holder neglected to assert his rights or condoned the infringement, the people’s court will not support the alleged infringer’s claim that only the infringement damages within three years before the lawsuit should be calculated on the grounds of the statute of limitations.
34. Determination of the Improper Behavior of Ticket Grabbing Software
【Case Number】
(2024)京0101民初4607号
[Judgment Summary]
Ticket-grabbing software uses technical means to provide users of the target platform with unfair ticket-grabbing advantages, which undermines the platform’s ticket purchasing rules and damages the platform’s competitive interests. It also damages the legitimate rights and long-term interests of consumers and disrupts the fair competition market order. It should be deemed to constitute unfair competition.
35. Determination of improper use of data
【Case Number】
(2023)沪0114民初13000号
[Judgment Summary]
The right holder obtains the consent of the user to collect, use, organize and store relevant information, and aggregates and forms a data set based on platform user information and work content information. It enjoys property rights including legal control, use, and operation of the relevant data. The accused infringer illegally obtains non-public data through technical means and displays it on a self-operated website, thereby conducting paid transaction services. The way it obtains and uses such data exceeds reasonable limits and violates business ethics, disrupts the market competition order, and is improper.
36. Determination of the non-public nature of technical secrets
【Case Number】
(2022)鄂01知民初707号
[Judgment Summary]
Each single step or part of the parameters of the technical information already exists in the public domain, but the overall technical solution of multiple steps and parameters is not well known in the industry, and can still be protected as a technical secret. Whether it constitutes a technical secret should be strictly examined based on the elements of the technical secret, rather than judging by the evaluation standards of the novelty and creativity of the technical solution in the patent law.
37. Criteria for determining whether a technology neutrality defense is established
【Case Number】
(2024)渝0192民初2546号
[Judgment Summary]
In cases of unfair competition disputes on the Internet, if the operator uses technology neutrality as a defense, the judgment criteria should be whether the use of technology is legitimate and whether it has a substantial non-infringing purpose. The use of neutral technology that breaks the will of network platform users and bypasses the technical settings of the network platform is unfair; the operator should prove that it has a substantial non-infringing purpose, otherwise it should be deemed to have subjective fault and bear the corresponding infringement liability.
38. [Omitted as pertains to antirust]
39. [Omitted as pertains to antirust]
V. Trial of Cases Concerning New Plant Varieties
40. Burden of proof of variety identity and review of identification methods
【Case Number】
(2022)最高法知民终1362号
[Judgment Summary]
1. When conducting identity identification or testing of the authorized variety and the alleged infringing variety, the variety right holder shall try his best and to diligently provide evidence for the samples of the alleged infringing variety to be tested and the control samples of the authorized variety used for identification or testing, and exercise reasonable care to ensure that the sources are clear, the storage is standardized, the inspection process is authentic and reliable, and that the identification or testing requirements are met.
2. In cases involving infringement of new plant variety rights, the people’s court shall review whether the molecular marker method for variety identity identification is scientific and reliable. If there is no national standard or industry standard for the molecular marker detection method of a specific plant variety, the identification agency and appraiser with corresponding qualifications shall make an identification opinion by referring to other relevant national standards and industry standards. If the identification method can scientifically and accurately distinguish different varieties and has sufficient scientific basis and repeatability, the identification opinion can be used as one of the evidences to determine whether the characteristics and properties of the alleged infringing object are the same as those of the authorized variety.
VI. Trial of Integrated Circuit Layout-Design Cases
41. Identification of protected objects of layout designs and those that have been put into commercial use
【Case Number】
(2022)最高法知民终2133号
[Judgment Summary]
1. Although the layout design does not contain source components, it shows the three-dimensional configuration relationship between active components and circuits, which can clarify their interfaces with active components, and can achieve corresponding circuit functions when using other standardized components. It can be considered that the layout design belongs to the “three-dimensional configuration of at least two or more components that are active components and partially or completely interconnected circuits”, and is the object protected by the exclusive rights of layout design.2. After the completion of the layout design, it is necessary to conduct testing and verification of performance through tape-out. However, if the number and quantities of chips containing the layout design manufactured significantly exceed the amount needed for tape-out, the claim of the right holder that the layout design has not been put into commercial use will not be supported in the absence of contrary evidence.
VII. Intellectual Property Litigation Procedure and Evidence
42. Transfer of jurisdiction should be subject to the limitation of response jurisdiction
【Case Number】
(2024)最高法民辖152号
[Judgment Summary]
Except for violations of hierarchical jurisdiction and exclusive jurisdiction, if the parties do not raise any objection to jurisdiction and respond to the lawsuit, even if the court believes that it has no jurisdiction, it should not transfer the case.
43. Conditions for Issuance of an Anti-injunction (Enforcement) Order
【Case Number】
(2024)最高法知民终914、915号
[Judgment Summary]
If a standards implementer applies to a foreign court for an injunction (enforcement) order against a patent infringement lawsuit filed by a standard essential patent owner in a Chinese court, and the standard essential patent owner files an application for a counter-injunction (enforcement) order with the Chinese court hearing the patent infringement lawsuit, and the People’s Court, after preliminary review, finds that the standard essential patent owner has fulfilled its fair, reasonable and non-discriminatory licensing commitments in the licensing negotiations, and that the standard implementer has obvious faults in the licensing negotiations and intends to improperly hinder the standard essential patent owner from exercising its due process rights to promote case trial and judgment enforcement in the Chinese court, the application for a counter-injunction (enforcement) order filed by the standard essential patent owner may be approved in accordance with the law.
Could This be the Ai-nswer? A Collective Copyright Licence for Generative AI Training
The Copyright Licensing Agency (CLA), a United Kingdom (UK) not-for-profit, has announced that it is developing a Generative AI (GenAI) Training Licence, and is hoping to publish the licence in the third quarter of 2025.
Why does this matter?
One of the most hotly debated issues surrounding GenAI is how to train AI models, and how to balance the very real concerns of creators and the necessary flexibility for developers to encourage true innovation.
Promoted as “groundbreaking” and a “milestone initiative”, the aim of this licence is a scalable collective licensing solution similar to other copyright collection societies. This licence looks to find that difficult balance by guaranteeing compensation and remuneration for publishers and authors, and by providing developers with legal certainty and material to train models.
Who does it involve?
Alongside the CLA, the Publishers’ Licensing Services (PLS) and the Authors’ Licensing and Collecting Society (ALCS) are also involved in this ambitious development. PLS is a non-profit collective management organisation, owned by the four main UK publishing trade associations and representing 4,500 publishers in the UK, and its aim is to maximise the value and returns of published content through collective licensing. ALCS is a not-for-profit organisation with 125,000 members that works for the benefit of all types of writers, and collects money for secondary uses of writers’ work.
Could this be the AI-nswer?
It might just be. Collective licensing has been proven to work well in a number of industries. By simplifying access to the massive amounts of data necessary to train GenAI models, and streamlining the process to ensure that all creators receive fair compensation for the use of their works, this licence allows legal certainty and protection for both parties.
It also allows smaller creators to obtain benefit from the language training where they may have missed out due to their lack of bargaining power. It could also slow the already accumulating number of cases bubbling away around the world on this very topic.
The availability of these types of licences will also likely alter the risk profile for transactions involving AI systems in the UK and internationally, which to date have had to proceed without adequate measures to address third party copyright litigation risk.
France’s Limagrain Wins Highest Chinese Damages Ever for New Plant Varieties Infringement – Over 53 Million RMB
On April 25, 2025, China’s Intellectual Property Court of the Supreme People’s Court (SPC) announced a verdict favoring Limagrain’s Chinese affiliate Heng XX Seed Industry Co., Ltd. against Henan Jin XX Seed Industry Co., Ltd. The SPC awarded Limagrain’s affiliate over 53 million RMB and an injunction for infringing new corn plant variety “NP01154” overturning the lower court’s decision and applying punitive damages. This is believed to be the highest ever award in China for new plant varieties infringement.
Heng XX Company filed a lawsuit with the first instance court, claiming that the seven approved corn hybrid varieties produced and sold by Jin XX Company, including “Zheng Pinyu 491”, “Jinyuanyu 304”, “Jinyuanyu 171”, “Zheng Pinyu 597”, “Jinyuanyu 181”, “Zhengyuanyu 777” and “Zhengyuanyu 887”, were all produced without permission using the “NP01154” variety as a parent, and requested that it be ordered to stop the infringement, apply punitive damages of 160 million RMB and pay 200,000 RMB for reasonable expenses for rights protection. In the first instance, Heng XX Company submitted four test reports to prove that the number of difference sites between the parents of the alleged infringing variety “YZ320” and “NP01154” was 1, and therefore was infringing; Jin XX Company submitted test report No. 2994 and claimed that there were differences in 4 of the 5 additional test sites, and the two were different varieties, so it did not constitute infringement. The first instance court accepted the test report No. 2994 submitted by Jin XX Company, determined that the parent of the alleged infringing variety “YZ320” and the authorized variety “NP01154” were different varieties, and ruled to dismiss all the claims of Heng XX Company. Heng XX Company appealed.
The focus of the second-instance dispute was whether Jin XX infringed the variety rights of “NP01154” and the determination of infringement liability, which mainly involved whether the parents (paternal parents) of the seven hybrid corn varieties accused of infringement were identical to the authorized variety “NP01154”. In particular, when using molecular markers to determine the identity of the variety, the conditions for expanding the site testing and the probative value of the additional testing results were the key issues in this case.
The Supreme People’s Court held that there was insufficient evidence to prove that the five additional test sites in the No. 2994 test report were generally recognized specific sites that could distinguish different varieties. The report’s initiation of the expanded site testing procedure and the selection of additional test sites did not comply with the provisions of the relevant judicial interpretations and the requirements of the molecular marker testing standards for new plant varieties, and had no probative value. Jin XX’s claim that its allegedly infringing variety was “glutinous” corn and that the authorized variety “NP01154” was “ordinary corn” and that the two were different varieties lacked evidence. The evidence in this case can prove that the parents (father) of the seven hybrid corn varieties accused of infringement are identical to the authorized varieties, and Jin XX’s behavior constitutes infringement of the “NP01154” variety rights; Jin XX’s company intentionally infringed, and the infringing products involve 7 approved hybrid varieties, the infringement period is as long as five years, and the infringing production area is as high as 8243.4 acres. The infringement is serious, and punitive damages should be applied, and the multiple of punitive damages is determined to be 1X, and then the total compensation is determined to be twice the amount of compensatory damages, that is, more than 53.347 million RMB. In view of the complexity of the case and the evidence, Heng XX’s attorney fees, testing fees, travel expenses and other expenses are reasonable, and the reasonable expenses of 200,000 RMB for rights protection are fully supported. The final compensation amount in this case is 53,547,163.1 RMB.
The original text of the announcement is available here (Chinese only).